Zero Trust Secure Access to Traditional Applications with VMware
VMware HorizonVMware Workspace ONE Access
VMware Workspace ONE UEM
VMware Unified Access Gateway
VMware Workspace ONE Intelligence
VMware Dynamic Environment Manager
VMware NSX-T Data Center
Introduction: What Is Zero Trust?
Zero Trust is a hot topic today. The problem is that there is no fixed definition of Zero Trust. Most experts agree that with Zero Trust, we should not default to trusting someone or something just because it is plugged in to a certain network. But if we are not going to place our trust in the local network, we must establish trust using other methods.
Another issue with the traditional security architecture is that the local network usually encompasses a large perimeter, which is difficult to secure. Once a large perimeter is penetrated, it is very difficult to contain the attack. The ability of threats to move laterally (east- west traffic) is often a result of having a large perimeter, as is illustrated in the following figure.
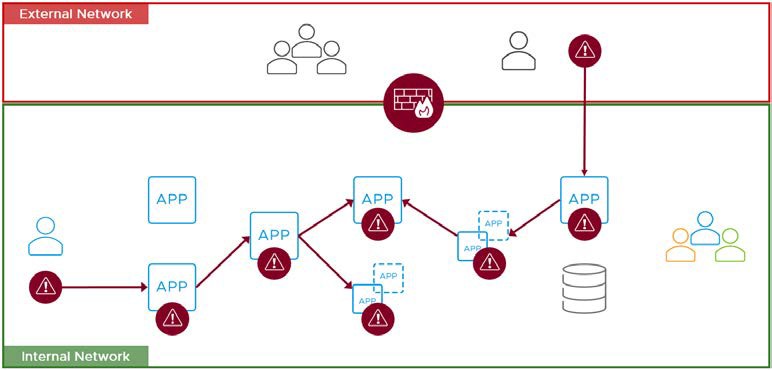
Figure 1: Traditional Perimeter-Based Security Model
With Zero Trust, we shrink the perimeter to include only the backend system for a particular application and its data. All user access is treated the same. From a security standpoint, there is no difference between using a traditional internally connected device versus using a device that connects over the Internet. All requests are validated by using the same stringent requirements.
With multiple, much smaller perimeters, an attack is much easier to contain within one area.
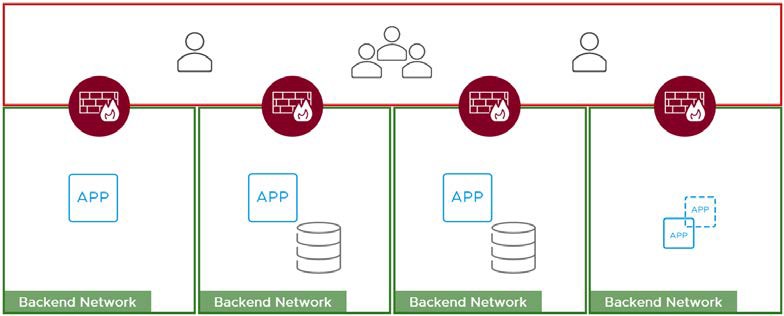
Figure 2: Zero Trust Security Model with Perimeters Around Each Application
If we cannot, by default, trust everything inside the perimeter of the local network, where can we place our trust? At VMware, our Zero Trust solution is based on developing five pillars of trust. These pillars are device trust, user trust, transport/session trust, application trust, and data trust. A full implementation requires all five pillars.
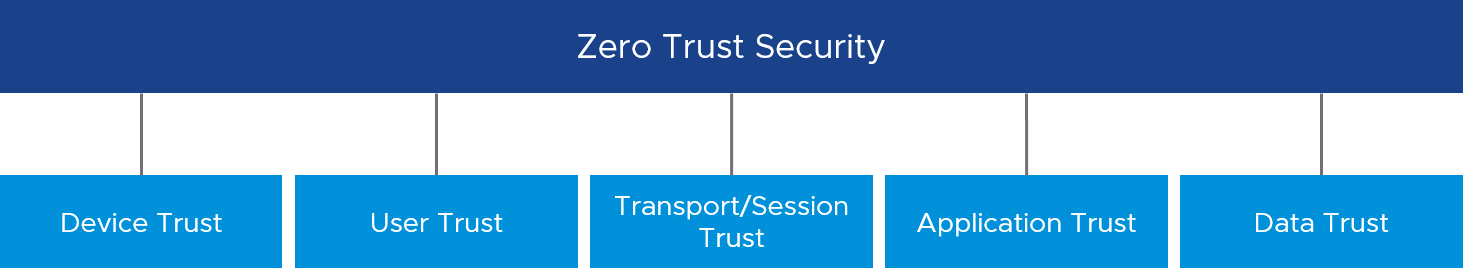
Figure 3: Five Pillars of Zero Trust
Another key component of Zero Trust is the concept of least-privilege access. The idea is that a user or system should have access to only those resources that are specifically required to perform the task at hand. No more, no less. This concept is discussed in detail later in this guide, in Principle of Least-Privilege Access.
Although companies are interested in moving to a Zero Trust architecture because it offers more security than traditional models, most companies will not be able to implement Zero Trust principles and technologies throughout their organization all at once. Most organizations start implementing Zero Trust with only one application or a small number of applications.
Purpose of This Guide
This guide addresses only one use case: securing traditional, Windows-based applications. This guide in no way presents a complete Zero Trust model that covers any other use case. However, the foundational principles used in this guide will be used for future Zero Trust use cases that VMware documents. Reading this guide will therefore familiarize you with the core principles and architecture described in other use cases.
Intended Audience
This guide helps IT architects, consultants, and information security administrators involved in planning, designing, and implementing a Zero Trust security solution for the VMware Horizon® desktops and published applications in their organization. Readers should have:
- A solid understanding of the mobile device landscape
- Familiarity with device-management concepts
- Knowledge of identity solutions and standards, such as SAML federation
- A good understanding of virtualization, in particular any platform used to host services such as VMware vSphere®
- A solid understanding of desktop and application virtualization
- A solid understanding of firewall policy
- A good working knowledge of networking and infrastructure, covering topics such as Active Directory, DNS, and DHCP
Use Case: Securing Traditional Windows Applications
The Zero Trust methodology can be applied to protect any application, but the implementation might look different, depending on the use case. In this document, we focus on one specific use case: protecting traditional applications.
By traditional application we mean an application that is not necessarily designed for external access. Such an application typically:
- Relies heavily on Microsoft Active Directory
- Might use proprietary communication methods
- Often requires a Windows machine to run the end-user-facing client software
These traditional applications are often business-critical, and many times there is no upgrade path to a modern architecture.
Note: Although the Zero Trust strategy for web applications might differ from that for traditional applications, you may still choose to use the architecture discussed in this document for web applications, especially if the web application requires a specific version of a web browser.
VMware Horizon as a Bridge from Traditional to Modern
In order to isolate and modernize traditional applications, we must use a technology that allows us to create a bridge between the traditional architecture and the future based on Zero Trust. In our solution, that technology is VMware Horizon virtual desktops and published applications.
Although all the functionality discussed in this guide applies to virtual desktops as well as published applications, we focus on the published application feature. This focus allows us to specify access rules down to the individual application and its data, which creates a much more granular security posture.
Alignment of Workspace ONE and Horizon with the Trust Pillars
The following diagram shows how the VMware Workspace ONE® and Horizon products and solutions for this use case can help establish each applicable trust pillar. Note that some products span multiple pillars.
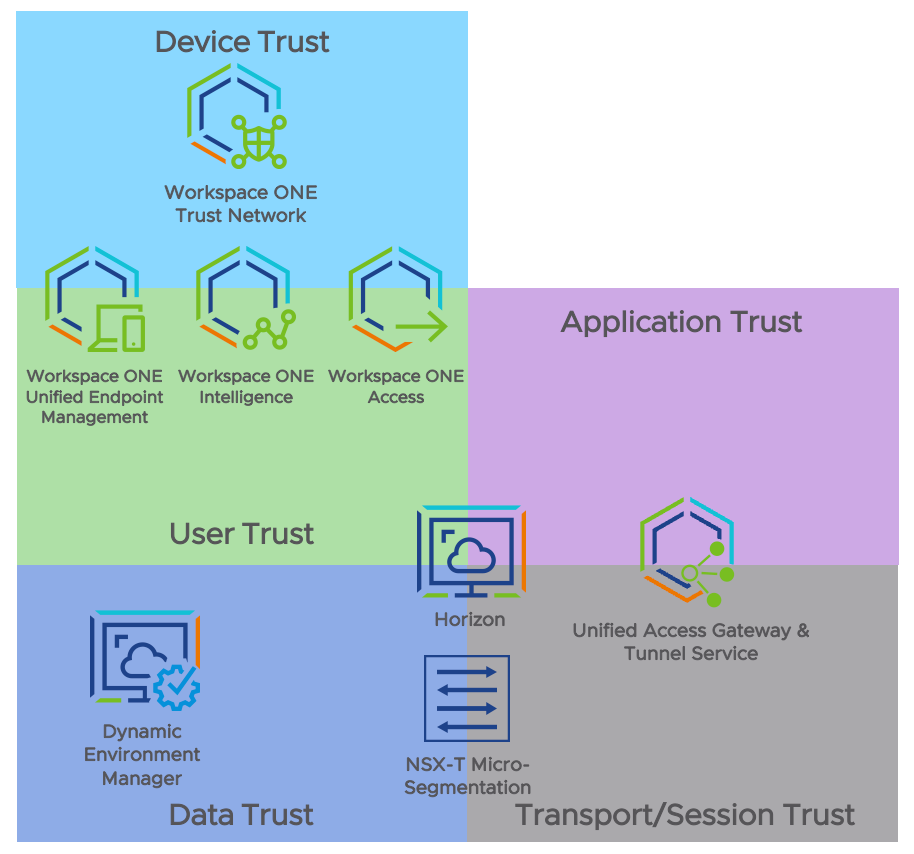
Figure 4: Product Alignment to Trust Pillars
Later in this guide, we discuss each product in more detail and describe which features you can use to achieve trust in each pillar.
In our design, we focused on device-agnostic solutions. Although platform-specific features are available and can enhance the solution, for simplicity, we have focused on broad device support. You may decide to add platform-specific features and third-party solutions into the mix, but these options are outside the scope of this document.
Logical Architecture of the VMware Zero Trust Solution
For the use case covered in this document, the following diagram shows the relationship and interaction of the various products used. More detail on product features and integration points is given later in this document.
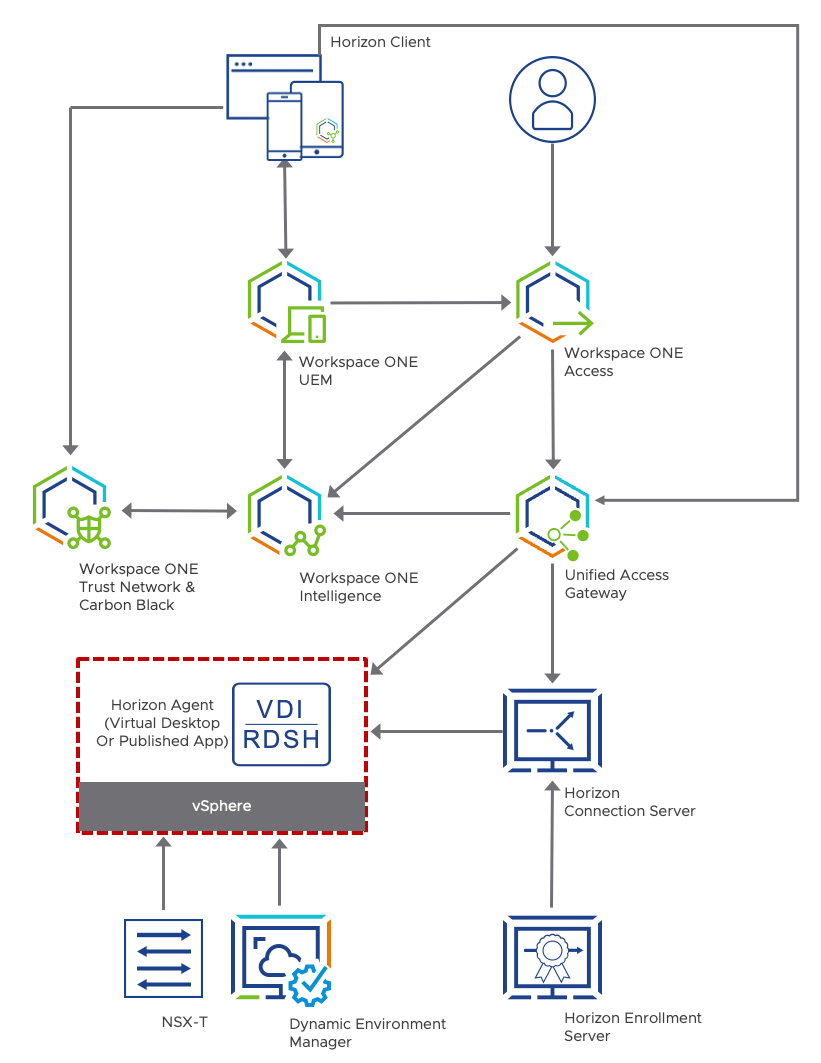
Figure 5: Logical Architecture
Now that you have an overview of the system you can build for a Zero Trust solution, we delve into the details and rationale for each pillar of trust, starting with device trust.
Device Trust
In the Zero Trust model, device and user trust are two pillars of trust that people often begin with. In general, these two areas are where you find the most products and vendors offering solutions. For Zero Trust , as an IT administrator, you need to know your devices before you can trust them. You must have an inventory specifying which devices are owned and thereby controlled by your company. You must have a solution that monitors, manages, and controls these devices.
Note: When it comes to supporting BYOD (bring your own device), you might simply have to relax your trust level on the device. End users are not often eager to let their personal devices be managed by their employer.
To secure a strong level of trust in end users’ devices, you might need to know, for example, whether the local disk is encrypted properly, what the antivirus status is, what versions of the OS and applications are installed, and more. Knowing all these properties adds to your overall trust in the device.
Included in this pillar is the capability for automatic remediation. For example, if a device does not have the correct version of the OS or an application, the system should be able to remediate by pushing out the correct version or by guiding the user in how to upgrade.
The rest of the sections in this chapter provide more detail about the various elements of device trust:
- Device Management
- Device Inventory
- Device Compliance Check and Remediation
- Real-Time Device Threat Detection and Response
- Certificate Management
Device Management
Device management means having control over the device to achieve the desired goals, including control over what software is installed, which versions, and under what conditions a given application may be used. For example:
- To achieve certain privacy goals, the camera app on hospital employees’ managed phones might need to be turned off when employees enter the hospital where they work.
- To avoid data theft, the OS on the device needs to be kept up to date, and the storage disk might need to be encrypted.
