VMware and the Essential Eight
Introduction
The Australian Cyber Security Centre (ACSC) Essential Eight Maturity Model has been provided as a set of key cyber principles to implement in any organisation.
VMware has extensive experience with the Essential Eight Maturity Model and supports many customers in Australia who are required to comply with the Essential Eight. This paper explains which VMware products can be used to meet the Essential Eight, and provides practical guidance and advice on how to achieve effective security outcomes in each of the eight areas of focus.
VMware recommends that organisations should focus their effort on achieving the intended security outcome for each of the Essential Eight controls, rather than focusing only on the specific methods that are discussed in the Maturity Model documentation. A focus on outcomes will help to ensure that the organisation achieves the risk-reduction objectives of the Essential Eight, and can effectively justify the control approach to auditors if the Essential Eight maturity levels are being formally assessed.
Purpose
This whitepaper provides an overview of VMware’s guidance in relation to the ACSC Essential Eight Maturity Model, and where this is relevant across all VMware products.
VMware product specialist teams can provide more detailed information on how to configure a specific VMware product (such as Carbon Black App Control or Workspace ONE UEM) to meet each maturity level for one of the Essential Eight areas of focus.
Audience
This paper is intended for IT and security teams within Australian organisations that are required to apply the Essential Eight Maturity Model. Some familiarity is expected with IT management practices in medium- and large-sized organisations, but the paper does not assume deep technical knowledge of VMware products. The paper is intended to provide a broad perspective that informs people who are considering their options to meet the Essential Eight maturity levels.
Context
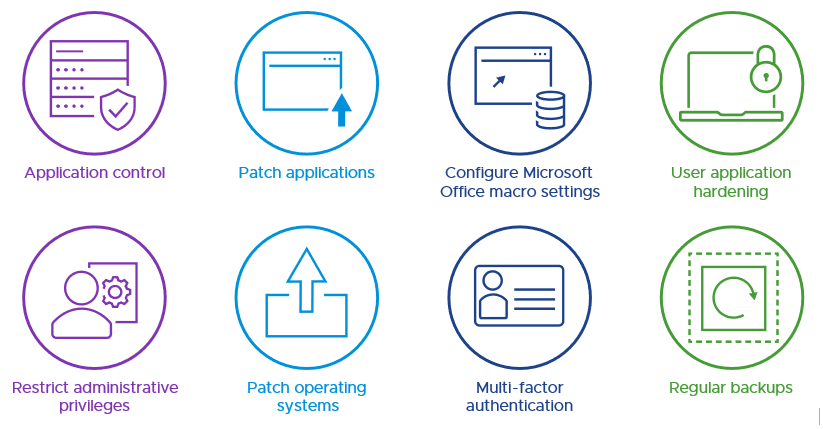
Figure 1: The ACSC Essential Eight
We acknowledge the important work of the ACSC in publishing Strategies to Mitigate Cyber Security Incidents since 2010, with the most recent release being in 2017. In 2017, the ACSC first published the Essential Eight, which is a subset of eight prioritised mitigation strategies from the broader document.
The Essential Eight is primarily intended for protecting Microsoft Windows-based internet-connected networks, although its principles apply to non-Windows environments. The supporting Essential Eight Maturity Model has been regularly updated – most recently in November 2022 – to provide more detailed guidance about how to progressively implement the Essential Eight.
