VMware DevSecOps-as-a-Service: App Delivery with Enhanced Security
Overview
The arc of digital business leads companies to a “do more, own less” model. Companies are becoming more digitized while owning and running fewer organic IT resources. Cloud computing and virtualization are a cornerstone of this transition, as is the availability of “…as a Service” functionality. Businesses still require specialized software to support specific core competencies. Due to the greatest familiarity with their own business, companies are often best served developing applications in-house. These businesses are frequently not experts in modern software delivery and are amenable to assistance.
Thus, the opportunity to provide “DevSecOps-as-a-Service” (DSOaaS) represents a clear, customer-oriented value for which VMware is renowned. Building on mature VMware products, such a service may be delivered almost immediately.
Audience
This whitepaper is intended for IT administrators and product evaluators who are familiar with VMware vSphere® and VMware vCenter Server®. Familiarity with networking and storage in a virtual environment, Active Directory, identity management, directory services, and Simple Mail Transfer Protocol (SMTP) is assumed. Knowledge of other technologies regarding End-User Computing (EUC), such as VMware Workspace ONE®, VMware Horizon®, and VMware Horizon® Cloud Service™ on Microsoft Azure, is also helpful.
Introduction
As a cloud-based company, VMware’s strategic priorities are aligned with Cross-Cloud Services (CCS) or multi-cloud support and integration. Refinement of these priorities includes having VMware Tanzu® and Cloud Management become the top choice for building and managing apps on native cloud, making VMware Cloud the top choice for multi-cloud IaaS and CaaS for all enterprise apps, and delivering world-class multi-cloud SaaS offerings first. Customers who adopt multi-cloud infrastructures and “…as-a-Service” based IT support still need business-specific applications.
This is an outside-in opportunity to meet VMware’s strategic priorities: enable customers to deliver their specialized applications faster and provide virtual decision support – DSOaaS is as much of such an offering as it is based on a mature set of VMware products and services, such as the Workspace ONE suite in support of Anywhere Workspace. Ongoing research will add to the existing catalog, improve current products, and better enable DSOaaS going forward.
VMware’s CCS Framework (see Figure 1) represents an integrated use of the technology stack to enable application development and is leveraged by a distributed workforce in a secure environment based on Zero Trust principles. Although there are products within the market that offer decision support to software development, no other entity has as comprehensive a solution that integrates the full technology stack from bare metal to a modern app development process, nor addresses DSOaaS so head on.
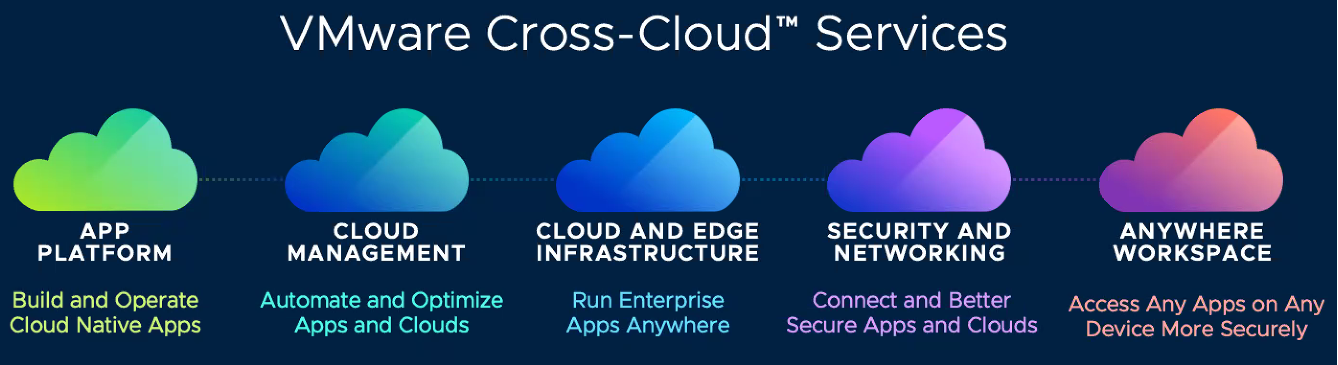
Figure 1: VMware’s CCS Framework
Digitization of Business
Companies in the 21st century have embraced the internet. Large and small businesses, multinational or local, appreciate the power of internet commerce, with many businesses lacking brick-and-mortar physical presence in favor of the virtual world. In addition, E-commerce means an unprecedented reach to markets, where small businesses, which in a previous era would have been limited to customers in their physical locality, now may have a global clientele.