To achieve these goals, device management includes determining security policies such as how to identify the device, often using multiple authentication and authorization methods. To address constantly changing circumstances, device management includes continuously monitoring the state of the device and its attributes so that at any time, security policies can be updated and applied. For example, if an employee suddenly quits and goes to work for a competitor, you might want to lock the now-former employee out of the device and perform a device wipe.
Table 1: VMware Products for Device Management
| Feature | Product |
| Device enrollment | Workspace ONE UEM |
To become a managed device, the device must go through a quick and easy VMware Workspace ONE® Unified Endpoint Management (UEM) enrollment process. After enrollment, the system manages the device. The following steps outline the process:
- The device sends device attribute information to Workspace ONE UEM.
- Workspace ONE UEM issues a device certificate to the enrolled device, which is used to establish trust between Workspace ONE UEM instance and the device.
- The server issues device management profiles and other over-the-air configurations to the device.
- Workspace ONE UEM also runs periodic compliance checks to ensure that the device complies with the organization’s compliance policies.
- If the device is found to be out of compliance, enforcement or remediation occurs according to the organization’s policies.
Note: The compliance engine is described in detail in the section Device Compliance Check and Remediation.
Device Inventory
Because credentials can be stolen and servers exploited, in a Zero Trust model, IT must also catalog all hardware devices to verify that each device is a known secure endpoint. IT can then use inventory- based access controls and allow access only from devices registered to authenticated users.
Table 2: VMware Products for Device Inventory
| Feature | Product |
| Device enrollment | Workspace ONE UEM |
| Access control | Workspace ONE Access |
When the device is registered or managed with Workspace ONE UEM, it gets added to the device inventory list. Only devices included on this inventory list can progress to the following stages:
- From Workspace ONE UEM, receive configuration profiles and policies that allow access to protected resources.
- From VMware Workspace ONE Access™ control conditional access to the apps.
Device Compliance Check and Remediation
After IT determines what security policies are required, the next step is to make sure devices comply with these policies, which might include, for example, determining whether the device:
- Is included in the current inventory list
- Has the required OS version
- Has the required agents installed
- Is running the latest software patches
- Uses strong PIN/unlock methods
Compliance checks must be performed by collecting information from devices at both scheduled and unscheduled times. In addition, IT must determine the consequences for noncompliance, which might include, for example, denying access to corporate resources. Determining that the device is out of compliance is helpful only if the system can also respond and remediate to quickly bring the device into compliance.
Table 3: VMware Products for Device Compliance Checks and Remediation
|
Feature |
Products |
|
Compliance rules |
Workspace ONE UEM Workspace ONE Access Workspace ONE Intelligence |
Compliance
There are two methods by which Workspace ONE can measure compliance.
- Engine compliance – The compliance engine, a software algorithm that receives and measures scheduled samples, primarily determines the compliance of a device. The time intervals for running the scheduler are defined in the console by the administrator.
- Real-time compliance (RTC) – Unscheduled samples received from the device are used to determine whether or not the device is compliant. The samples are requested on demand by the administrator.
The compliance engine is an automated tool by Workspace ONE UEM that ensures all devices abide by your organization’s policies. These policies can include basic security settings such as requiring a passcode and having a minimum device lock period. For certain OS platforms, you can also set and enforce precautions such as setting password strength, denylisting certain apps, and requiring device check-in intervals to ensure that devices are safe and are in regular contact with Workspace ONE UEM.
The Workspace ONE Access component connects the Workspace ONE UEM device compliance knowledge to the flow of authentication. To make use of the device compliance status, you must chain two authentication methods in your access policies. First, you validate the user using a certificate- based authentication method. Next, you require the check for device compliance. The authentication process goes like this:
- Because the device uses certificate-based authentication, the device’s UUID can be retrieved by Workspace ONE Access.
- Workspace ONE Access uses API integration with Workspace ONE UEM to send the device’s UUID for validation and to check compliance status in real time.
Detection of Compromised Devices
In deployments of both BYOD and corporate-owned devices, it is important to verify that devices are healthy before letting them access corporate resources. Workspace ONE UEM leverages the VMware Workspace ONE® Intelligent Hub agent, which is installed on the device, to detect if the device is compromised; that is, rooted or jailbroken.
- On iOS devices, Intelligent Hub can dynamically update its detection algorithms over-the-air.
- On Android devices, Workspace ONE UEM leverages SafetyNet Attestation, which is a Google API, to validate software and hardware information to determine if a particular device has been tampered with or modified.
- On Windows devices, the Windows Health Attestation Service accesses device boot information from the cloud. This information is measured and checked against related data points to ensure that the device boots up as intended and is not a victim of security vulnerabilities or threats. Measurements include Secure Boot, Code Integrity, BitLocker, and Boot Manager.
Workspace ONE UEM enables you to configure the Windows Health Attestation service to ensure device compliance. For Windows 10 guidelines, see Configure the Health Attestation for Windows Desktop Compliance Policies and Compliance Policies, in the Workspace ONE UEM Product documentation. Because Workspace ONE UEM pulls the necessary information from the device hardware and not the OS, compromised devices are detected even though the OS kernel might be compromised.
Remediation
Once devices are determined to be out of compliance, the compliance engine warns users to address compliance errors to prevent disciplinary action on the device. For example, the compliance engine can trigger a message to notify the user that their device is out of compliance.
Devices not in compliance cannot have device profiles assigned to them and will not be trusted. If corrections are not made in the amount of time specified, the device loses access to certain content and functions that you define. The available compliance policies and actions vary by platform.
You can automate escalations when corrections are not made, for example, by locking down the device and notifying the user to contact you to unlock the device. These escalation steps, disciplinary actions, grace periods, and messages are all customizable with the Unified Endpoint Management Console.
In addition to the built-in compliance engine, administrators can leverage the VMware Workspace ONE® Intelligence™ automation engine to identity changes to any of more than 250 attributes from devices, applications, and OS updates. If any of these changes requires immediate action, they can trigger automated workflows involving the devices and third-party solutions.
Real-Time Device Threat Detection and Response
Traditionally, threats evolve as quickly as security researchers release patches for the vulnerabilities they find. The ability to detect malware, viruses, behavioral anomalies, and many other types of threats is essential, as is the ability to provide real-time remediation.
Table 4: VMware Products for Real-Time Threat Detection and Response
| Feature | Products |
| Trust Network | Workspace ONE Trust Network solutions, including:
|
CB Defense is a next-generation antivirus (NGAV) and endpoint remediation (EDR) solution that provides advanced protection and visibility to defend against malware and non-malware attacks, allowing IT administrator to:
- Respond to an attack as soon as it is identified.
- Visualize every stage of the attack with easy-to-follow attack chain details to uncover root causes in minutes.
- Immediately triage alerts by isolating endpoints, denylisting applications, or terminating processes.
- Open a secure shell into any endpoint on or off the network to investigate and neutralize threats remotely.
Workspace ONE Intelligence integrates with CB Defense to obtain threat activities in real time from Windows and macOS endpoints, allowing IT administrators to define automated actions against managed devices when a threat is identified.
Additional security solutions such Lookout on Mobile Threat Defense (MTD) and Netskope on Cloud Security Broker (CSB) can be leveraged to enhance endpoint and data protection. Both products are also part of the VMware Workspace ONE® Trust Network, and integrate with Workspace ONE Intelligence. Workspace ONE Intelligence consolidates all threat data to provide visibility into the threatscape and to enable the automation engine to take additional remediation actions on devices under attack.
Certificate Management
As the mobility of sensitive corporate content becomes the norm, the probability of unauthorized access and malicious threats increases. Even if you protect your corporate email, Wi-Fi, and virtual private network (VPN) using strong passwords, your infrastructure remains vulnerable to brute force attacks, dictionary attacks, and employee error.
Digital certificates provide optimal protection for securing your corporate assets. Certificates offer a level of stability, security, and sophistication with which passwords cannot compete. Certificate management by Workspace ONE UEM ensures security throughout the lifecycle of a device.
Table 5: VMware Products for Certificate Management
| Feature | Product |
| Digital certificates | Workspace ONE UEM |
Workspace ONE UEM installs a device certificate on the device and uses the certificate to establish trust between the Workspace ONE UEM server instance and the device. The certificate can be generated and signed by the default digital certificate authority, Workspace ONE UEM CA, or you can use a trusted third-party CA. Workspace ONE UEM supports many third-party certificate authorities.
User Trust
To ensure a high level of trust in the user, you must make use of modern and strong authentication methods. Relying on passwords alone is not sufficient. You can chain many authentication methods together, but you also must weigh the security benefits against any possible decline in user experience. The goal with Zero Trust is to enhance both security and user experience.
Certificates are ideal as the foundation of your user authentication method. With certificate-based authentication in place, you can add things like multi-factor authentication (MFA) for critical systems. Today most MFA solutions are user friendly and add minimal inconvenience to the user experience.
Conditional access rules can help determine whether and when to enforce stronger authentication. Conditional access is the foundation of Zero Trust, where you bring together not only the user but also the device posture. You can also decide the amount of time to live (TTL) for the user’s authentication. The lower the TTL of a session, the more often conditional access rules are invoked. But it is a balance. If the time limit is too small, users will be prompted for authentication too often. Offering a seamless, zero-touch authentication method will go a long way toward earning the acceptance of users.
The rest of the sections in this chapter provide more detail about the various elements of user trust:
Passwordless User Authentication
Passwordless authentication is a mechanism for determining the identity of the user without requiring the user to enter a password. Some types of passwordless authentication include:
- Biometrics, such as fingerprints or facial scans
- Hardware or software security tokens
- One-time codes or links sent to an email address or a mobile phone number
- Piggybacking on a service that has already authenticated the user
- Certificate-based authentication
The benefits of passwordless authentication include:
- Improved user experience, since users do not need to keep track of passwords
- Faster login times if the system does not need to wait for the user to enter something
- Better security because IT does not need to worry about users sharing or reusing passwords
- Reduction in maintenance costs because IT spends less time removing and resetting passwords for users who have forgotten their passwords
Table 6: VMware Products for Passwordless Authentication
| Features | Products |
| MobileSSO | Workspace ONE UEM |
| Certificate authentication | Workspace ONE Access |
Workspace ONE Access performs the act of authenticating users in our solution. Workspace ONE Access supports many types of authentication, including RADIUS, RSA SecurID, passwords, SAML authentication using external identity providers, and more.
Because in a Zero Trust implementation, we want to use strong authentication but still maintain a good user experience, we rely on different methods of certificate-based authentication. You can easily build and adjust access policies that require different levels of authentication, including multi-factor authentication if needed, but at its foundation, our Zero Trust solution is built on certificate-based authentication.
Workspace ONE Access supports multiple different methods of certificate-based authentication:
- Traditional certificate-based user authentication methods used by PC and Mac devices
- Our own certificate-based user authentication solution for iOS and Android devices, called MobileSSO
- Certificate-based device authentication, for validating the device itself
Mobile SSO technology provides the ability to sign in to an app on a mobile device once and gain access to all entitled applications, including SaaS apps. VMware leverages open standards such as SAML (Security Assertion Markup Language) and OIDC (OpenID Connect) to authenticate a user between the identity provider, namely, Workspace ONE Access, and the service provider, such as SaaS apps in the cloud. By eliminating the requirement of entering passwords to access a resource, this technology addresses security concerns and password-cracking attempts as well as offering an SSO experience for users.
Multi-factor Authentication
Multi-factor authentication (MFA) involves requiring at least two pieces of evidence that prove the user’s identity. These pieces of evidence are usually some combination of the following three factor types:
- Something the user knows, such as a password or the answer to a security question
- Something the user has, such as a hardware or software security token or a certificate
- Something the user is, which might mean a scan of the user’s fingerprint, retina, or face
Table 7: VMware Products for Using Multi-factor Authentication
| Features | Product |
| Verify (Intelligent Hub) | Workspace ONE Access / UEM |
Verify (Intelligent Hub) is a multi-factor (MFA) authentication method integrated with the Workspace ONE Intelligent Hub app that can be configured in Workspace ONE Access. When the Workspace ONE Intelligent Hub app is installed on Workspace ONE UEM managed or registered devices, Verify (Intelligent Hub) can be used as a second authentication method to access a restricted Hub catalog or restricted apps.
To use Verify (Intelligent Hub) authentication, Workspace ONE Access and Workspace ONE UEM must be integrated with Hub Services. You enable the authentication method in the Workspace ONE Access services and then add it as an authentication method in the built-in identity provider. When a request for Verify (Intelligent Hub) authentication is required, Hub Services sends an urgent notification message to the device that user designated to receive the notification.
Conditional Access
To implement conditional access, IT must decide what the rules will be with regards to allowing a user to access a particular protected service or data source. The idea is to reduce the attack surface by narrowing the conditions under which access is granted. In any given condition, you have a user on a device, in a location, at a particular time, using a certain app, and trying to access a service (or data). All of these numerous parameters can be taken into account to understand the context of the request:
- User
- Device
- Location
- Type of application being used
- What is being requested to access
From these parameters, IT can create rules that, for example, call for authenticating the user, device, and application and then authorizing that user on that device to access only that service.
Table 8: VMware Products for Using Conditional Access
| Feature | Products |
| Access policies | Workspace ONE UEM Workspace ONE Access |
With Workspace ONE Access, all requests for access flow through the conditional access rules engine:
- You can define different conditions such as group membership, device type, location, and resource requested.
- You can build conditional access for individual applications, Workspace ONE Access itself, or a combination of these. For example, you can allow seamless access to some applications while requiring step-up authentication using MFA for others.
- To validate the user often, you can adjust the time to live for each conditional access rule.
- You can allow for fallback methods of authentication. This hybrid, fallback mode is typically used if some client devices have not yet been enabled for Zero Trust.
With conditional access, you chain multiple authentication methods to build a strong trust level in your user. When you integrate Workspace ONE UEM with Workspace ONE Access, you can leverage the device compliance status collected by Workspace ONE UEM to implement conditional access.
Workspace ONE Access chains user authentication together with the authentication method called Compliance Check, as follows:
- Workspace ONE UEM distributes and manages the certificate on the device.
- Workspace ONE Access collects the device’s UDID from the certificate the device presents as a method of authentication.
- To perform the device compliance check, Workspace ONE Access connects to Workspace ONE UEM through API calls and passes the device’s UDID (unique device ID) to Workspace ONE UEM.
- Workspace ONE UEM then checks the compliance status and passes the information back to Workspace ONE Access.
Transport and Session Trust
To secure communication between the user, on their device, and the backend application with its data, we need transport and session trust. This trust pillar is a critical in making sure only valid requests are passed to the backend.
In an ideal situation, you could interact with an existing session and terminate it immediately when a change in trust level occurs. But today only a few solutions have this capability, and their support for applications is limited. The best we can probably do today is to make sure the backend is protected as much as is absolutely possible.