VMware alignment with the Essential Eight
The following figure shows a high-level view of VMware solutions and their support for each of the Essential Eight maturity levels:
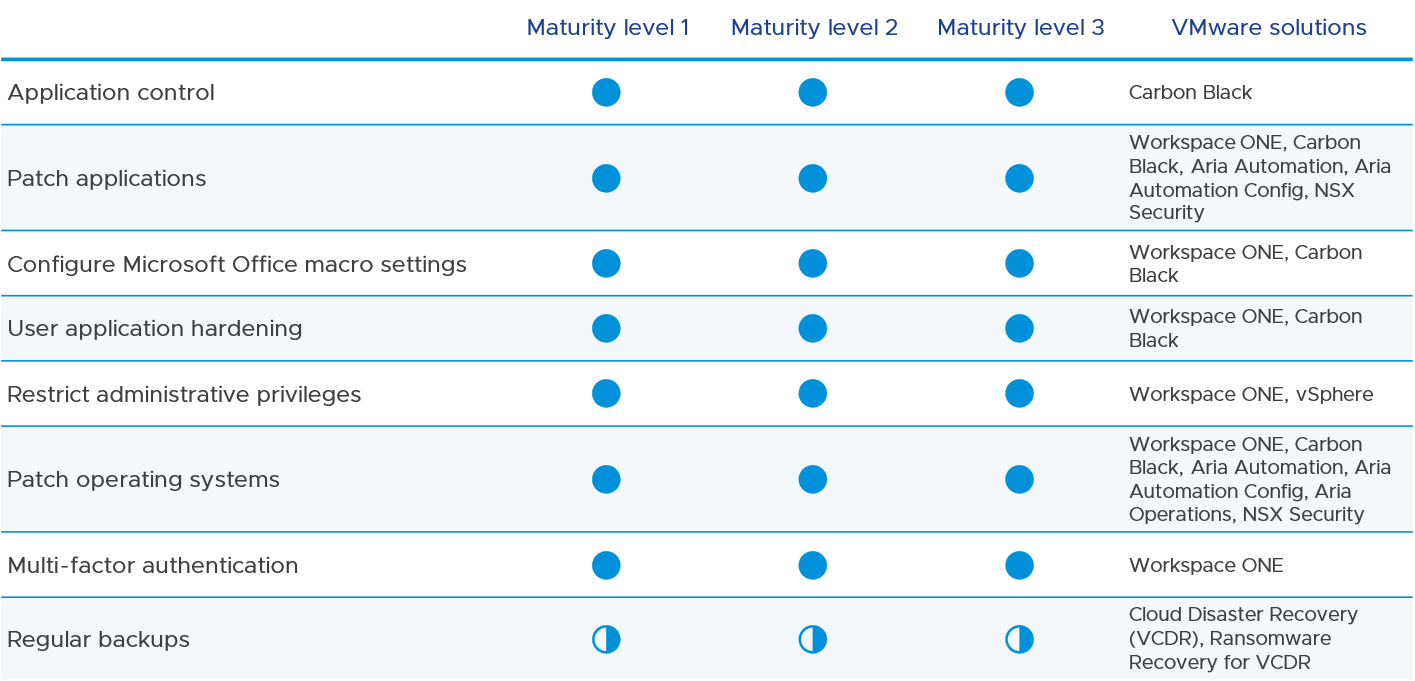
Figure 2: VMware solutions and their alignment to the Essential Eight
The following sections provide further details for each of the Essential Eight control areas, with our perspective on how to address each control area and the relevant VMware solutions that apply.
Application control

The general objective of this control is that only specifically authorised applications are approved to run on workstations and servers, with all other executable code being blocked. This is to decrease the risks of attacks such as ransomware, where unauthorised malicious code is run on a device.
Product capabilities – end-user computers, servers, and workloads
VMware Carbon Black App Control is a market-leading application control product which can be used to meet all Essential Eight maturity levels for application control. Carbon Black App Control has unique flexibility and fine-grained control and is trusted by Google, Netflix, and Aramco, as well as government, defence, and critical infrastructure organisations around the world. It also has very broad operating system (OS) support with coverage of many versions of Windows, MacOS, and Linux.
Many standard antivirus and endpoint protection products have basic application control functionality to block the execution of unexpected software, but lack important functions to make application control practical at scale (such as workflow management of software changes). Carbon Black App Control provides excellent manageability that supports permitted changes and application deployments. For example, Carbon Black App Control trust and approval mechanisms allow for the automated approval of patches from update mechanisms and sources that are used by an organisation. This capability is extremely important for the practical implementation of the patching requirements within the Essential Eight – especially the requirements for urgent patches to be applied within 48 hours.
VMware guidance – end-user computers
Application control is easiest to enforce for computers that have few changes to their software and Carbon Black App Control helps organisations to achieve up to maturity level three.
For many organisations, it is extremely challenging to implement application control for workstations, due to the high frequency of software changes on these devices. As a result, most organisations do not implement application whitelisting. Developer workstations and development environments in general are particularly challenging, and application control may not be practical. A stronger focus on modern endpoint protection products may be more realistic and effective than allow-lists. Examples include Endpoint Detection and Response (EDR) tools which enforce behaviour-based protection, such as Carbon Black EDR or Carbon Black Cloud on workstations, or Workspace ONE Mobile Threat Defence (MTD) on mobile devices.