Cloud computing means companies no longer need to maintain their own IT infrastructure. One major selling point for cloud infrastructure is its scalability and corresponding price structures: a company only pays for as much infrastructure as it needs at any given time. There are numerous SaaS offerings for routine business functions: email, presentations, accounting, payroll, sales support, and many others. Companies are happy to outsource functions that are not core competencies to real experts. Such outsourcing allows them to focus their resources on their core business rather than spend time and effort trying to develop ancillary expertise.
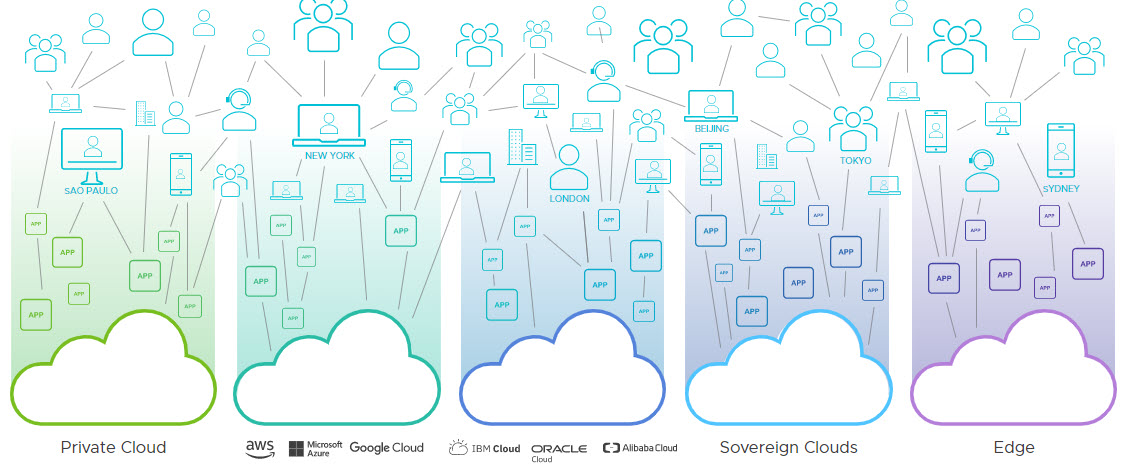
Figure 2: Modern Multi-Cloud & Cloud Computing
Challenges arise in two areas: data and specialized applications. Knowledge management, the discipline of collecting data, storing it efficiently, and sharing it amongst those who need it to do their jobs, has been a concern for as long as organizations have existed. However, specialized applications are a uniquely digital issue. The options are limited when companies need software, whether user interfaces, processing algorithms, or backend databases, which is particular to their business. They may outsource development, wherein they must engage software engineering partners over the specialized apps’ complete Software Development Lifecycle (SDLC). Or they may develop their software.
There are several advantages to a company developing its custom apps. The biggest are those associated with a company’s familiarity with their business and inside knowledge of practices. There is no need to explain the nuances of the business to an outside developer. There is also no need to share inside or proprietary information with outsiders connected with the SDLC. Coding is a teachable skill, especially with the increasing availability of low-code options. More important is articulating processes and algorithms that specialized apps need to execute. Insiders usually know such things, even if they don’t think of them in algorithmic terms.
The burden imposed by in-house development is the management of the SDLC. Application development is seldom just coding. Given the IT ecosystem’s fluid and constantly changing nature custom applications usually involve maintenance to keep functionality and compatibility current. As companies evolve, apps often need to change to reflect new business practices, products, and services. This needs to happen without compromising a company’s core competencies; stakeholders tend to look unfavorably on business interruptions due to IT failures.