A minimum requirement in Zero Trust is the encryption of communication between the user’s device and the backend application data. Traditional applications typically use protocols not suitable for Zero Trust. Therefore, in this use case, we make use of supplemental technologies to enhance the isolation and communication between the end user and the application.
The rest of the sections in this chapter provide more detail about the various elements of transport and session trust:
Principle of Least-Privilege Access
As you might have already learned, the principles of Zero Trust are, “never trust, always verify, enforce least privilege.” Least-privilege access means giving users only as much access as they need, which minimizes each user’s exposure to sensitive parts of the network.
The idea of least-privilege access is to provide granular role-based access to privileged resources. For example, users who belong to the HR department would get access to only the HR applications and only the servers and data required for HR job functions. Conversely, users who belong to the Finance department would get access to only the Finance applications and only the Finance servers and data. Neither group of users would get access to the other group’s applications, servers, or data.
Table 9: VMware Products for Least-Privilege Access
| Feature | Products |
| Micro-segmentation | Unified Access Gateway NSX-T Data Center |
Segmentation of Traffic into Multiple Networks
Managing data flow requests, which might be coming from anywhere all the way to the backend zone, as well as controlling privileged network access are essential tasks for a Zero Trust implementation.
VMware Unified Access Gateway™ acts as the gateway, or enforcement point, to control access to published applications and virtual desktops delivered by Workspace ONE. Unified Access Gateway ensures that connections to virtual applications and desktops are always from trusted, authenticated, and authorized users, who are restricted to using managed and compliant devices, and are limited to using specific protocols. Any unauthorized traffic is blocked and is prevented from accessing any backend resources.
Unified Access Gateway supports segmentation of network traffic through a multiple-NIC configuration. The three-NIC configuration allows for the segmentation of traffic in (1) the public or corporate network, (2) the management network, and (3) the backend network. Routing capabilities allow users to access backend data in separated networks.
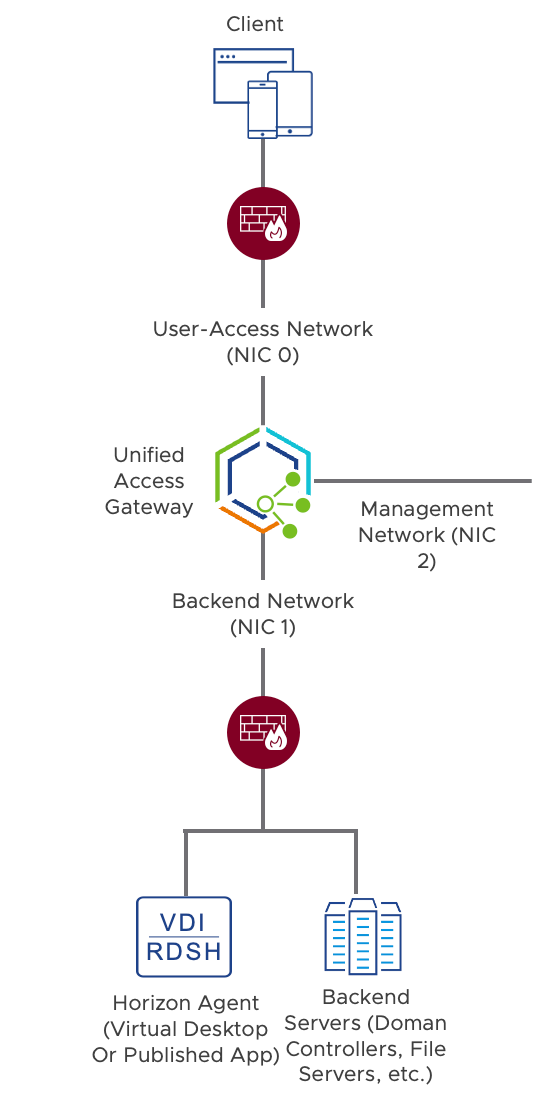
Figure 6: Network Segmentation Using the Three-NIC Configuration of Unified Access Gateway
Contextual Granularity Through Distributed Firewall Rules
At the transport and network layer, the principle of least privilege can be achieved by using VMware NSX-T™ Data Center. The distributed firewall feature allows for the definition of network security policies and firewall rules that can be applied granularly based on context. This allows for:
- Micro-segmentation – Enables micro-segmentation to protect virtual machines from the lateral spread of threats. The security policy is defined based on context and is enforced individually. Each VM can have individual firewalls and individual security policies.
- Identity-based firewall – Applies micro-segmentation and applies the network security policy based on who the user is and which Active Directory groups they belong to.
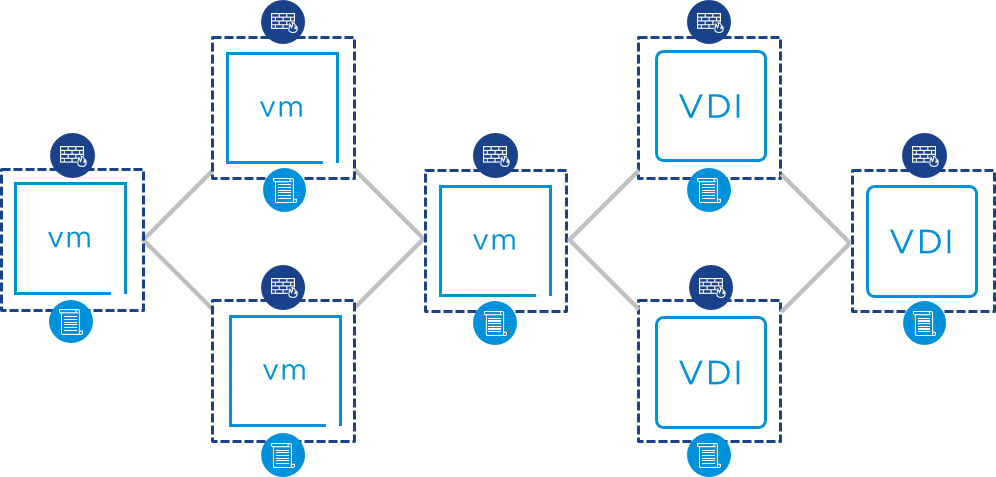
Figure 7: Micro-segmentation Enforcing Network Security Policy at the Individual VM Level
The use of micro-segmentation allows for the definition of network policies that will be applied around every resource in the data center.
- Servers can be secured so that only required sources are allowed to communicate and only over the necessary network ports.
- Desktops can have policies applied to prohibit unnecessary lateral communication. For example, rules can block desktop-to-desktop communication.
Dynamically Applied Identity-Based Firewall Rules
The use of identity-based firewalls takes this strategy to the next level in a Horizon environment. The network policy can be dynamically applied based on who the user is. This allows for the policy-based lockdown of the environment to the least privilege required for that user.
With VDI, each user is presented with an entire desktop VM. Firewall rules are based on giving a single user access to their entitled desktop VM on a per-NIC basis.
With RDSH-published applications, each user is presented with an application or session inside a shared server VM. Features include:
- Context-aware support for virtual user sessions running on RDSH
- Application of firewall-rule-based multi-user and multi-session identification, on a per-NIC basis
- Micro-segmentation by NSX-T Data Center of each session for Horizon RDSH based on user ID
- Granular application access to simultaneously logged-in users
Encryption of the Transport Protocol
In a Zero Trust model, the goal is to encrypt all data transmitted between devices and data stored in the data center. This end-to-end certificate-based encryption is used to avoid any data theft during transit. When every packet is encrypted, even within the same data center, you do not need to take into consideration which packets traverse the Internet, and which do not.
Table 10: VMware Products for Encryption of Transport Protocol
| Features | Products |
| Blast Extreme protocol | Horizon |
| Blast Secure Gateway | Unified Access Gateway |
Within VMware Horizon®, there are multiple communication flows, including for client authentication, client remote protocol, agent status updates, synchronization, and more. All of these leverage AES encryption by default. For TCP communication, the key exchange is done with TLS symmetric public-key cryptography.
The use of the Blast Extreme display protocol on Unified Access Gateway is recommended:
- The Blast Extreme protocol uses the fewest security algorithms.
- The Blast Extreme protocol supports AES (Advanced Encryption Standard) encryption, where all TCP connections support TLS 1.1 and 1.2, and all UDP connections are encrypted with DTLS encryption.
- The Blast Secure Gateway component ensures that the only traffic that can enter the corporate data center is traffic on behalf of a strongly authenticated user. End users can access only the resources that they are authorized to access.
Because a Zero Trust approach does not distinguish between internal and external networks, it is all the more important to determine the proper security protocols and cipher suites to use for encrypting communication between clients and the Unified Access Gateway appliance.
TLS 1.2 is the cryptographic protocol recommended to protect data being transferred between endpoints by verifying connection security and performing “handshake” authentication between a client and the appliance. For cryptographic algorithms, the use of the following cipher suites significantly increases security over TLS communication:
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
When performing scanning tests against Unified Access Gateway HTTP communication over TLS (TCP 443) using the combination of TLS 1.2 and the above ciphers, Unified Access Gateway achieves a score of A+ and compliance with the following:
- PCI DSS requirements:
- Finance Industry (Payment Card Industry Data Security Standard)
- PCI DSS 3.2.1 - Requirements 2.3 and 4.1
- HIPAA guidance:
- Healthcare Industry (Health Insurance Portability and Accountability Act of 1996)
- HIPAA of 1996, Guidance Specifying the Technologies and Methodologies that Render Protected Health Information Unusable, Unreadable, or Indecipherable to Unauthorized Individuals
- NIST guidelines:
- Federal Agencies (National Institute of Standards and Technology)
- Reference: NIST Special Publication 800-52 Revision 2 - Section 3.
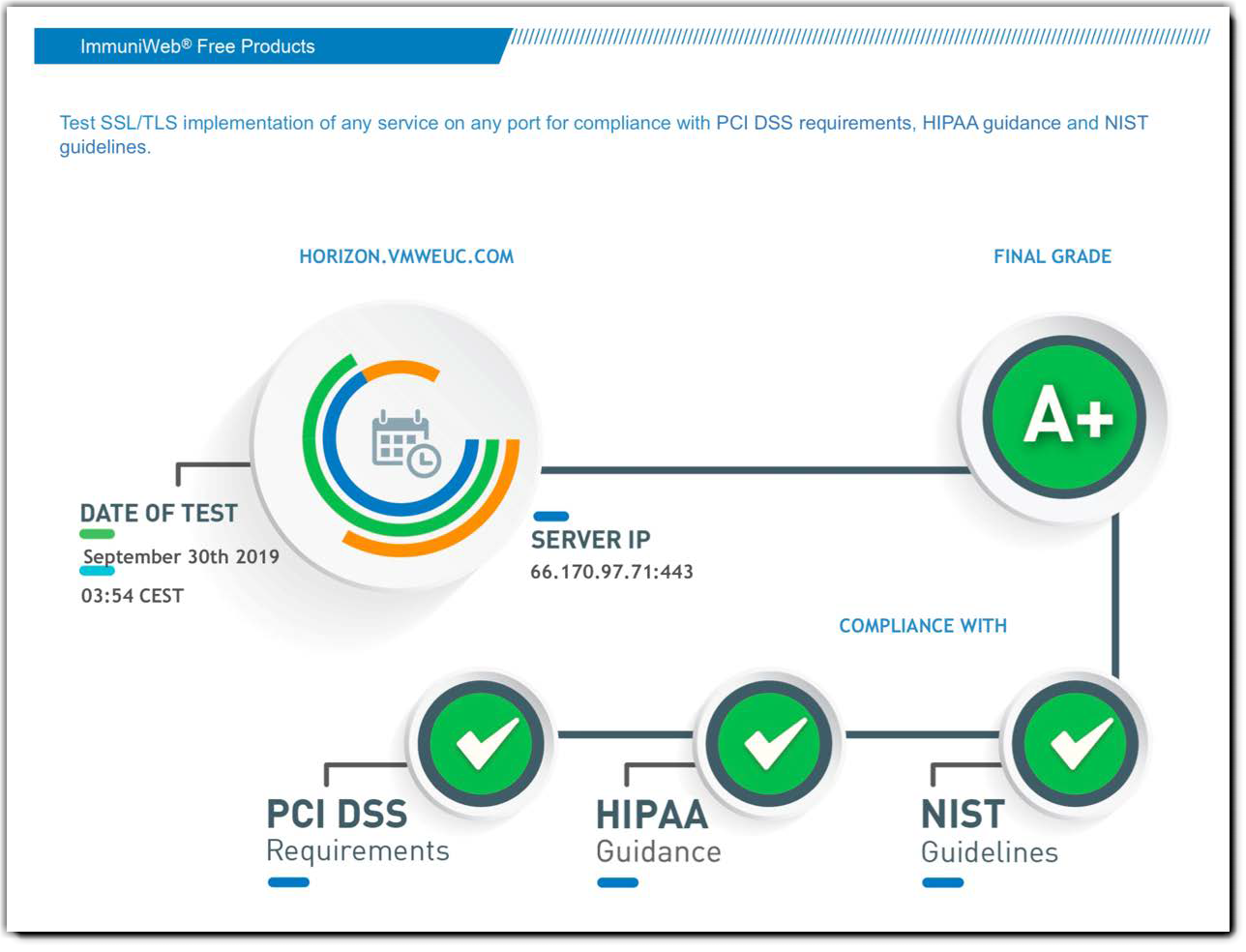
Figure 8: Unified Access Gateway 3.7 Scan Rating Report Compiled by ImmuniWeb
For information about how Unified Access Gateway performs JWT artifact validation for Horizon launches through SAML, see Single Sign-On.
Session Protection
A session is a temporary connection between two devices or between a user and a computer during which information is communicated and exchanged. To avoid having a session hijacked, several security measures can be used:
- You must have an effective authentication system and only allow sessions from authenticated users and compliant devices.
- Communication must be encrypted, so that even after the user is authenticated, no one will be able to steal the session ID used to pass subsequent communications back and forth.
- An expiration period must be defined, limiting the amount of time malicious actors have to make their hijack attempts.
Table 11: VMware Products for Session Protection
| Features | Products |
| Secure gateway | Unified Access Gateway |
| Horizon Smart Policies | Dynamic Environment Manager |
| Risk Scoring | Workspace ONE Intelligence |
| NSX Data Center | NSX-T Data Center |
Session Expiration with Unified Access Gateway
Unified Access Gateway will only forward traffic to the backend network if it is on behalf of an authenticated user. In addition, by enabling the Endpoint Compliance Check Provider settings and integrating with Workspace ONE Intelligence, we can check the posture of the user’s device before allowing further access. Workspace ONE Intelligence provides several levels of severity and based on the level sessions are allowed through or blocked. The risk score is carried through to the virtual application and can be leveraged for by the Dynamic Environment Manager to restrict the session.
