How to use Workspace ONE to manage local VMs with our new beta
|
This blog post was originally published at VMware End-User Computing Blog. |
We recently shared news of an exciting new feature, now available in beta: Workspace ONE Managed VM.
VMware Workstation and Fusion are industry-standard type-2 hypervisors used by countless IT professionals and consumers across the globe. Workspace ONE UEM provides comprehensive Windows 10 device management with the ease of a cloud service. Workspace ONE Managed VM brings these two technologies together providing the best of both worlds: local hypervisor resources with enterprise-class device management.

In this article, you will get a closer look at the technology, how it works, and how you can implement it. Significant thought and engineering work have gone into securing the Windows 10 Managed VM guests, and the solution supports implementations on both managed and unmanaged Windows 10 and macOS hosts. I’ll go through the stages of the process, and highlight the security capabilities built into the product for each stage.
Prerequisites
As an administrator of Workspace ONE Managed VM, you need VMware Workstation or Fusion, a copy of Windows 10, a Workspace ONE tenant, and the Managed VM provisioning tool to get started. The Managed VM provisioning tool can be found on the VMware beta portal and contains the bits for the VM packager, the host component, and the guest component referenced later in this article. Be sure to check the documentation in the beta portal for minimum software versions of Workspace ONE UEM, Workstation, and Fusion.
If you need demo licensing, see the following resources:
- You can get a functional Workspace ONE sandbox tenant for testing purposes from VMware TestDrive.
- VMware Workstation Pro evaluation for Windows 10 hosts.
- VMware Fusion Pro evaluation for macOS hosts.
Authoring the VM
During the authoring phase, you create a Windows 10 VM, configure data loss prevention (DLP) policies for the virtual disk, then digitally sign the VM to prevent tampering during distribution.
The following outlines the high-level authoring procedure:
- Create a Workspace ONE provisioning package, which contains a PPKG and unattend.xml file.
- Create a Windows 10 VM using Workstation or Fusion.
- Install the Workspace ONE Managed VM guest component. You can add this component to the PPKG, install it manually, or distribute it later with UEM.
- Use the Workspace ONE provisioning tool to apply the provisioning package and generalize the Windows 10 image.
- Use the Workspace ONE Managed VM provisioning tool to sign and ZIP the image for distribution.
Security in Authoring
Because Managed VMs are meant to run on either managed or unmanaged endpoint devices, securing the VM is imperative. Workspace ONE Managed VM provides a layered approach to security.
Minimal guest content – An authored VM should contain little more than the operating system. Excluding data and applications from the initial package prevents data loss should the VM fall into the wrong hands during distribution. A secondary benefit is packaged VMs are small, easing the burden of distribution.
VM restrictions – Several required and recommended DLP settings are validated during the authoring and packaging process. Workspace ONE Managed VM reads and enforces standard Workstation and Fusion VM policies, preventing unwanted movement of data between the guest VM and host device, while eliminating the need for additional management tools. Simply deactivate the camera, shared folders, virtual printers, etc. within the Workstation or Fusion VM settings, and Managed VM ensures these settings are enforced on the guest.
Digitally sign components – The Workspace ONE Managed VM packaging tool uses your digital certificate to sign VM components such as the VMDK and VMX files, as well as the final ZIP package used for distribution.
Distribute the VM
Workspace ONE Managed VM provides considerable flexibility in deployment options, supporting a wide range of use cases and customer requirements. Whether you own and manage the endpoints with Workspace ONE UEM, a legacy PCLM tool, or are trying to provide a corporate image to support personal or contractor BYOD scenarios, Managed VM distribution can easily be adapted to fit your model.