Workspace ONE Unified Endpoint Management (UEM) is used by organisations to manage workstations and mobile devices, including delivery of managed applications on those devices. Workspace ONE UEM uses built-in operating system functionality to control which applications can be used. Note that the Essential Eight only considers workstations and servers.
A combination of Workspace ONE UEM profiles and baselines can be used to apply some effective application restrictions. Dynamic Environment Manager (DEM) integrates with Workspace ONE UEM to enable applications from approved vendors to install with privileged access, so that most end users can effectively work without needing elevated or privileged access.
VMware guidance – servers and workloads
Servers are usually relatively straightforward for application control because changes and updates are strictly controlled. Application control on servers is part of Maturity Level Three, although high-risk servers (such as Internet-facing servers) are a more important priority and are included in Maturity Level Two.
NSX Security can be used to enforce network segmentation of workloads that run in a software-defined data centre (SDDC) such as vSphere, VMware Cloud Foundation (VCF), or VMware Cloud. NSX network security policies can be applied using tags and Layer 7 Application IDs to limit which applications are accessible across the network. NSX micro segmentation can be used to limit the attack surface by allowing only approved applications to be accessed on specific workloads. Although a micro segmentation approach does not fit the ACSC’s definition of application control and cannot be used to comply with the Essential Eight, it does meet some of the intent of application control and can be used to significantly reduce security risk for important workloads.
Patch applications

The general objective of this control is for application vulnerabilities on workstations and servers to be addressed through patching.
Unfortunately, application patching is complex, with enormous and very different challenges for both workstation and server applications. Most organisations struggle with the volume of patching required, and with prioritising the work. VMware recognises that 100% compliance to patching is further complicated by production outages that may be required. We suggest that a better approach to application patching is to:
- Patch publicly accessible applications as a top priority
- Patch business-critical applications urgently – despite the inevitable integration complexity
- Patch any application that stores sensitive data immediately, including personally identifiable information
- Factor in government advice about vulnerabilities that are commonly exploited in attacks (such as advisories from ACSC, or the Known Exploited Vulnerabilities Catalog from the US Cybersecurity and Infrastructure Security Agency)
- Require that the organisation accepts the risk associated by not patching, if the organisation pushes back to patch an application
- Require that all organisations adopt a mature patching policy that considers patch severity, business operational needs and cyber risk appetite. It is critical that this is accepted by the organisation, the CISO and the Risk leader of the organisation.
Product capabilities – end-user computers
Workspace ONE UEM is used by organisations to deliver application patches to relevant workstations such as Windows and Mac computers, and mobile devices. Workspace ONE UEM is fully featured for managing application patches and can be used to meet all Essential Eight maturity levels.
Workspace ONE MTD is used by organisations to provide device, network, application, and phishing protection for mobile operating systems such as iOS, iPadOS, Android, and Chrome OS, as well as to provide integration with Workspace ONE UEM. For BYOD or organisation-owned devices, Workspace ONE MTD can identify missing app versions or apps which have exploitable vulnerabilities or malware, while integrating with Workspace ONE UEM and Workspace ONE Intelligence for automated response and enforcement of policy.
Workspace ONE Intelligence can be used to further enhance management of application lifecycle and OS vulnerability management by giving near real-time data on application usage and automating responses to a failed patch installation or detected vulnerabilities.
Product capabilities – end-user computers, servers, and workloads
Carbon Black Cloud provides vulnerability management information for known operating system and application vulnerabilities. Carbon Black App Control provides a near real-time application and file inventory of every endpoint, which can also be used to identify computers that require patching.
Product capabilities – servers and workloads
VMware Aria provides a single platform with multi-cloud management capabilities, which spans VMware’s previous vRealize, CloudHealth, and Tanzu Observability offerings.
Aria Automation (formerly vRealize Automation) provides powerful infrastructure automation across clouds and data centres, and is frequently used for deploying application patches on server workloads using DevOps processes.
Aria Automation Config (formerly vRealize Automation SaltStack Config) is a software configuration automation tool that extends Aria Automation with rich guardrails functionality, to ensure that cloud and data centre workloads meet a desired configuration state. It is commonly used to automate the deployment and enforcement of application patches for server workloads. Workload application patches can also be automated with fast, scalable, event-driven orchestration using Aria Automation for Secure Hosts (formerly vRealize Automation SaltStack SecOps).