Then the Horizon protocols (Blast Extreme and PCoIP) will only be forwarded to desktops and hosts that the user is authorized to access. Any protocol traffic received by Unified Access Gateway that is not on behalf of an authenticated user is discarded by Unified Access Gateway and is not forwarded.
The launch of a virtual application opens a secondary connection based on the display protocol (Blast, PCoIP), allowing the user to stay connected for to up to 10 hours (default). The session interval is configurable on Unified Access Gateway but must be aligned with the re-authentication time period defined in Workspace ONE Access policies. Together, these settings enforce the re-authentication process periodically. In general, we recommend shortening the session time to live period as much as is acceptable to your end users. A shorter TTL period allows for more frequent validation of the user sessions.
Restriction of User Behaviors Based on Session Conditions
With VMware Dynamic Environment Manager™ (formerly called User Environment Manager), you can configure Horizon Smart Policies to turn off remote features that might pose a security risk when using VDI or published desktops or applications. Horizon Smart Policies are applied during login and can be refreshed when a user attempts to reconnect to a session. Smart Policies can be based on conditions such as client location, client IP, user group, pool name, or the above-mentioned device risk score.
The following remote user experience features can be controlled:
- Audio – Enable or turn off audio playback.
- Display protocol – Choose protocol, quality, frame rate, bandwidth.
- Drag and drop – Enable or turn off dragging and dropping of files and choose directions (from client device to virtual desktop, or the reverse, or both).
- Printing – Enable or turn off printing.
- Redirection (client drive, clipboard, USB) – Enable or turn off redirection and choose direction for clipboard.
- File transfer – Enable or turn off web/Chrome file transfer.
Intrusion Detection and Prevention
NSX Data Center allows for the insertion of advanced third-party security services that are permitted to inspect the network traffic of a virtual machine. The services typically provide advanced security features such as an intrusion detection system (IDS) or an intrusion prevention system (IPS).
Advanced service insertion allows the third-party solution to examine the traffic for behavior that breaches policy and take appropriate action if necessary.
Application Trust
In the best of worlds, applications would be designed from the ground up with Zero Trust in mind. This is a very rare occurrence today. We must do the best with what we have. We can enhance the security posture of an application using the transport and session trust enhancements discussed in previous chapter, and add to that a change in the way we authenticate into the applications.
In this use case, where we are focusing on traditional applications, we must address the most common authentication method used, on-premises Microsoft Active Directory (AD) login. The traditional AD login system does not translate to a Zero Trust design very well. It is hard for users to perform an AD login when they are not connected to a traditional internal LAN.
We need a passwordless authentication method and federation that is designed for the Internet and the cloud. The most common federation protocols used include SAML and OpenID Connect, together with OAuth2.
For this use case, we enhance the flow of user authentication by enabling modern SAML federation in a Windows application or desktop. This allows for a greater flexibility of authentication methods to be used. With the federation the user will gain seamless access to the Windows application no matter which authentication method we have chosen.
The rest of the sections in this chapter provide more detail about the various elements of application trust:
Single Sign-On
Single sign-on (SSO) means that a user authenticates to a system once and then can access many related but separate systems without having to re-authenticate for the duration of the session. SSO has many benefits, including improving the user experience, reducing helpdesk requests, and improving compliance through using a centralized database.
One means of providing SSO is by using SAML (Security Assertion Markup Language), an XML-based standard. SAML passes information about users between identity providers and service providers in XML documents called SAML assertions. In our solution, the integration between Workspace ONE Access and Horizon makes use of SAML for user authentication. With the Horizon True SSO feature, short-lived certificates are used, rather than usernames and passwords, to manage the login process to virtual applications and desktops.
Table 12: VMware Products for Single Sign-On
| Features | Products |
| True SSO | Workspace ONE Access Horizon |
| SAML | Workspace ONE Access Unified Access Gateway |
Ordinarily, using any authentication mechanism other than AD credentials would prevent SSO to Horizon virtual desktop or published application. If a user first logged in with anything other than AD credentials, after selecting a desktop or published application from the Workspace ONE catalog, the user would be prompted to authenticate again, this time with AD credentials.
However, with the federation of Horizon into Workspace ONE Access, we can perform true single sign-on to a Windows published application or desktop. Horizon True SSO uses SAML, where Workspace ONE Access is the identity provider (IdP), and the Horizon Connection Server is the service provider (SP).
Note: Although our solution can integrate with other existing federation solutions such as Microsoft AD FS and Okta, because this use case includes Horizon virtual applications and desktops, Workspace ONE Access must be used as a part of the authentication chain.
Unified Access Gateway provides additional security. When users launch a virtual application from the Workspace ONE catalog, a SAML JWT (JSON Web Token)–encoded artifact is generated by Workspace ONE Access. This artifact is used by the VMware Horizon® Client™ XML-API request.
Unified Access Gateway identifies this incoming request and performs a validation of the SAML JWT– encoded artifact:
- If the request is valid, Unified Access Gateway forwards traffic to the backend network on behalf of the authenticated user.
- If the request is not valid, the request is dropped.
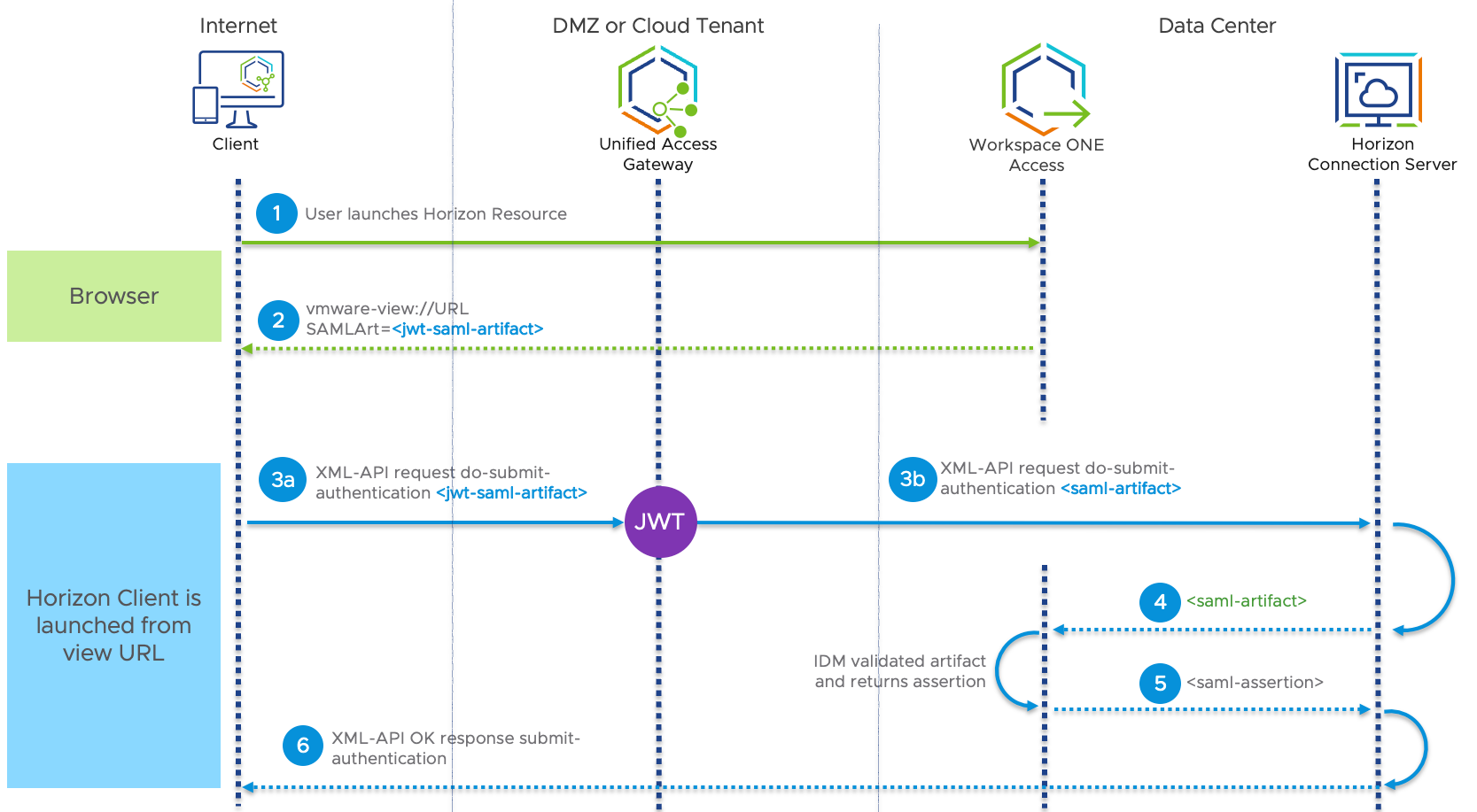
Figure 9: SAML JWT-Encoded Artifact Processing Flow for Workspace ONE Access to Horizon Connection Server
- From the client endpoint, the user selects a Horizon desktop or published application from the Workspace ONE catalog.
- Workspace ONE Access generates a SAML artifact and assertion. These are the access tokens that allow the user access to Horizon resources.
- (a) The Horizon Client sends an authentication request along with the SAML JWT-encoded artifact and vmware-view URL to Unified Access Gateway for validation. (b) Unified Access Gateway receives the SAML artifact and validates its JWT settings to make sure it comes from a trusted identity provider before forwarding the authentication request with SAML artifact on to the Horizon Connection Server.
- The Connection Server performs SAML artifact resolution by sending an artifact resolution request to Workspace ONE Access.
- After validating the artifact, Workspace ONE Access returns the assertion.
- The client is allowed to access the Horizon resource.
Application Access from Any Device
Enabling employees to securely and seamlessly access any application, including traditional Windows applications, from any device is key to creating a digital workspace and enforcing Zero Trust. With flexibility of work tools and freedom of access from anywhere at any time, digitally empowered employees become more engaged and productive. They can collaborate with team members more easily and make faster decisions.
Table 13: VMware Products for Application Access from Any Device
|
Features |
Product |
| Application publishing VDI | Horizon |
Using Horizon published applications simplifies management of line-of-business applications, allows the delivery of Windows applications to non-Windows devices, and can potentially provide licensing advantages.
With Horizon published applications, IT installs applications on servers with the Microsoft Remote Desktop Session Host (RDSH) role, and then entitles applications to corporate users through the Horizon administration console. Once authenticated, users can launch an application, save files, and use network resources from a remote RDSH server—just as if the users had the application installed on their local computer, tablet, or phone.
Selecting an application opens a window for that application on the local client device, and the application looks and behaves as if it were locally installed. For example, on a Windows client computer, an item for the application appears in the taskbar and looks identical to the way it would look if it were installed on the local Windows computer. Users can also create shortcuts for published applications, and the shortcuts appear on the client desktop, just like shortcuts for locally installed applications.
VMware Horizon Client software is available for Windows, macOS, and Linux desktops and laptops; iOS and Android phones and tablets; Chromebooks; and even browsers or thin/zero clients, allowing users to access applications from any device.
Figure 10: Windows Applications Accessible from Any Device
Data Trust
At the end of the day, it is the data that is of utmost importance—the whole reason we need strong security. We must protect against data breaches and leaks, and make sure it is the correct, unmodified data that our users are interacting with. Although data classification and integrity is, for the most part, handled by the application itself, we should enhance the trust level wherever we can when building a Zero Trust architecture.
In this specific use case, we do not handle the data directly. The data is hosted in the data center and should never be allowed to leave it. We need to apply policies that make it as difficult as possible for users to perform prohibited actions. For example, to prevent users from accidentally leaking sensitive data, we might set a policy that removes their ability to copy and paste text and graphics from the remote session into their local system.
Protection of Data at Rest
Data at rest, as compared with data in transit, is data that is being stored on a stable medium such as a hard drive, laptop, flash drive, or some other storage medium. Previously, using antivirus software and firewalls was thought to do an adequate job of protecting data at rest. With the Zero Trust model, however, software-defined perimeters are increasingly being used to create a protective casing around data access.
Security teams must of course continue to implement security practices that keep unauthorized users out of the data center and away from the data stored there. But because data must now also be protected from lateral attacks inside the corporate network, data must be segmented and isolated from other data using micro-segmentation. Network segments can then serve as trust boundaries.
Other elements of protection include using strong encryption for sensitive files or even the entire storage drive. IT must also take into consideration whether to allow end users to attach a flash drive or other removable device and get data in an unencrypted form.
Table 14: VMware Products for Protection of Data at Rest
| Features | Products |
| Published applications VDI | Horizon |
| Horizon Smart Policies | Dynamic Environment Manager |
With Horizon, sensitive data is able to remain within the data center and be accessed only remotely, using a virtual machine or remote application session. This eliminates the need to store data on a mobile device such as a phone or laptop and also allows for separation of work and personal data.
Both traditional firewalls and micro-segmentation add protection to contain data to only the components required.
With Dynamic Environment Manager, you can create Horizon Smart Policies that control the behavior of features often used in Horizon desktop or application sessions. Horizon Smart Policies are applied during login and can be refreshed whenever the user attempts to reconnect to a virtual desktop or published application. For example, Smart Policies can prevent file transfer and clipboard functionality based on conditions such as client location, client IP, user group, pool name, and more.
Visibility and Analytics
To implement a solution that follows the Zero Trust tenet, “never trust, always verify, enforce least privilege,” you need a system that gives you visibility by logging all traffic. This information can then be used to learn and monitor network patterns. The resulting analytics help you make effective dynamic policy and trust decisions.
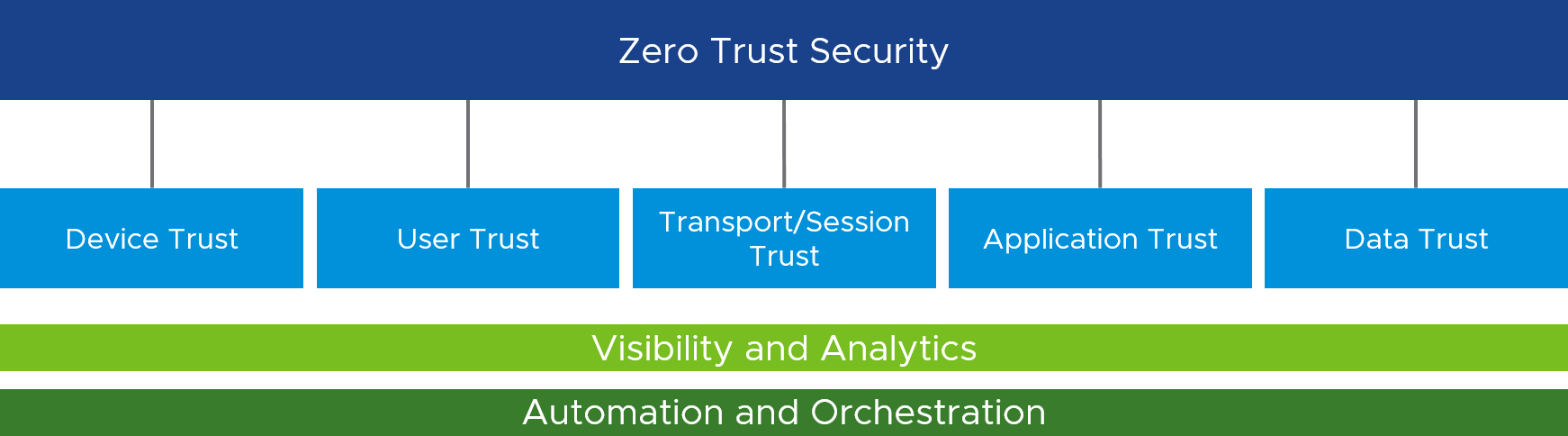
Figure 11: By Establishing Trust Across the Five Pillars, You Gain Visibility and Analytics
The sections that follow describe, for each product, the features that give you visibility and help you analyze behavior.