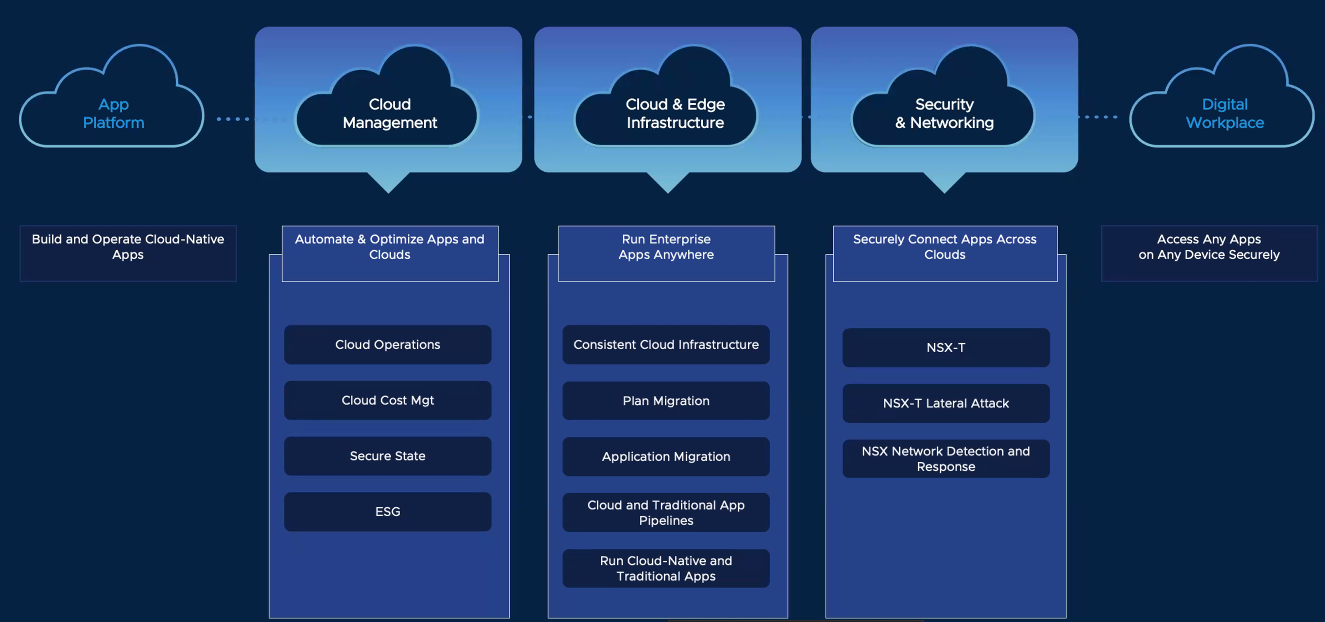
Figure 3: CCS Framework Details
What is DevSecOps, anyway?
“DevSecOps” is a portmanteau of the words “Development, Security, and Operations” and refers to a set of interlocking functions needed to support an SDLC exclusive of actual coding. Much of the functionality pertains to management: provisioning resources for development, planning, prioritization of requirements for a given software project, and tracking the readiness of code being written for deployment. Testing and security have become a priority as of the 2014-2015 time period. Does code have vulnerabilities? Does it meet standards for reliability? Code must be moved from development to production while minimizing the impact on ongoing operations. Finally, operating software must be monitored for interruptions or other issues. Ideally, feedback mechanisms also evaluate how well existing applications are meeting demands and where improvements are most needed.
While some human interaction is needed in managing an SDLC, much of it may benefit from the power of automation. For example, one significant advantage of cloud computing is being able to automatically provide resources that are preconfigured and hardened with appropriate levels of security without concern about the requester’s security awareness and ability. Similarly, many management functions also lend themselves to automation, such as accumulating and prioritizing requirements, sequencing and chaining features that are best built progressively, and determining dependencies for more efficient coding. Tracking the progress of code also lends itself to automation. Although there are toolsets and programs used by project managers to help track development, much of the work PMs do is manual and repetitive. It may be better done algorithmically with limited human intervention.
Security and testing have gained importance as cybersecurity has drawn greater attention. Many companies are quick to throw the cliché of “shifting security left,” appreciating that designing security into software is much faster and cheaper than remediation later in an SDLC. The concept of “shifting security left” is a central tenet in NIST SP 800-218 - Secure Software Development Framework (SSDF) version 1.1, published in February 2022. The SSDF sets guidelines for preparing organizations for secure development, producing secure software, protecting software, and responding to vulnerabilities (see Figure 4).
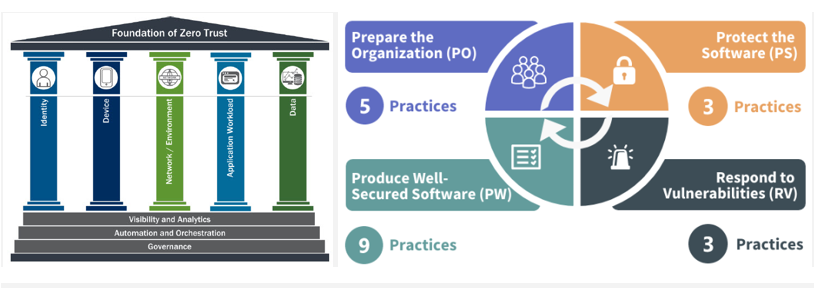
Figure 4: CISA ZT Pillars & NIST’s SSDF Model
For many of the recommended tasks listed in the SSDF, as with provisioning development environments, automation is helpful. Providing developers with templates and patterns for secure algorithms speeds the coding process and mitigates many vulnerabilities by avoiding them. Automated testing processes, both while code is being written and shortly after completion, may look for other vulnerabilities, such as logical flaws to be exploited. Although human testers offer irreplaceable value, automated testing may augment their efforts and test repetitively for many common vulnerabilities.