NSX Security provides extensive network security functionality that can be applied flexibly for server workloads that are part of a software-defined data centre (SDDC). NSX Security includes network intrusion prevention service (IPS) functions that can be enabled to protect workloads from known network attacks. Virtual patching functions can be integrated with the network IPS using NSX Advanced Threat Prevention and virtual patching is also available as part of the Web Application Firewall (WAF) services within NSX Advanced Load Balancer. These network-based protection capabilities can be used to provide protection for workloads with known vulnerabilities that cannot be patched immediately.
VMware guidance – end-user computers
The Modern Management approach to patching for end-user devices is based on deployment rings, so that new patches are automatically deployed on increasing numbers of devices. This approach enables patches to be released quickly without the bottleneck of formal user acceptance testing, while the progressive rollout allows early deployment waves that affect small sets of sample staff to detect problematic patches, so that a deployment can be stopped before too many devices are affected. Workspace ONE UEM readily supports modern management approaches to application patching.
The dynamic nature of workstation environments means that it is usually difficult to achieve high patching compliance for workstation applications. This can be improved using products such as Workspace ONE UEM which provide accurate and up-to-date visibility of whether patch deployments on devices were successful or automating remediation of failed patch installations.
VMware guidance – servers and workloads
The modern DevOps approach to server management involves an Infrastructure-as-Code model where server workloads are always deployed with the latest updates for all applications. When an application update becomes available, this is included in the code pipeline and new workloads are deployed with the updated software while old workloads are removed. This operational model means that in-place patching of workloads is no longer required.
Organisations that use Kubernetes-based container images to deploy and manage applications will generally establish DevOps code pipelines for their container images. Tanzu Application Platform can be used by developers to simplify and automate their development processes with Kubernetes management, and it includes Tanzu Build Services to automate source-to-container workflows. This ensures that updates for key source images can be included automatically into containers when they are packaged.
Application patching for traditional server environments is often challenging because regression testing is necessary but can be complex and time consuming. It can be further complicated for production servers which frequently have high availability requirements and have very limited change windows as a result.
It is very important for application patching to be applied in a prioritised manner, aiming to address high-risk computers and users more urgently.
Configure Microsoft Office macro settings

The general objective of this control is that Microsoft Office macros are disabled on workstations, or strictly controlled and limited when they are required for business purposes. This is because malicious actors commonly use Microsoft Office macros for spearphishing attachment and other associated attack methods.
VMware recommends that IT teams engage closely with organisation areas where macros have been used. For example, the finance team may extensively use macros in Excel.
Product capabilities – end-user computers
Microsoft Office macro settings on Windows workstations are commonly managed using baseline policy frameworks such as Configuration Service Provider (CSP) policies.
Workspace ONE UEM is used by organisations to manage workstations, including security policies and baselines. Workspace ONE UEM supports a range of policy frameworks including CSP policies and can be used to meet all Essential Eight maturity levels for this requirement.
Carbon Black Cloud can enforce predefined or customised security baseline policies and can meet this requirement of the Essential Eight.
VMware guidance – end-user computers
Restrictions on Office macros can be difficult to apply effectively on workstations so that necessary macros are permitted while malicious macros are blocked. In practical use, many organisations need to permit Office macros from trusted locations. A stronger focus on modern endpoint protection products may be more realistic and effective than managing trust lists for approved macros; for example Endpoint Detection and Response (EDR) tools which enforce behaviour-based protection, such as Carbon Black EDR or Carbon Black Cloud.
Note that Office macros are now disabled by default in Microsoft 365.
User application hardening

The general objective of this control is that non-critical features and functionality are disabled for standard essential workstation applications, so that there is reduced opportunity for these features to be used as part of a malicious attack.
Product capabilities – end-user computers
Web browser and Microsoft Office hardening on Windows workstations are commonly managed using baseline policy frameworks such as Configuration Service Provider (CSP) policies.
Workspace ONE UEM is used by organisations to manage workstations, including security policies and baselines. Workspace ONE UEM supports a range of policy frameworks including CSP policies and can be used to meet all Essential Eight maturity levels for this requirement.
Carbon Black Cloud can enforce predefined or customised security baseline policies and can meet this requirement of the Essential Eight.
VMware guidance – end-user computers
Many aspects of this control are dated. Java and Flash aren’t supported in modern browsers, and there are few applications in use that still require the use of Java or Flash on workstations. The intent of the control is to limit the attack surface for web browsers so that it is difficult for malicious code to be executed from the browser, resulting in the installation of malicious software on the workstation.