Horizon
The Horizon Help Desk Tool is a web application that you can use to troubleshoot problems with user sessions and perform desktop maintenance operations such as restarting or resetting virtual desktops or RDSH servers.
You can use the dashboard in the Horizon Console to quickly see problems that might affect the operation of Horizon or problems that affect access to remote desktops by end users. For example, the System Health dashboard allows you to monitor many components of the system:
- vCenter Server VMs
- RDSH server farms and the hosts included in each
- Events database
- Other Horizon and vSphere components and remote pods
The Sessions dashboard displays information about the status of remote desktop and application sessions. For a complete list of the information displayed in the dashboard, see Monitor VMware Horizon Components, in the Horizon Administration guide.
Unified Access Gateway
Unified Access Gateway provides a collection of logs and that cover all the services available on the appliance. The logs are available through the administration console or REST API.
Unified Access Gateway also offers Syslog integration for log retention and centralized analyses. Administrators can configure one Syslog server to collect administration events and a second one to monitor the overall activity of the Unified Access Gateway appliance, including information from each edge service. All these types of logs can be integrated and replicated to a Syslog server for auditing purposes.
Monitoring information regarding current active sessions is provided in real-time through the Unified Access Gateway Administration Console. This console shows the number of active sessions per edge service. A REST API is also available and can provide additional information from each edge service as well as the overall appliance.
Workspace ONE Access
Within Workspace ONE Access, administrators can quickly get an overview of the number of logins, application adoption, and more using the user engagement dashboard.
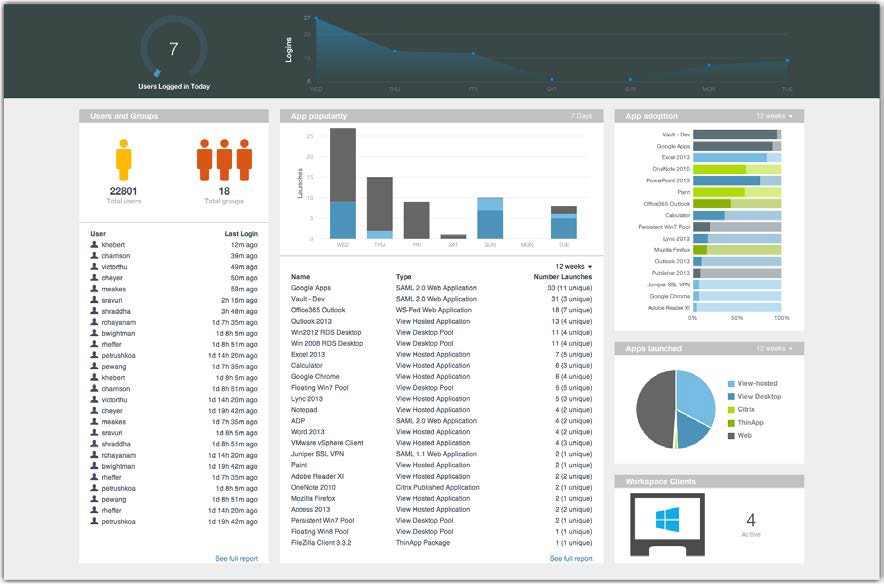
Figure 12: Workspace ONE Access Engagement Dashboard
From within the same console, you can search and view audit and event logs. These help with troubleshooting and validating the overall health of your implementation.
You can add an external Syslog server to collect logs in a central location and analyze events that occur on the Workspace ONE Access Connector, which is the on-premises component.
Workspace ONE UEM
The Console Monitor in Workspace ONE UEM is your central portal for access to critical information. Its bar charts and donut graphs help you quickly identify important issues and take action.
The Monitor > Overview page from the Workspace ONE UEM console provides summary graphs and detailed views for the following:
- Devices – Number of devices, broken down by status, platform, and enrollment history.
- Compliance – List of devices that violate compliance policies, with policy details, and list of top violated policies and application groups; for example, denylisted apps, required apps.
- Profiles – Latest profile version, list of profiles that are out of date, and devices that have old versions of each profile.
- Apps – Latest application version, list of most installed apps, and list of devices that have old versions of each app.
- Content – Latest content version and list of devices with content that is out of date.
- Email – List of devices blocked from email, including devices blocked by default, denylisted, or unenrolled from Workspace ONE UEM.
- Certificates – List of expired certificates and certificates expiring soon, along with the expiration periods.
After you create device profiles, compliance policies, managed applications, and other managed content, you can leverage dedicated dashboards and configuration screens to manage these settings one at a time and remotely from a single source.
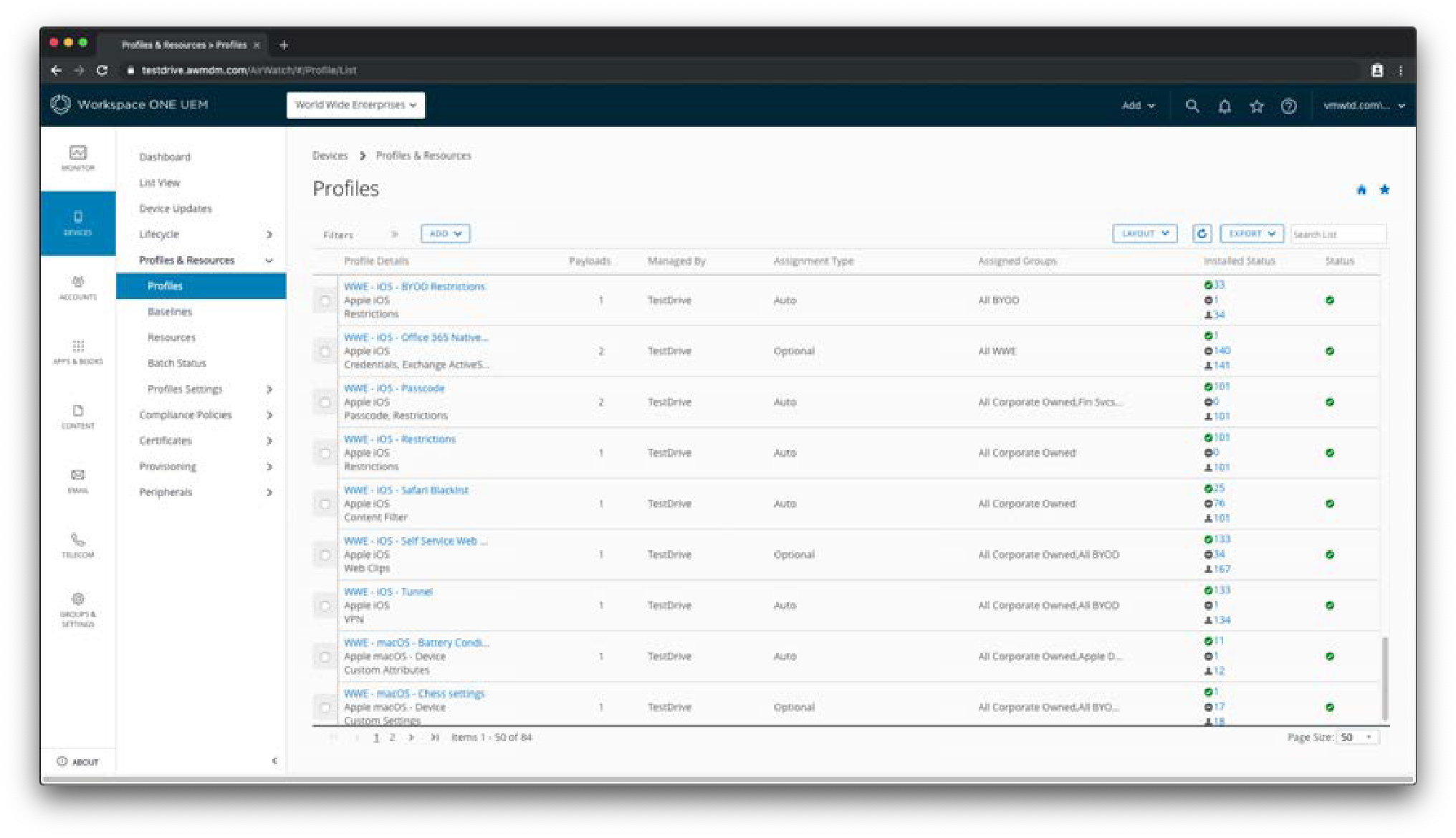
Figure 13: Device Profiles List in the Workspace ONE UEM Console
This screenshot shows the Devices > Profiles & Resources > Profiles page from the Workspace ONE UEM console. Similar pages exist for Application, Content, Email, and Telecom Management with features like filters, layout, and column sorting.
Workspace ONE UEM records administrative and device actions in terms of console events and device events:
- Console events show actions taken from the Workspace ONE UEM console, including login sessions, failed login attempts, admin actions, system settings changes, and user preferences.
- Device events show the commands sent from the Workspace ONE UEM console to devices, device responses, and device user actions.
For more information, see Use Console Events and Use Device Events in the Workspace ONE UEM documentation.
Workspace ONE Intelligence
Workspace ONE Intelligence provides a rich set of capabilities across devices and users. Administrators receive real-time analytics and visibility through reports and dashboards on device posture, user engagement, application deployment and utilization, and threats.
Trust Network integration in Workspace ONE Intelligence brings together threat data from different security solutions such as Mobile Threat Defense (MTD), end-point protection and remediation (EDP/EDR) and Cloud Access Security Broker (CASB) in a single console. Trust Network insights allow IT and information security (InfoSec) teams to observe in real time what is happening in the environment so that they can make the best remediation decisions.
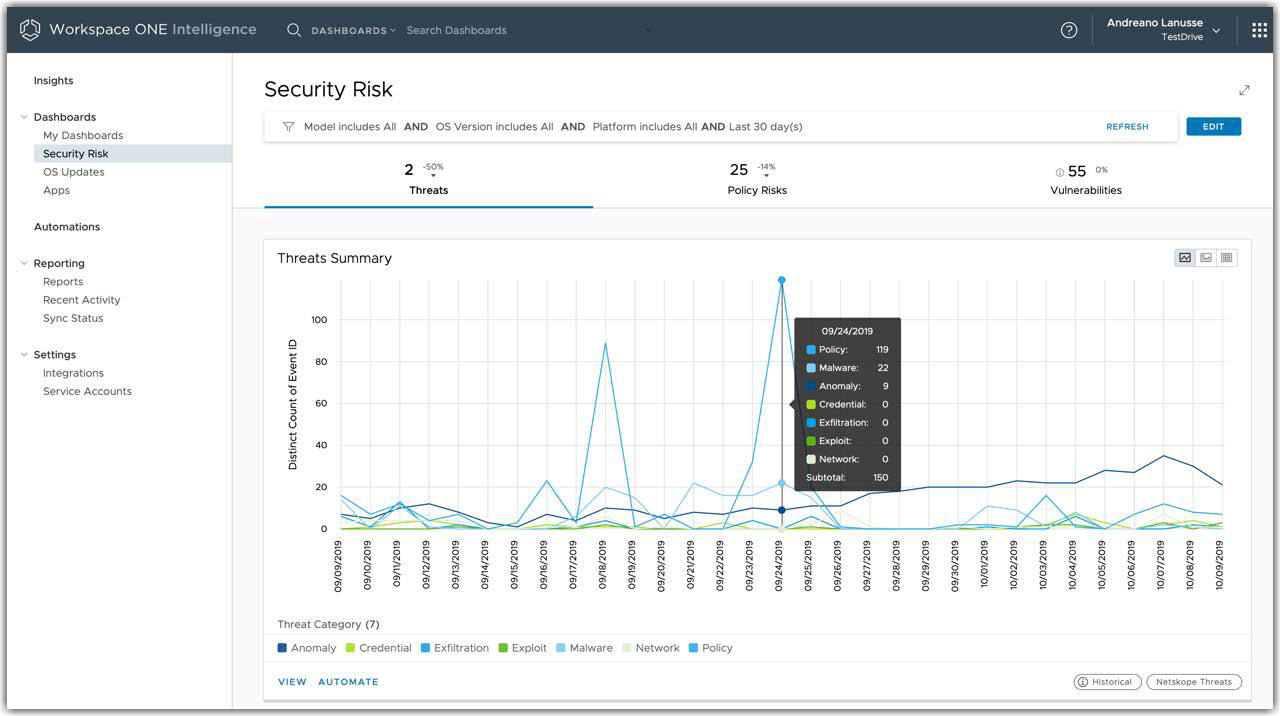
Figure 14: Security Risk Dashboard in the Workspace ONE Intelligence Console
Within the Workspace ONE Intelligence console, administrators can easily customize dashboards to:
- Identify anomalous behavior related to the authentication process through Workspace ONE Access.
- Analyze application utilization.
- Perform real-time troubleshooting without requiring access to server logs, and so on.