Transitioning code from development to production is a management problem requiring precise timelines and meticulous attention to detail. Although human decisions cannot be completely divorced from this stage, greater speed and reliability come from adding automated processes. In addition, many monitoring features may be added to a development environment, using dashboards and alerts to detect and report anomalies, while tracking ongoing and emerging trends. Finally, bots and other diagnostics may help assess user satisfaction with applications, which drives the cycle to improve existing or create new software.
Agile Methodologies
Agile is a development methodology, the intellectual underpinning of which is based on the work of the late John Boyd, meant to develop functional software in the face of incomplete or changing requirements. It favors rapid iteration and review in short development cycles (known as sprints) to produce and improve upon minimum viable products which meet end users’ needs. It eschews elaborate specifications and planning based on the assumption that end users often cannot define ultimate requirements when development begins or circumstances, such as available technology or markets, can be expected to change before delivery is complete. Agile methodologies lend themselves well to products that require the addition of new features, regular upgrades, or must operate in fluid environments.
Enter the Agile Manifesto
No discussion of modern application development is complete without alluding to the Agile Manifesto. First published in February 2001, the Manifesto lists four key values and twelve principles the authors believed should guide software development. This document is historically interesting because it marks the beginning of “Agile Methodologies” as approaches to software development. Moreover, the Manifesto is compelling because it provides a snapshot of the mindset of many developers: developers want to code.
The values and principles listed in the Manifesto are pragmatic: the key metric for success is working software. The emphasis is on getting functionality soonest with constant refinement until customers are satisfied. The Manifesto eschews elaborate planning and up-front specifications, taking the view that such details are likely to change, often because—at least where software is concerned—customers are frequently unclear about requirements at the start of a development effort. Constant interactions between developers, people who understand critical aspects of business, and users are stressed. In aggregate, the principles in the Manifesto offer a compelling argument for in-house app development, ideally making effective use of cross-functional teams.
The worst aspect of the Manifesto has been its abuse by lazy developers. Hiding behind misinterpretation or oversimplification, some use the Manifesto for justification to omit adequate documentation and completely dismiss any planning process. In their commentary, the authors warn how the principles are about priorities, rather than binary choices. Yet even such misinformed behavior has value in underscoring the developer mindset: developers want to code.
A salient point from the Agile Manifesto is to minimize the overhead burdens imposed upon developers by managing an SDLC. Although developers may be capable of managing updates, change control, system monitoring, and tracking workflows, all of these distract from their main task of developing software. There is a clear need for infrastructure which automates the development environment to the greatest extent possible. As with IT, most companies’ core competencies do not include SDLC management (as are included within the VMware Cloud-hosting solution framework – see Figure 5). Providing an environment where in-house developers can focus on coding while reducing overhead burden offers real value.
VMware’s Security Development Lifecycle (SDL) program is designed to identify and mitigate security risks during the development phase of VMware software products. The development of VMware’s SDL has been heavily influenced by industry best practices and organizations such as the Software Assurance Forum for Excellence in Code (SAFECode) and Building Security in Maturity Model (BSIMM).
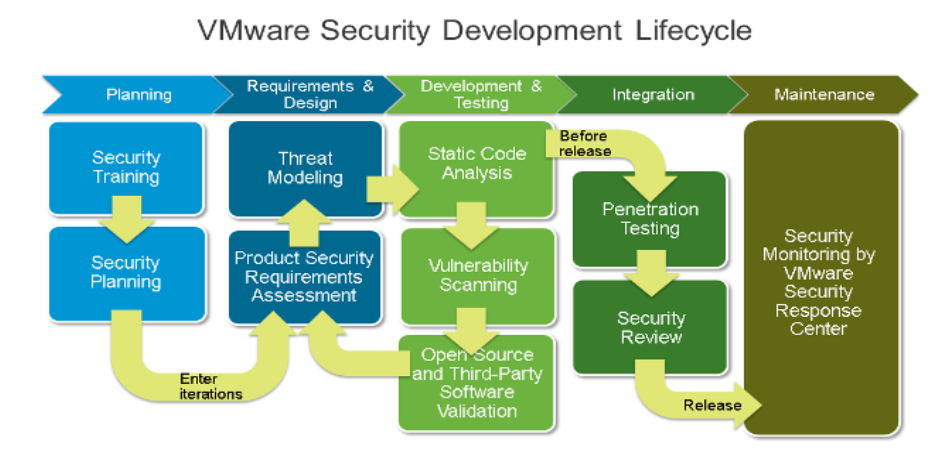 Figure 5: VMware Security Development Cycle
Figure 5: VMware Security Development Cycle
Enabling Modern Software Development – The Layer Cake
The VMware portfolio allows companies to shift as much of their IT infrastructure to cloud-based architecture as they please. The full stack of VMware offerings—the Layer Cake—allows software-defined, cloud-based data centers using physical infrastructure or hyperscaler agnostic outsourcing. VCF comprises the base of the Layer Cake and a Software-Defined Data Center (SDDC) bringing the full and complimentary functionality of vSphere, VMware vSAN™, and VMware NSX® into an integrated whole. Associated with this layer is endpoint protection and security provided by VMware Carbon Black®.