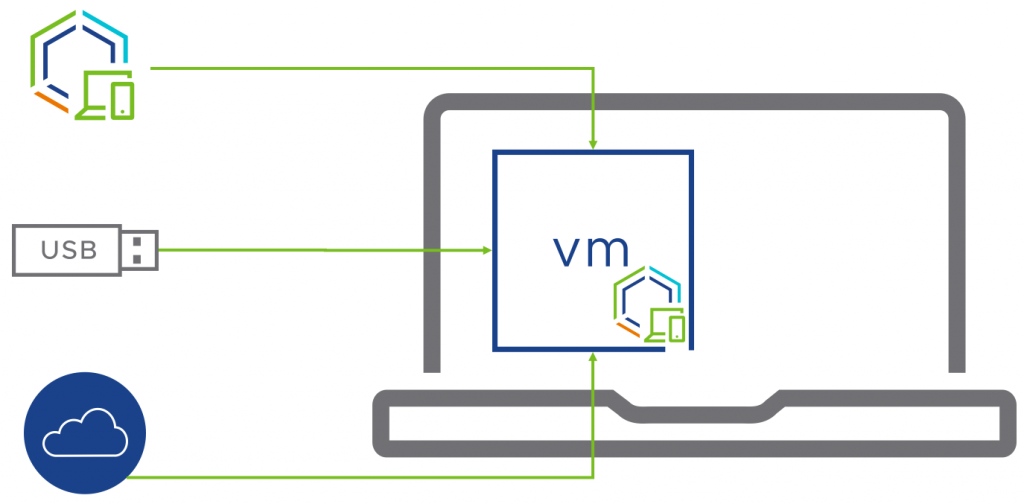
Enrolling endpoints in Workspace ONE can provide an end-to-end solution, with simple, automated distribution of the packaged VM, the Managed VM host component, and prerequisite hypervisor. Alternatively, you can physically distribute packaged VMs using removable media, or host the packaged VM on a public or private cloud sharing platform.
Security in Distribution
Securing and managing the lifecycle of the guest VM with Workspace ONE UEM is a fundamental capability of the Managed VM solution. You configure a Workspace ONE UEM enrollment grace period, ensuring the guest VM is enrolled within an acceptable time frame after provisioning occurs. In the current beta, end-users will be continually prompted to enroll if the VM is not enrolled within the grace period. Future releases will permit more severe actions such as making the VM unusable if not enrolled on time.
Provision the VM
To provision the Managed VM, the endpoint device requires VMware Workstation or Fusion, along with the Workspace ONE Managed VM host component. Provisioning is then a matter of invoking the Managed VM host component to unpack the guest VM from the ZIP and add it to the Workstation or Fusion inventory.
Workspace ONE UEM can be used to deliver all of these components and automate the process. Alternatively, you could use other PCLM, packaging, or automation tools, or do the process manually.
Once the VM is provisioned and powered on, the user is guided through the Windows out-of-box experience (OOBE), the VM is automatically enrolled in Workspace ONE UEM, and UEM completes staging of the VM with apps, policies, and more.
Security in Provisioning
There are several security features that come into play during guest provisioning:
- As the VM components are extracted, the digital signature of the ZIP and all contained components are verified.
- A vTPM device is automatically created with keys protected by the host operating system.
- Once powered on, the Workspace ONE enrollment grace period begins, ensuring timely enrollment of the guest VM.
- A Workspace ONE BitLocker profile can be automatically distributed and applied upon successful enrollment, providing in-guest VM encryption. BitLocker keys are protected by the vTPM created on the VM, preventing data loss if the VM is moved, lost, or stolen.
- The Managed VM host component will auto-repair configuration settings to prevent manual tampering of the VMX file.
What about other Workspace ONE security controls?
Up to this point, we have explored several security features implemented and enforced by Workspace ONE Managed VM from the authoring to the provisioning phase. It is important to note this is not the end of the secure management story, but rather the beginning!
Once the guest VM is automatically enrolled in UEM, you have full control over the lifecycle of the virtual guest OS. From remote management to application lifecycle, patch management to security baselines, remote lock to enterprise wipe, the full power of the Workspace ONE platform is available for your Managed VMs.
What’s Next?
I hope this brief look at the Workspace ONE Managed VM technology highlights the simplicity of design, the power to support a wide variety of use cases, and the flexibility to build a solution that meets your needs with managed or unmanaged endpoints.
The Workspace ONE Managed VM technology is now available for public beta. If you would like to sign up, simply navigate to https://beta-ea.vmware.com, search for WS1 ManagedVM, and try it for yourself!