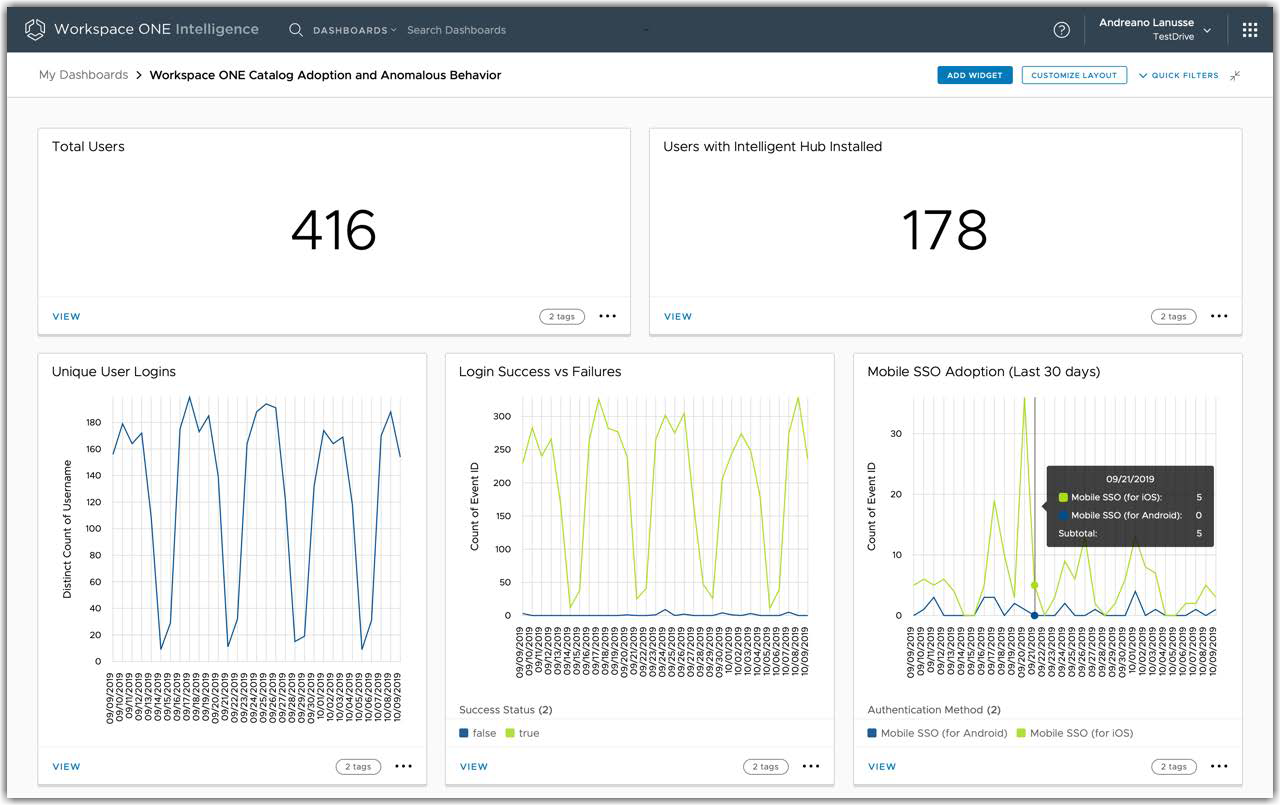
Figure 15: Workspace ONE Catalog Adoption and Anomalous Behavior Dashboard
Workspace ONE Intelligence correlates daily OS update data from managed Windows 10 devices and correlates that data to CVEs, allowing administrators to easily identify all vulnerable devices and prioritize patch management based on the CVSS score.
Note: Syslog integration is also available for Workspace ONE Intelligence.
Automation and Orchestration
With visibility and analytics, as described in the previous chapter, we can build automation and orchestration. Workspace ONE and Horizon platform services allow us to collect contextual information from across the entire environment. This contextual awareness feeds intelligence, allowing us to make just-in-time decisions, and use automation for threat remediation.
The sections that follow describe the automation features for Workspace ONE UEM and Workspace ONE Intelligence.
Workspace ONE UEM
The compliance engine is an automated tool by Workspace ONE UEM that ensures all devices abide by your company’s policies. These policies can include basic security settings such as requiring a passcode and having a minimum device lock period.
For certain platforms, you can also enforce certain precautions. For example, you can set password strength, denylist certain apps, and configure device check-in intervals to ensure that devices are safe and in regular contact with Workspace ONE UEM.
How the Compliance Engine Works
If devices are found to be out of compliance, the compliance engine warns users to address compliance errors to prevent disciplinary action on the device. For example,
the compliance engine can trigger a message to notify the user that their device is out of compliance.
In addition, a device that is not in compliance cannot have device profiles assigned to it and cannot have apps installed. If corrections are not made in the amount of time specified, the device loses access to certain content and functions that the admin defines. The available compliance policies and actions vary by platform.
You can automate escalations when corrections are not made, for example, by locking down the device and notifying the user to contact IT to unlock the device. These escalation steps, disciplinary actions, grace periods, and messages are all customizable with the Workspace ONE UEM console.
REST APIs for Integration with External Programs
Workspace ONE UEM provides a collection of RESTful APIs that allow external programs to use the core product functionality by integrating the APIs with existing IT infrastructures and third-party applications. Leveraging the simplified REST style of software architecture, Workspace ONE UEM REST APIs currently support a multitude of functionalities, including organization group, console administration, mobile application, mobile device, email, user enrollment, profile, smart group, and user group management.
Workspace ONE UEM offers event notifications so that you can configure settings to capture specific device-related events in real time. It uses Webhooks, which are HTTP callbacks to send event-specific information to the configured URL in JSON or XML format. This eliminates the need to constantly poll the API server for a specific event or attribute.
You can leverage REST APIs and event notifications to build a customized automation flow. For example, by subscribing to event notifications for Device Compliance Status Change, you can invoke automatic corrective actions on noncompliant devices.
Workspace ONE Intelligence
Workspace ONE Intelligence leverages the Workspace ONE UEM compliance engine, which allows for continuous monitoring of all ingested data. This data includes information from all managed devices, applications, device sensors, OS updates, identity authentication requests, and threats.
Workspace ONE Intelligence adds an automated process capability across the environment by defining rules and actions based on a wide range of parameters. This allows administrators to create contextual workflows that will take automated remediation actions based on ongoing or recent security threats. Compliance requirements are similarly met through automated access control.
For example, administrators can create an automation based on high-severity threat events that identity suspicious behavior across devices and users. Impacted devices can be automatically placed in quarantine in the Workspace ONE UEM system. Workspace ONE Intelligence can notify IT and InfoSec through Slack and create a Service Now incident ticket to initiate an investigation on the impacted devices.
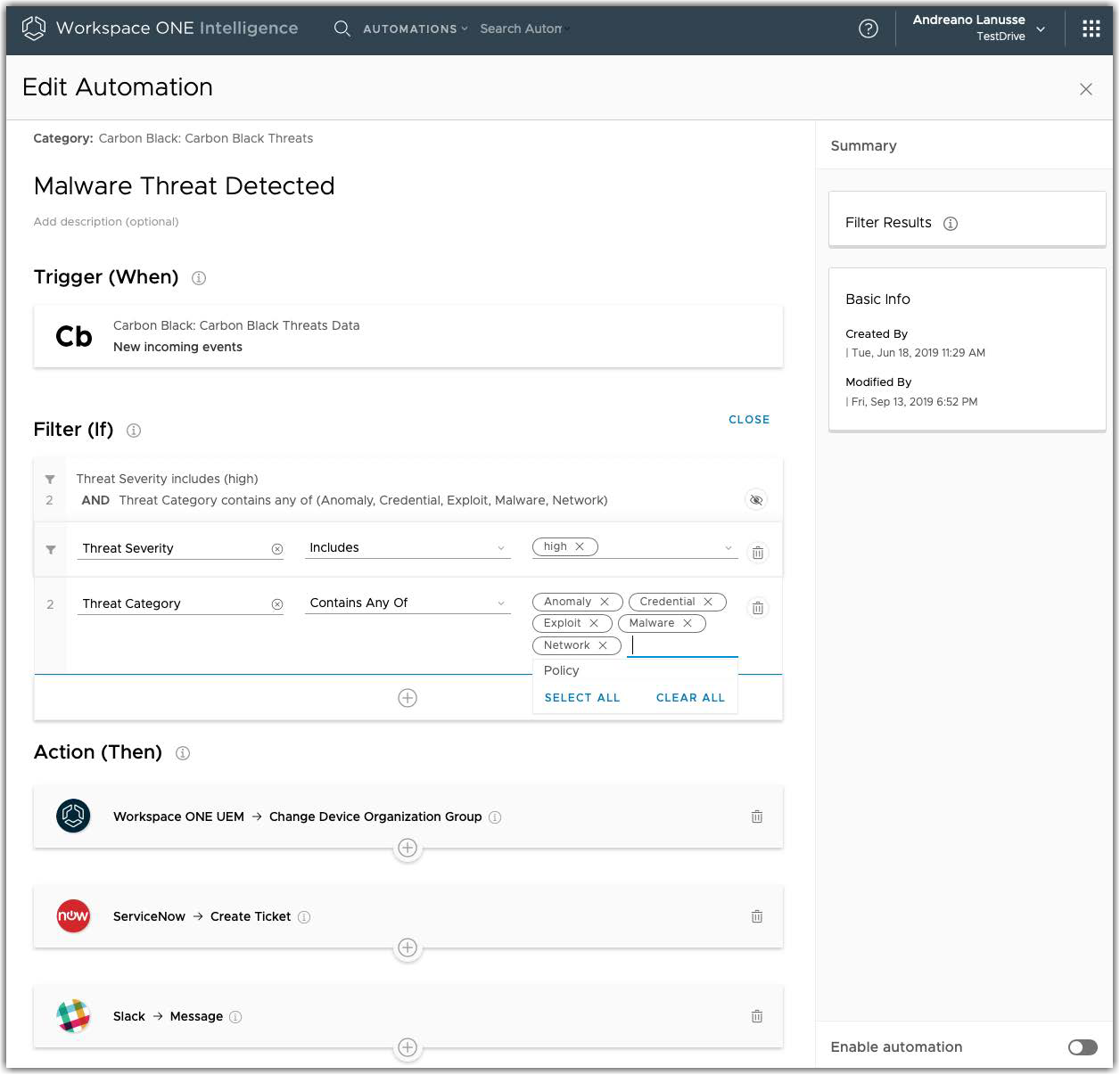
Figure 16: Example of an Automation to Detect and Respond to Real-Time Threats
Administrators can also leverage automation to identity all managed Windows 10 devices that are missing critical CVEs (Common Vulnerabilities and Exposures) based on CVSS (Common Vulnerability Scoring System) and automate approval for installing the correlated patches (Microsoft KBs).
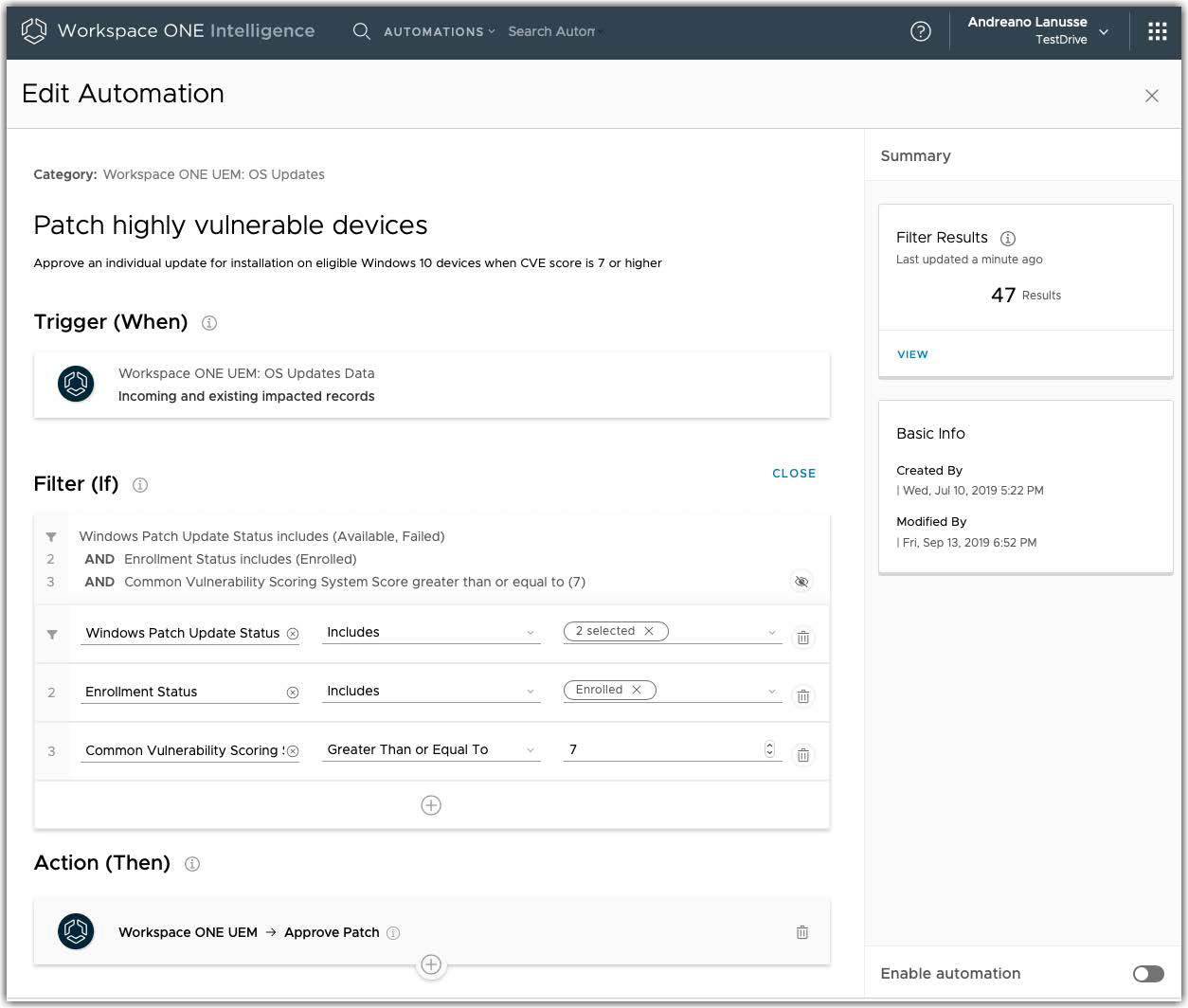
Figure 17: Example of an Automation for Patching Vulnerable Windows 10 Devices
Zero Trust Solution for Horizon Applications
The following diagram shows how the various Workspace ONE and Horizon components interact to build an end-to-end solution that incorporates the following Zero Trust elements:
- Verification of device compliance
- Conditional, least-privilege access
- Certificate-based and multi-factor authentication
- Single sign-on
- Micro-segmentation of networks
- Automated real-time threat detection and remediation
- Encryption
- Session protection
- Protection of data at rest
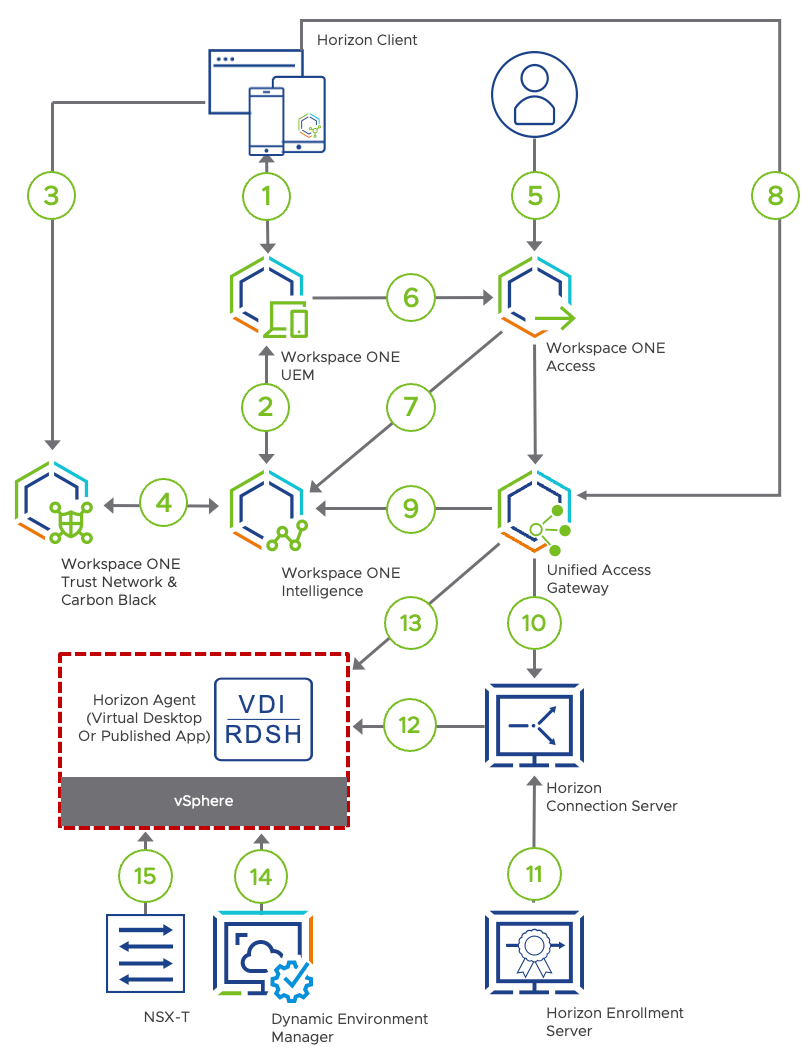
Figure 18: Logical Flow
The numbers in this diagram correspond to the following actions:
- Device enrolls in the management system by using Workspace ONE Intelligent Hub. After the device is enrolled, Workspace ONE UEM sends management profiles, device certificates, and user certificates to the device. The device periodically reports its device posture so that Workspace ONE UEM can validate the device against the configured compliance rules.