Restrictions on User Applications can be difficult to apply effectively on workstations so that necessary functionality is permitted while malicious functionality is blocked. A stronger focus on modern endpoint protection products may be more effective; for example Endpoint Detection and Response (EDR) tools which enforce behaviour-based protection, such as Carbon Black EDR or Carbon Black Cloud.
Restrict administrative privileges

The general objective of this control is to apply strict limitations for user accounts which have privileged access to systems.
Privileged access needs particular focus for key platform services such as Active Directory (AD), VMware vSphere and public cloud infrastructure. If privileged accounts for these platform services are compromised, an attacker can readily access and disable most of an organisation’s critical IT services – which is regularly demonstrated by ransomware attacks.
VMware sees three key recurring issues with privileged accounts:
- Too many individuals within an organisation have privileged accounts
- Too many individuals use their privileged account for non-privileged activity
- Privileged access is permitted without mandatory multi-factor authentication
The risks associated with excessive administrative privileges can be reduced through effective policy by:
- Restricting the number of privileged users
- Regularly reviewing and auditing privileged accounts
- Retaining audit logs of all privileged accounts
Note: Privileged accounts should only be used for privileged activity, and users should log out of that account when the task required for privileged access is completed.
Product capabilities – end-user computers
Workspace ONE Access provides a centralised identity aggregation point which can integrate with cloud and on-premises identity services such as Okta, Azure AD, Active Directory, PingFederate, and LDAP. Many aspects of the Essential Eight requirements for Restrict Administrative Privileges are configured using the external identity services.
Workspace ONE UEM can be used to apply security policies for privileged users, such as preventing them from accessing high-risk applications (including web browsers and email applications), as well as limiting access to online services.
VMware guidance – end-user computers, servers, and workloads
Some of the Restrict Administrative Privileges requirements relating to virtualisation and jump servers are frequently implemented using software-defined data centre (SDDC) platforms such as vSphere, VMware Cloud Foundation (VCF), or VMware Cloud. NSX Security provides identity-based firewall functions that can be used to enforce many of these requirements for workloads within an SDDC environment.
One of the challenges with controlling the use of privileged accounts for workstations and jump servers is that many applications require privileged access during installation. As a result, it is difficult to enable staff to install and use necessary applications without granting them privileged access. Dynamic Environment Manager integrates with the Workspace ONE platform to enable applications from approved vendors to install with privileged access, so that most end-users can effectively work without needing privileged access.
Gaining unauthorised privileged access is a key focus of malicious actors during a cyber-attack. AD has been used operationally in many organisations for over 20 years and it is important to emphasise that AD design approaches from 10 or 20 years ago do not provide strong protection against the attack methods that are used by capable threat actors today (such as cyber-crime groups or nation states). AD design and configuration weaknesses are a very high security risk in many organisations and it is recommended that organisations evaluate options to harden and clean-up their AD, including adoption of a tiered AD model aligned with Microsoft recommendations.
Patch operating systems

The general objective of this control is that operating system (OS) vulnerabilities on workstations and servers are addressed through patching.
Patching of operating systems can be done through automation to ensure that it is done continually and rapidly. OS patching is often a challenge for organisations given the number of patches required and the number of devices to address. This is further complicated by non-standard configurations, which require expensive bespoke patching.
Product capabilities – end-user computers
Workspace ONE UEM is used by organisations to deliver operating system patches to relevant workstations such as Windows and Mac computers, and mobile devices. Workspace ONE UEM is fully featured for managing patches and can be used to meet all Essential Eight maturity levels.
Workspace ONE MTD is used by organisations to provide device, network, application, and phishing protection for mobile operating systems, such as iOS, iPadOS, Android, and Chrome OS, and to provide integration with Workspace ONE UEM. Workspace ONE MTD can identify missing critical operating system updates for BYOD or organisation-owned devices, while integrating with Workspace ONE UEM and Workspace ONE Intelligence for response and enforcement of policy.
Workspace ONE Intelligence has vulnerability management functionality for known operating system vulnerabilities (including Windows and Mac). Reports and dashboards can be used to prioritise remediation activities such as patching. Workspace ONE Intelligence can also provide enhanced visibility into mobile devices from its integration with Workspace ONE MTD.