In aggregate, this layer of functionality offers a comprehensive and scalable IT infrastructure. It offers freedom of agnostic accessibility, complete flexibility on the choice of hyperscaler, and is ideally suited for companies for which IT is not a core competency. This layer simplifies and accelerates the use of underlying infrastructure. It enables the concept of heterogenous computing transparently for developers.
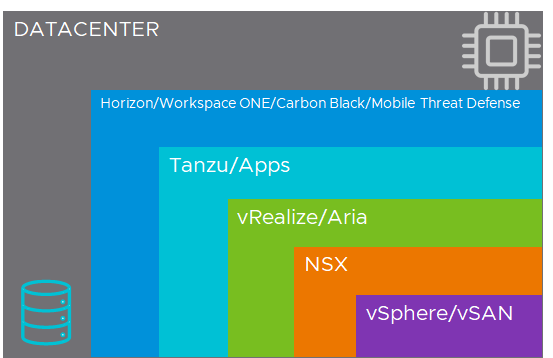 Figure 6: The Layer Cake
Figure 6: The Layer Cake
Atop this sits a layer of functionality dedicated to applications and virtual interfacing. The Tanzu suite of products offers an environment to develop modern containerized applications and execute them within a multi-cloud capable Kubernetes control plane. Associated with this layer is the Horizon product line, which enables virtual desktop interfaces (VDI) across an organization. VDI consolidates individual workstations in a data center, allowing users to have the same personal desktop experience regardless of the device used for access. It also allows central management of workstations, which enables rapid updates and comprehensive security policies.
Workspace ONE brings SaaS offerings to developers, allowing the use of off-the-shelf apps in the development process. This layer allows developers to build containerized applications while their work is decoupled from specific physical devices. Essentially, it abstracts away variation which may be introduced by different endpoints and enables a distributed workforce. It has the benefit of making SaaS applications and features available to any and as much of a workforce as needed. The result is standardization and better security while retaining the prospect for individual customization within defined parameters.
Workspace ONE has also received its Authority-to-Operate and Authorization from the General Services Administration (GSA) Federal Risk & Management Program (FedRAMP) program which provides for enhanced security and monitoring for use within the Federal Civilian, Intelligence, and Department of Defense and those components are represented below. VMware has also been authorized in other solutions with FedRAMP, including VMware Government Service’s (VGS) Infrastructure-as-a-Service (IaaS), which is a set of cloud service offerings designed to allow US government agencies and customers supporting the US government to migrate, manage, and operate more sensitive workloads in the cloud. The VGS authorization boundary provides SaaS and IaaS capabilities to deliver modern applications at the speed the US government demands and operate across the data center, the edge, and the cloud. VGS provides the following FedRAMP authorized services at the High baseline: VMware Cloud on AWS GovCloud (US) (VMC), Hybrid Cloud Extension (HCX), Carbon Black Cloud (CBC), and Software Defined WAN (SD-WAN) and Horizon Cloud Service (HCS). More information on the VGS public sector roadmap can be found on the VMware Trust Center.