- Workspace ONE UEM sends device information to Workspace ONE Intelligence. Intelligence can now use this device data to detect threats and instruct Workspace ONE UEM to carry out remediation actions.
- Trust Network agent is deployed to protect endpoint devices and remediate threats. When a threat is identified, the agent sends and stores the related threat information in the Trust Network Cloud repository.
- Workspace ONE Intelligence queries the Trust Network repository every 30 seconds for any newly reported threats on the device. Workspace ONE Intelligence then stores threat information on the Intelligence Cloud Service for unified visibility and automation. In this step, automation actions are triggered if the incoming threat data matches the condition defined for an automation.
- When the user tries to access anything protected by our Zero Trust solution, the user must first pass through the conditional access mechanism of Workspace ONE Access. When Workspace ONE Access prompts the user for authentication, this process is seamless because we use certificate-based authentication.
Note: If a stronger method of authentication is required, additional authentication methods can be used, such as multi-factor authentication. Also, it is important to configure the session’s time to live to fit your Zero Trust user validation policies. - During certificate-based user authentication, Workspace ONE Access also collects the device UUID from the certificate. With this information, Workspace ONE Access can request the status of the device from Workspace ONE UEM.
In order for the user to be allowed access, Workspace ONE UEM must report the device as being compliant according to your organization’s policy settings. - Once the user successfully passes the conditional access rules and launches the application, Workspace ONE Access feeds these audit events to Workspace ONE Intelligence.
- Workspace One Access generates a SAML artifact and assertion. These are the access tokens that allow the user access to Horizon resources. The authentication request is sent forward, using the SAML artifact, to the Unified Access Gateway.
- The SAML artifact is wrapped in XML-API do-submit-authentication request from the Horizon Client and that includes the MDM Device ID, which is used by the Unified Access Gateway to request the risk score from Workspace ONE Intelligence.
- Unified Access Gateway receives the SAML artifact and validates its JWT token settings to make sure it comes from a trusted identity provider. The Connection Server is passed the SAML artifact, performs a SAML resolve against Workspace ONE Access, which validates the artifact and returns an assertion. The Connection Server is then able to validate the identity of the user and to check entitlements.
- The Horizon Enrollment Server is used to enable single sign-on to the Horizon published application or virtual desktop. The Enrollment Server receives certificate-signing requests from the Connection Server and then passes them to the trusted Certificate Authority to generate a short-lived certificate on behalf of the user.
- Horizon Agent software service is installed on the guest OS of all target VMs, physical systems, or RDSH servers. This agent allows VMs to be managed by Connection Servers and allows a Horizon Client to establish a protocol session to the target VM. The short-lived certificate, which was generated as described in the previous step, is passed to the Windows operating system to log the user in.
- Connection to VDI is established using the session protocol.
- Dynamic Environment Manager sets Horizon Smart Policies that control the behavior of remote features of a Horizon desktop or published application session based on client information like type, IP address or risk score.
- NSX-T Data Center applies micro-segmentation firewall policy based on the user identity. This enacts the principle of least-privilege access to the transport level.
Implementation
The VMware Workspace ONE and VMware Horizon Reference Architecture guide provides a framework and guidance for architecting using Workspace ONE and Horizon. Design guidance is given for the products used in this Zero Trust use case, with each product having a chapter.
- Workspace ONE UEM Architecture
- Workspace ONE Access Architecture
- Workspace ONE Intelligence Architecture
- Horizon Architecture
- Unified Access Gateway Architecture
Our primary driver for utilizing NSX-T Data Center is to enable the principle of least-privilege access at the transport level by using identity-based firewalls. For details on designing and implementing NSX-T Data Center with Horizon, see the NSX-T Data Center and EUC Design Guide.
Several integration and configuration points need to be considered to make the separate products deliver the desired Zero Trust architecture and to provide a complete platform. The integration points are covered in the Platform Integration chapter of the VMware Workspace ONE and VMware Horizon Reference Architecture guide.
The following diagram, along with the remainder of this chapter, covers the necessary points of integration that need to be set up.
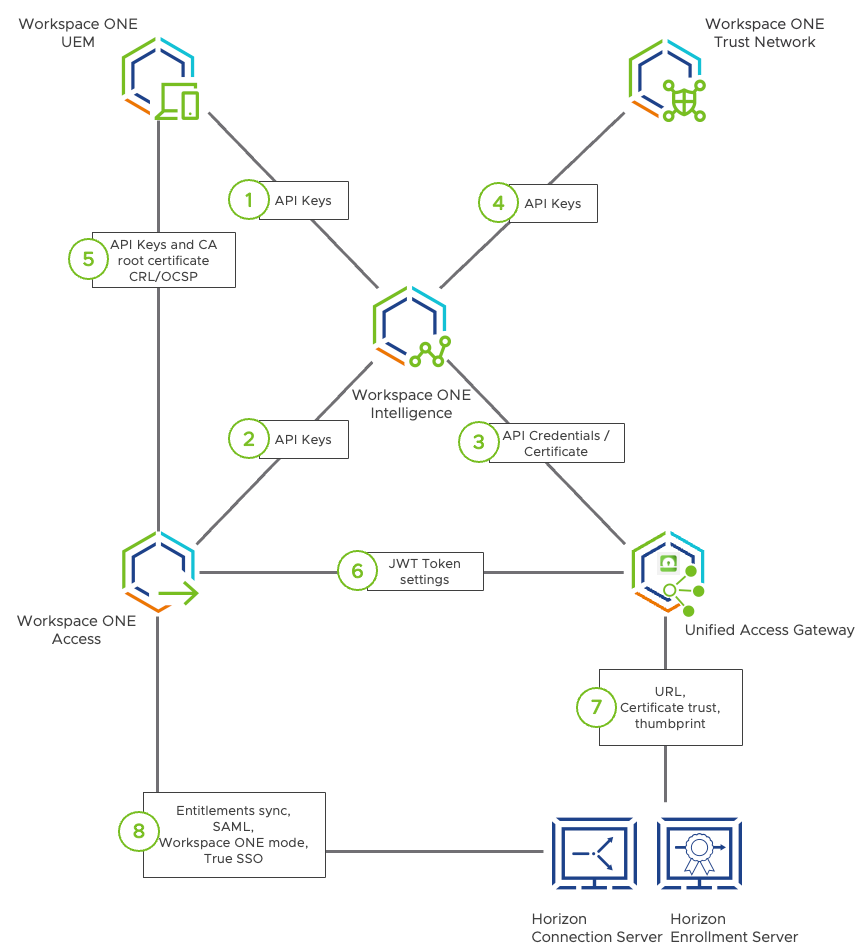
Figure 19: Integration and Configuration Points
The circled numbers in the preceding diagram correspond to the rest of the sections in this chapter:
- Workspace ONE Intelligence and Workspace ONE UEM
- Workspace ONE Intelligence and Workspace ONE Access
- Workspace ONE Intelligence and Unified Access Gateway
- Workspace ONE Intelligence and Trust Network
- Workspace ONE UEM and Workspace ONE Access
- Unified Access Gateway and Workspace ONE Access
- Unified Access Gateway and Horizon
- Workspace ONE Access and Horizon
Workspace ONE Intelligence and Workspace ONE UEM
Core integration of Workspace ONE Intelligence involves enabling endpoint analytics. This feature provides capabilities that are crucial for device trust. Endpoint analytics use automated workflows involving the devices, and can offer insights on all managed devices by generating reports and dashboards.
The reference architecture guide provides details on Workspace ONE UEM and Workspace ONE Intelligence Integration, which includes using the Workspace ONE Intelligence Connector service. This service collects data related to devices, apps, sensors, and OS updates from your Workspace ONE UEM database and pushes this data to the cloud-based Intelligence service.
Note: For this use case, we used cloud-based Workspace ONE UEM, which is enabled by default.
To allow Workspace ONE UEM to access Workspace ONE Intelligence you must opt into the Workspace ONE Intelligence Cloud Service. See Access Workspace ONE Intelligence, in the VMware Workspace ONE Intelligence Products documentation.
Another important integration point is the Automation Connector, which enables the platform to take actions based on automation conditions. Enabling integration with Workspace ONE UEM is key to automating remediation actions on managed devices. For instructions, see the video VMware Workspace ONE Intelligence: Automation Connectors - Feature Walk-through.
Workspace ONE Intelligence and Workspace ONE Access
Integration between Workspace ONE Intelligence and Workspace ONE Access enables identity analytics capabilities on Workspace ONE Intelligence. Identity analytics provide insights on user logins and application launch events generated by Workspace ONE.
The reference architecture guide provides details in the chapter Workspace ONE Access and Workspace ONE Intelligence Integration.
Workspace ONE Intelligence and Unified Access Gateway
To enable Workspace ONE Intelligence (Risk Analytics) as Endpoint Compliance Check Provider for Horizon, as well as pushing analytics data from the Unified Access Gateway into Workspace ONE Intelligence, initially an integration needs to be set up between both solutions.
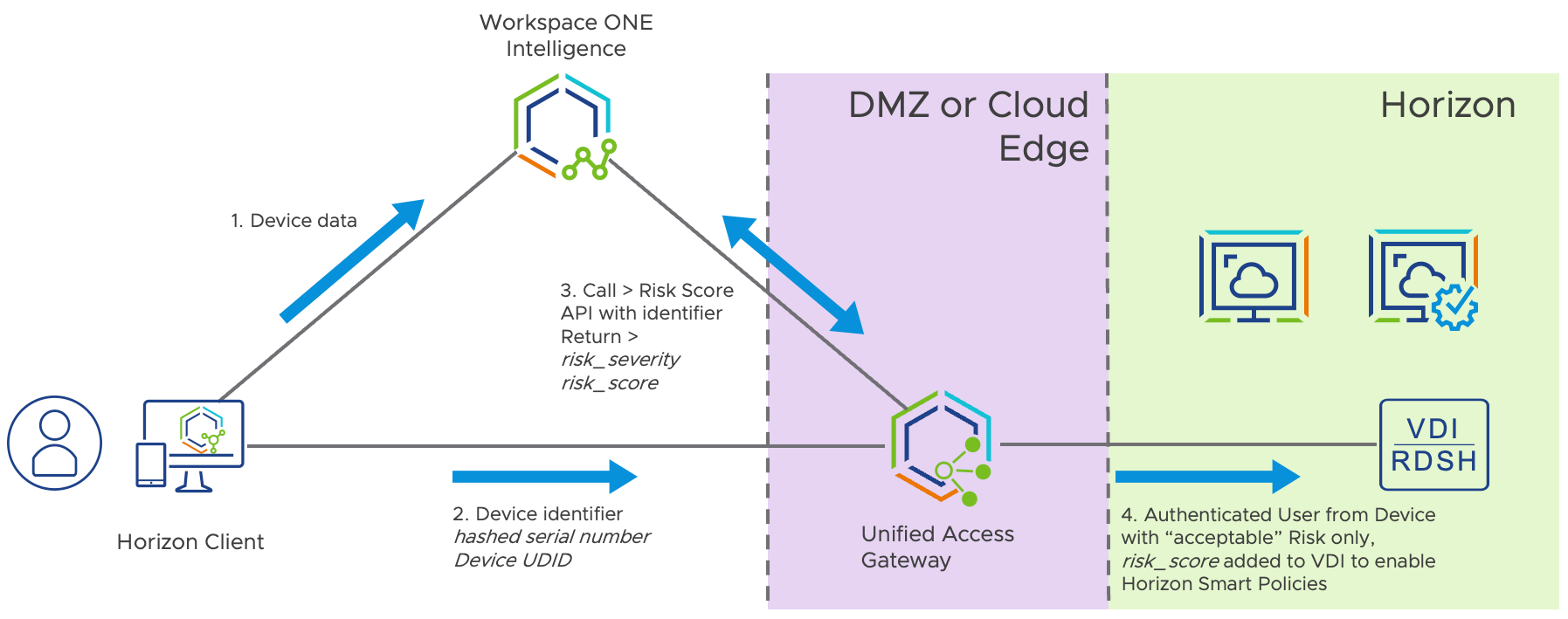
Figure 20: Workspace ONE Intelligence – UAG integration
These documents provide a guidance on how to set up that integration and configure the Endpoint Compliance provider.
- Configure Workspace ONE Intelligence Connection Settings
- Configure Workspace ONE Intelligence (Risk Analytics) as the Endpoint Compliance Check Provider for Horizon
Workspace ONE Intelligence and Trust Network
To enable threat analytics, configure Workspace ONE Intelligence to obtain all threat data reported by each Trust Network solution configured in the environment. With this information, administrators can get insights through dashboards and can create automations based on threat events.