The Workspace ONE Intelligence rules engine can take automated remediation actions, such as applying patches to the impacted devices (typically using Workspace ONE UEM to deliver the patches).
Product capabilities – end-user computers, servers, and workloads
Carbon Black Cloud provides vulnerability management information for known operating system and application vulnerabilities. Carbon Black App Control provides a near real-time application and file inventory of every endpoint, which can also be used to identify computers that require patching.
Product capabilities – servers and workloads
VMware Aria provides a single platform with multi-cloud management capabilities, which spans VMware’s previous vRealize, CloudHealth, and Tanzu Observability offerings.
Aria Automation (formerly vRealize Automation) provides powerful infrastructure automation across clouds and data centres, and is frequently used for deploying operating system patches on server workloads using DevOps processes.
Aria Automation Config (formerly vRealize Automation SaltStack Config) is a software configuration automation tool that extends Aria Automation with rich security baseline and guardrails functionality, to ensure that cloud and data centre workloads meet a desired configuration state. It is commonly used to detect configuration drift, and to automate the remediation – including deployment and enforcement of operating system patches for server workloads. Workload OS patches can also be automated with fast, scalable, event-driven orchestration using Aria Automation for Secure Hosts (formerly vRealize Automation SaltStack SecOps).
Aria Operations (formerly vRealize Operations) has configuration and compliance dashboards that can effectively highlight out-of-date operating systems and infrastructure components for data centre workloads.
NSX Security provides extensive network security functionality that can be applied flexibly for all server workloads that are part of a software-defined data centre (SDDC). NSX Security includes network intrusion prevention service (IPS) functions that can be enabled to protect workloads from known network attacks. Virtual patching functions can be integrated with the network IPS using NSX Advanced Threat Prevention and virtual patching is also available as part of the Web Application Firewall (WAF) services within NSX Advanced Load Balancer. These network-based protection capabilities can be used to provide protection for workloads with known vulnerabilities that cannot be patched immediately.
VMware Cloud on AWS (VMC on AWS) and similar cloud services such as Azure VMware Solution (AVS) and Google Cloud VMware Engine (GCVE) provide SDDC environments where the VMware software stack is fully patched by the cloud service provider. This means that consumers of these cloud services no longer need to patch the SDDC components such as ESXi, vCenter Server, vSAN, or NSX.
VMware guidance – end-user computers
The Modern Management approach to patching for end-user devices is based on deployment rings, so that new patches are automatically deployed on increasing numbers of devices. This approach enables patches to be released quickly without the bottleneck of formal user acceptance testing. Meanwhile, the progressive rollout allows early deployment waves that affect small sets of sample staff to detect problematic patches, so that a deployment can be stopped before too many devices are affected. Workspace ONE UEM readily supports Modern Management approaches to operating system patching. Note that UEM provides OS patching support across Windows, Mac, iOS, iPadOS, and Android, including support for Apple’s Rapid Security Response features across workstations and mobile devices.
The dynamic nature of workstation environments means that it is difficult to achieve high patching compliance for workstation operating system components. This can be improved using products such as Workspace ONE UEM, which provides accurate and up-to-date visibility indicating whether patch deployments on devices were successful, and automation of responses to failed installations.
VMware guidance – servers and workloads
The modern DevOps approach to server management involves an Infrastructure-as-Code model which defines the specific operating system version and patches that are deployed for server workloads. When an operating system update becomes available, this is included in the code pipeline and new workloads are deployed with the updated software while old workloads are removed. This operational model means that in-place patching of workloads is no longer required.
Organisations that use Kubernetes-based container images to deploy and manage applications will generally establish DevOps code pipelines for their container images. Tanzu Application Platform can be used by developers to simplify and automate their development processes with Kubernetes management, and it includes Tanzu Build Services to automate source-to-container workflows. This ensures that updates for key source images can be included automatically into containers when they are packaged.
Operating system patching for traditional server environments is less likely to require regression testing than application patching does, and so a Modern Management approach for deployments can be very practical in traditional server environments. However, this is still difficult for production servers which usually have very limited change windows.
It is very important for operating system patching to be applied in a prioritised manner, aiming to address business critical infrastructure more urgently. Note that unpatched perimeter systems are frequently targeted by malicious attackers and are therefore a very high risk. As a result, it is an extremely important priority to apply security patches promptly for perimeter systems – including security, network, and gateway devices.