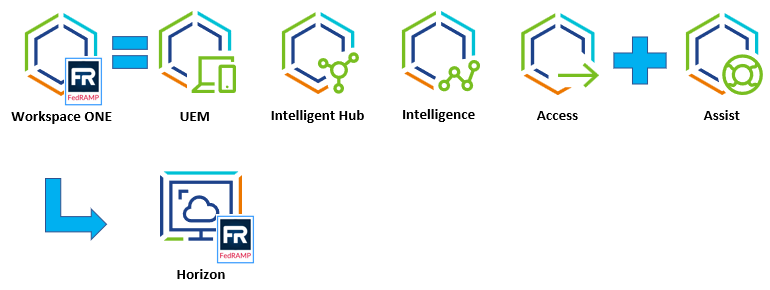
Figure 7: VMware FedRAMP Workspace ONE Solutions
The Layer Cake has drawn the attention of the US Government (USG), as several of its entities have become enamored with the concept of software factories. Embracing software factories affirms the value of business insiders developing applications. Although the USG has traditionally outsourced software development to various vendors, the software factory is a deliberate attempt to insource. The U.S. Air Force, with both Kessel Run and Kobayashi Maru, and the U.S. Army have created software factories, the latter at U.S. Army Futures Command out of Austin, TX that has been receiving great press attention.
While particulars of execution vary, the underlying concept is the same: provide an environment for agile software development by uniformed personnel. So, the U.S. Army software factory has been running an education program to teach soldiers the basics of coding and software design, with a follow-on assignment as programmers. The U.S. Air Force factories are less oriented on basic education than on using and improving existing talent. Other organizations within the USG, including DHS and U.S. Cyber Command, are also looking into similar software factories. Although the software factory movement is in its early stages and taking a variety of instantiations, the intent is clear: numerous bodies within the USG recognize the value of insourcing the development of critical applications by people who implicitly understand the missions being supported by their software.
The Layer Cake is seen as a ready solution to provide a modern development environment that has the added benefit of interoperability. Although different government entities may take different approaches to software engineering, all will use a common standard that enables sharing and collaboration between organizations. As several state governments have also expressed interest in creating software factories, the prospect of governmental collaboration grows.
Offering DevSecOps-as-a-Service
By adopting the Layer Cake, businesses may outsource significant portions of their IT infrastructure. Starting with VCF, and the functionality provided by its vSphere, vSAN, and NSX components, augmented with Carbon Black, the result is a secured multi-cloud platform upon which to handle business-related IT. In the next layer, with Tanzu and Horizon, the stage is set for in-house developers to write code. Tanzu offers the means to build and run modern containerized applications. Horizon offers a VDI solution to access a common development environment and use SaaS-based tools and apps.
Having all of this in place obviates the need for a company to administer most of its IT, reducing most of the workload to company-specific apps and data. Aside from the software development environment, the Layer Cake offers numerous other IT benefits with low marginal cost in the additional workforce, not least many of the components of a Zero Trust Architecture (Figure 8) as described by US GSA.
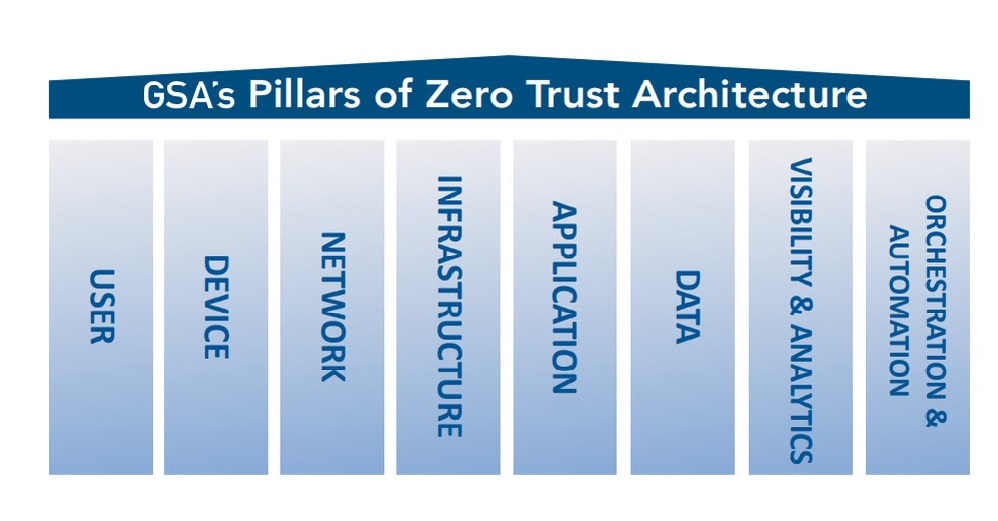
Figure 8: US GSA’s ZT Pillars Model
Bridging the gap between having outsourced IT infrastructure and enabling developers to write code without undue distraction requires some additional automated or partially automated functionality. Development environments need to be provisioned as necessary. Design aids help developers think about program structure, flow, and data use have value. Project tracking and mapping of dependencies allow developers to stay on the timeline and understand which resources are being affected by their choices.