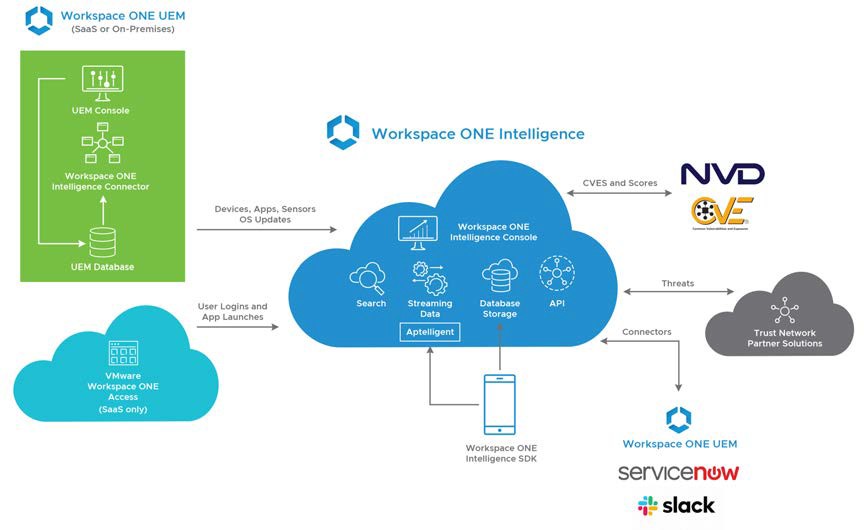
Figure 21: Workspace ONE Intelligence Architecture
The following Workspace ONE Intelligence documentation provides details on registering Trust Network and partner products with Workspace ONE Intelligence:
Workspace ONE UEM and Workspace ONE Access
Integrating Workspace ONE UEM and Workspace ONE Access enables the enforcement of device trust during the user authentication and authorization process. Workspace ONE UEM provides mobile management services for devices. Workspace ONE Access provides services for single sign- on and identity management for users.
When the components are integrated, Workspace ONE Access can obtain device compliance status directly from Workspace ONE UEM. Integration also enables users to authenticate on their enrolled devices and then SSO to the unified application catalog for a seamless user experience and secure access to their apps.
The reference architecture guide provides detail on Workspace ONE UEM and Workspace ONE Access Integration. The following documents provide instructions for setting up certificate-based authentication in Workspace ONE Access. Be sure to enable a certificate-revocation check to keep certificate authentication up-to-date and secure.
- For certificate-based authentication, see Configuring Certificate Authentication for Use with Workspace ONE Access.
- For mobile SSO for iOS, see Configure Mobile SSO for iOS Authentication in Workspace ONE Access.
- For mobile SSO for Android, see Configure Mobile SSO for Android Authentication in the Built-in Identity Provider.
Workspace ONE SSO offers mobile SSO for iOS and Android devices. The implementation of mobile SSO is based on the features provided by underlying OS.
- Mobile SSO for iOS – Uses a key distribution center (KDC) without the use of a connector or a third-party system. Kerberos authentication provides users who have successfully signed into their domain with access to their Workspace ONE app catalog without additional credential prompts. For more information, see Implementing Mobile Single Sign-On Authentication for Workspace ONE UEM-Managed iOS Devices.
- Mobile SSO for Android – Uses certificate authentication and the Workspace ONE Tunnel mobile app. The Workspace ONE Tunnel client is configured to access the VMware Workspace ONE Access service for authentication. The tunnel client uses the client certificate to establish a mutually authenticated SSL session, and the Workspace ONE Access service retrieves the client certificate for authentication. For more information, see Implementing Mobile Single Sign-On Authentication for Managed Android Devices.
Unified Access Gateway and Workspace ONE Access
The integration between Unified Access Gateway and Workspace ONE Access adds an additional layer of validation for incoming traffic to virtual desktops and applications. With this integration, Unified Access Gateway can communicate with Workspace ONE to ensure the user is validated and authenticated.
JWT token integration involves both Workspace ONE Access and Unified Access Gateway. You must specify the JWT token attributes in order to create a secure relationship between the two products.
- For instructions on configuring JWT settings in Workspace ONE Access, see Launching Horizon Resources Through Validating Gateways.
- For instructions on configuring JWT settings in Unified Access Gateway, see Configure JSON Web Token Settings.
Unified Access Gateway and Horizon
Integrating Unified Access Gateway and Horizon ensures that all connections to desktops and applications are secure, controlled, and validated with a single platform.
- To ensure the complete isolation of different types of network traffic, be sure to deploy Unified Access Gateway using either a two-NIC or three-NIC configuration.
- A two-NIC deployment separates Internet traffic onto its own NIC, while the management and backend network data share a NIC.
The first NIC is used for Internet-facing unauthenticated access. Traffic going to the internal network through the inner firewall must be authorized by Unified Access Gateway. The backend authenticated traffic and management traffic are separated onto a different network. - A three-NIC deployment separates the Internet traffic onto its own NIC, and also separates management and backend network data onto separate dedicated networks.
For deployment instructions, see the operational tutorial Deploying Unified Access Gateway with Two NICs Through PowerShell, and see Deployment with Horizon and Horizon Cloud with On-Premises Infrastructure, in Deploying and Configuring VMware Unified Access Gateway.
Because the Zero Trust model should not distinguish between internal and external network perimeters, it is important to specify the proper security protocols and cipher suites that will be used to encrypt communication between Horizon clients and the Unified Access Gateway appliance. For instructions, see Change the Security Protocols and Cipher Suites Used for TLS or SSL Communication, in Deploying and Configuring VMware Unified Access Gateway.
For details on how the primary and secondary protocols of a Horizon session traverse Unified Access Gateway, see the guide Understand and Troubleshoot Horizon Connections.
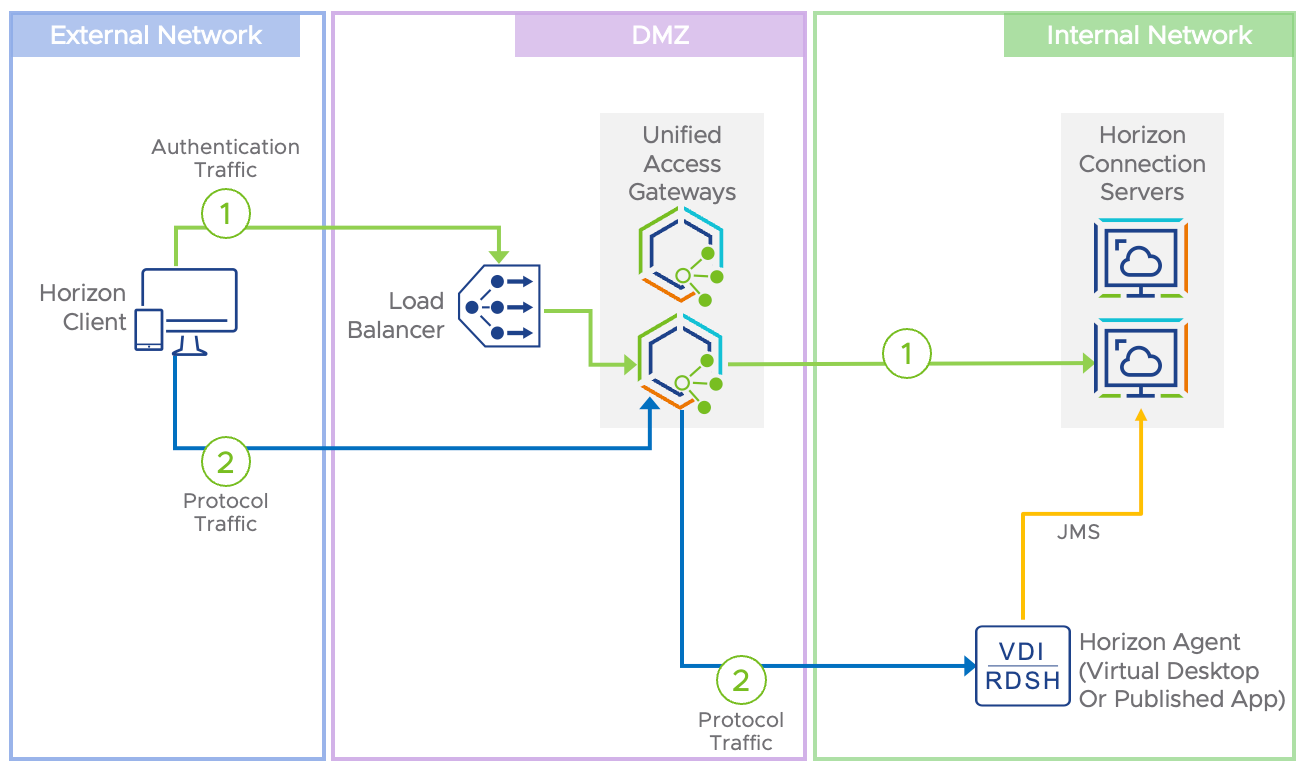
Figure 22: Horizon Primary and Secondary Protocol Traffic Flow Through Unified Access Gateway
Workspace ONE Access and Horizon
Integrating Horizon into Workspace ONE Access provides critical functionality to allow the implementation of a Zero Trust model.
- Horizon entitlements are synchronized with the Workspace ONE Access catalog.
- Authentication is performed by Workspace ONE Access and can include multi-factor and other authentication methods.
- Conditional control and access policies can be used by Workspace ONE Access when a user attempts to launch a Horizon published application or desktop.
The reference architecture guide provides details on Horizon and Workspace ONE Access Integration.
Figure 23: Workspace ONE and Horizon Integration
To enforce policies created in Workspace ONE Access, configure the Horizon Connection Servers to use Workspace ONE mode. With this mode enabled, when users open Horizon Client and attempt to log in to the server, they are redirected to log in to Workspace ONE Access. See Configure Workspace ONE Access Policies in Horizon Console, in the Horizon Administration guide.
After logging in through Workspace ONE Access, if the Horizon True SSO feature is configured, users can select a Horizon desktop or application from the catalog and SSO to that desktop or application, regardless of the authentication mechanism used. The True SSO feature was described earlier in this guide, in the section Single Sign-On. For an overview of the setup procedure, see Setting Up True SSO, in the reference architecture guide.
Summary
After you implement and integrate all the products as described in this guide, you will have created the enforcement points shown in the following figure. With these enforcement points, you can control access to your applications.
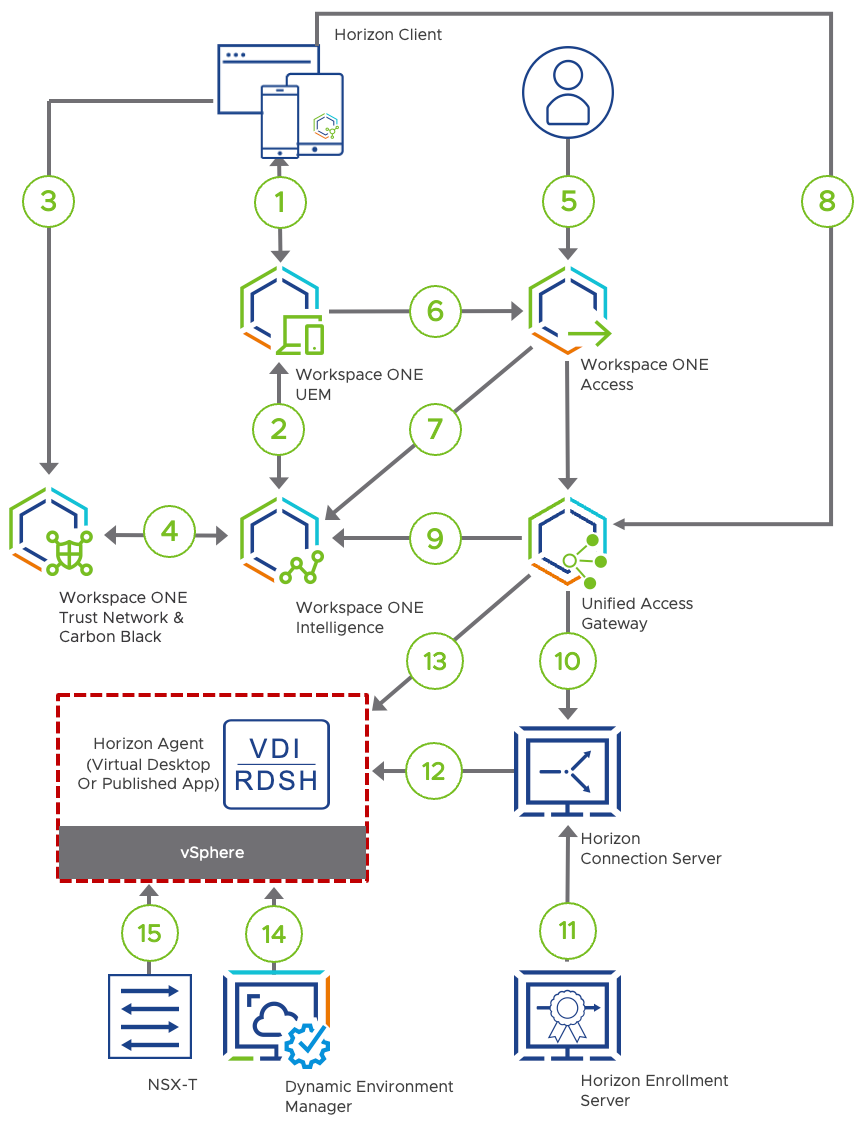
Figure 24: Device and User Trust Enforcement
As is shown in this diagram, you can insert access decisions anywhere along the flow from the device and user to the application. Each step was described in more detail in earlier sections of this document.
With this implementation, we achieve a Zero Trust security model that protects traditional applications. Although this implementation makes a very good start on the journey to digital transformation, keep in mind that Zero Trust is a process rather than a product. As VMware and its partner companies develop new functionality, be sure to revisit the solution and consider the latest enhancements.
Change Log
The following updates were made to this guide:
| Date | Description of Changes |
| 2022/11/21 |
|
| 2022/08/15 |
|
| 2019/01/11 |
|
About the Authors
- Peter Bjork is a Senior Staff EUC Architect in End-User-Computing Technical Marketing, VMware.
- Graeme Gordon is a Senior Staff EUC Architect in End-User-Computing Technical Marketing, VMware.
- Andreano Lanusse is a Staff EUC Architect in End-User-Computing Technical Marketing, VMware.
- Sascha Warno is a Staff EUC Architect in End-User-Computing Technical Marketing, VMware.
- Shardul Navare is a Senior Technical Marketing Architect in End-User-Computing Technical Marketing, VMware.
- Hilko Lantinga is a Staff EUC Architect in End-User-Computing Technical Marketing, VMware.
- Caroline Arakelian is a Senior Technical Marketing Manager in End-User-Computing Technical Marketing, VMware.
To comment on this paper, contact VMware End-User-Computing Technical Marketing at euc_tech_content_feedback@vmware.com.