Multi-factor authentication

The general objective of this control is that strong authentication is used effectively instead of weaker password-based authentication when personnel are accessing an organisation’s services and information.
Product capabilities – end-user computers, servers, and workloads
Workspace ONE Access is used by organisations to provide multi-factor authentication (MFA), including password-less authentication options that provide full single sign-on without any user interaction across all device types. MFA can be provided using the Workspace ONE Intelligent Hub mobile app, which can leverage the mobile platform’s biometric services if required. MFA can also be provided by integrating with third-party authentication solutions such as RSA SecurID, RADIUS, or FIDO2. For organisations that want to support a federated derived credential model, Workspace ONE PIV-D Manager can also be integrated so that mobile devices can be enrolled with derived credentials.
Workspace ONE Access has powerful, risk-based Conditional Access functionality which can be used for step-up or mandatory MFA in a range of scenarios (for example, based on device compliance, user behaviour, location, and risk analytic feeds). A key benefit is that it enables services to authenticate users and devices without requiring user interaction (such as prompt-less options, rather than requiring one-time passwords or push notifications).
Workspace ONE Access can also be used for centralised identity aggregation and to apply MFA for end-user computers and for workloads in a SDDC, across multiple sources of identity.
Workspace ONE can be used to meet all Essential Eight maturity level requirements for MFA.
VMware guidance – end-user computers, servers, and workloads
Workspace ONE offers more flexible MFA than many other vendors, which makes it practical to roll out for large user bases while minimising the impact and costs for end users.
Regular backups
The general objective of this control is that sound backup processes are applied to enable timely recovery of an organisation’s important systems and information.
Cybercrime groups that use ransomware will aim to delete an organisation’s backups before they deploy and activate the ransomware – if the target organisation has no recovery point available then it becomes much more likely that they will need to pay the ransom. It is extremely important to ensure that backups are protected from deletion, and that privileged access to backup services is strictly controlled.
Product capabilities – servers and workloads
VMware does not offer standard backup software for backup and restoration of software, data, and configuration settings from any system. VMware’s software-defined data centre (SDDC) platforms provide a backup API that is used by many third-party vendors to provide hypervisor-level backup capabilities.
However, VMware does have a “restore proofed” solution available for vSphere environments:
- VMware Cloud Disaster Recovery (VCDR) provides secure and immutable cloud-hosted backup of vSphere virtualised environments, enabling fast and cost-effective recovery with automated failover and failback in various disaster scenarios.
- Ransomware Recovery provides additional functionality for VCDR to simplify the identification of safe recovery points, and to enable rapid validation of recovery points by response teams during a major security incident. This can dramatically speed up the recovery of critical systems if the organisation has suffered a ransomware attack by a cybercrime group.
VMware guidance – servers and workloads
VCDR and Ransomware Recovery are extremely effective and practical solutions for disaster recovery of server workloads that run in a SDDC, such as vSphere, VMware Cloud Foundation (VCF), or VMware Cloud. Most organisations will have additional data, software, and configuration settings outside of the SDDC, and so additional backup services will be required.
Additional notes about Maturity Level Three
For most Essential Eight controls, Maturity Level Three requires the use of centralised and tamper-resistant logging services. These services are typically provided using a Security Information and Event Management (SIEM) service, or a dedicated security data lake.
VMware products generate security logs that can be sent via Syslog to any centralised log service such as VMware Aria Operations for Logs (formerly vRealize Log Insight), and forwarded to an organisation’s SIEM, or the security logs can be sent to the SIEM directly.
Summary
This whitepaper provides an overview of VMware’s guidance in relation to the Australian Cyber Security Centre (ACSC) Essential Eight Maturity Model. The paper does not provide detailed configuration recommendations on how to comply with the Essential Eight maturity levels.
Changelog
The following updates were made to this paper:
| Date | Description of Changes |
| 2023/04/26 |
|
About the Author and Contributors
The following individuals authored and contributed to the creation of this document:
- Peter Dowley, Federal Cyber Security Manager, VMware
- Shane Fowler, Solutions Architect, Global SME Engineering, End-User Computing, VMware
- Vikram Kumar, Senior Solutions Engineer, Security, VMware
- Martin Holzworth, Cyber Security Advisor, VMware
- Andrew Osborn, Staff Technical Marketing Architect, End-User Computing, VMware
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware End-User-Computing Technical Marketing at euc_tech_content_feedback@vmware.com.