As a bonus, security may be enhanced by using automatically configured resources as they are provisioned, supporting the user, device, and infrastructure pillars. Such automatic configuration and provisioning are an integral part of Horizon, Workspace ONE, and other End-User Computing products. The environment may add guardrails to prevent unsafe practices and approved patterns and libraries for coders to reuse, which falls squarely in the requirements of the application pillar.
Testing capabilities are necessary to ensure code resilience, including static and dynamic scanning, fuzz testing, and others. Packaging and releasing will build and deploy approved applications to users and add them to the functional ecosystem of business software, enabling better compliance with visibility and analytics requirements while employing tenets from orchestration and automation.
Finally, version control is needed to maintain awareness of the state of deployed applications and methodically upgrade or repair existing offerings. These efforts all address and fall under the guidelines presented under the Software Development Lifecycle and NIST SSDF, as well as providing a method to comply with Executive Order 14028, “Improving the Nation’s Cybersecurity”, and including new federally mandated ‘secure development and certification requirements’ that will become mandatory in 2023.
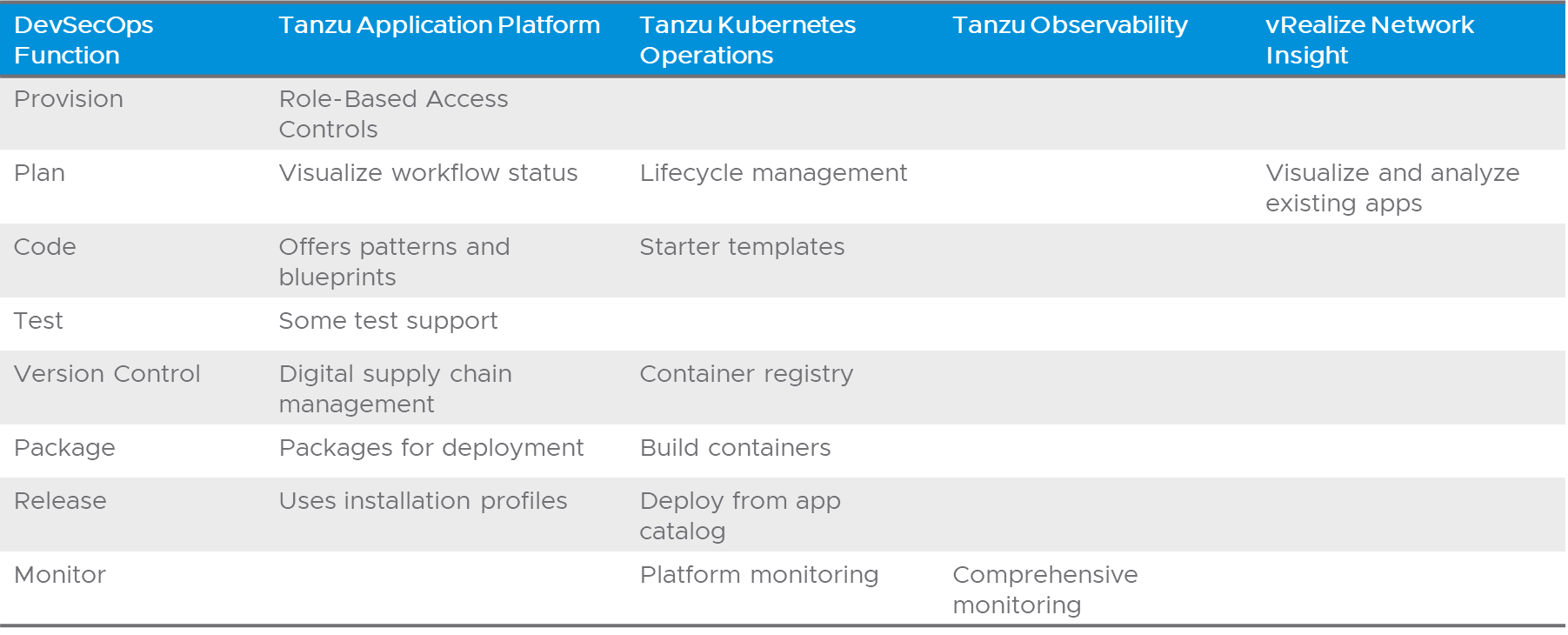 Figure 9: DevSecOps Functional Overlap
Figure 9: DevSecOps Functional Overlap
Tanzu Application Platform (TAP) offers many of these features in an off-the-shelf product. TAP offers coding templates to provide skeleton code that incorporates security features a company needs. Graphic user interfaces simplify the creation and integration of code into new or existing applications. Deployment is faster due to the use of installation profiles. Role-Based Access Control helps to maintain the separation of duties and the separation of data sets. TAP even tracks workflows and offers visualization aids on work status and scheduling, in addition to helping with digital supply chain management. Aside from supporting hyperscaler offerings, specifically EKS and Azure Spring, it accommodates and integrates a wide range of third-party tools and data services.
Tanzu Kubernetes Operations (TKO) offers functionality for containerized applications’ management, operation, and maintenance. It has a registry to keep container images for pushing, pulling, storing, and scanning. Full-stack multi-cloud observability enables the setting of proactive alerts, access to historical data, and ease of troubleshooting of deployed apps. Providing a centralized Kubernetes control plane across locations, clouds, and variations of Kubernetes simplifies keeping applications in operation. It complements much of the functionality in TAP, and many aspects of DevSecOps are handily accomplished between the two products.
A significant portion of the administrative overhead of managing an SDLC is automated. VMware Tanzu Observability allows comprehensive monitoring and visualization of Kubernetes-based applications as they run by assimilating and presenting data from applications, containers, microservices, cloud infrastructure, and business data. One final product, Tanzu Activation Services, is a hands-on advisory engagement to bring a company’s IT team up to speed on using Kubernetes in general and the Tanzu suite in particular.
Additional functionality will make the TAP-TKO combination a more comprehensive “DevSecOps as a Service” solution. A requirement parsing system may be useful to visualize and prioritize demands for app development. Some of this discovery and visualization of existing apps is already offered for existing environments by vRealize Network Insight and App Transformer for Tanzu, although new requirements are not assimilated. A more comprehensive set of security testing tools will help developers write more resilient code, some of which have been incorporated into TAP 1.3. Finally, a feedback mechanism for in-house and external consumers of specialized apps speeds up the identification of improvements to the app portfolio and recommendations for additional capabilities.
The Tanzu suite of products is further enabled by a variety of End-User Computing products which enable the combination of seamless secure access with role-based controls, all supported by automation. Horizon offers a platform for running virtual desktops, creating a consistent user experience. VMware Dynamic Environment Manager™ provisions user settings based on predefined IT policies and enables access to resources within a physical or cloud-hosted environment.
Workspace ONE provides unified endpoint management, which enables integration of devices into the development ecosystem while providing consistent management of content, applications, and policies. VMware Workspace ONE® Intelligent Hub provides a tailored user experience with an app catalog for all software development and internal business tools. Workspace ONE Experience Workflows enables internal business processes and may be used to enable routine DevSecOps processes.
Summary and Additional Resources
The Way Forward
The existing portfolio of VMware products supports a DSOaaS offering. Bundling the Layer Cake, along with TAP, TKO, and Tanzu Activation Services, along with a collection of End-User Computing offerings, amongst others, enables entities to outsource almost all IT support while having a solid framework to develop company-specific apps.
Ongoing research, such as Project Trinidad, which monitors traffic within Kubernetes APIs to enhance operating efficiency and security, will add to the richness of capabilities in the DSOaaS suite. Developing additional functionality will round out the portfolio and position VMware for a unique and powerful offering in the “as a Service” universe. A unified “DevSecOps as a Service” product further distinguishes VMware from competing infrastructure providers and enablers.
By taking virtualization to its logical conclusions, customers may focus on those competencies which define their business while benefiting from the power of digitization and global reach. In addition, by reducing in-house overhead and enabling a rapid and secure software development process, VMware enables innovation and delivery of digital capabilities at speed.
Additional Resources
For more information on configuring or enabling Horizon or Workspace ONE including, VMware Workspace ONE® Intelligence™ and UEM, as well as VMware Workspace ONE® Access, and Hub Services, explore the following resources:
VMware Horizon Resources
- VMware Tech Zone: WSO-Horizon-Architecture-Guide
- VMware Tech Zone: Intro-to-Zero-Trust-Arch-with-Horizon
Workspace ONE Resources
VMware vRealize & Tanzu Resources
VMware Networking & Advanced Security
Federal Integration References
- VMware TechZone: WS1 FedRAMP UEM Intro
- VMware Tech Zone: WS1 FedRAMP Intelligence Service Intro
- VMware Tech Zone: WS1 FedRAMP Access & Intel Hub Services Intro
VMware Cloud Infrastructure Tech Portals
- VMware TechZone: vSphere, HCI & Cloud Foundation
- VMware TechZone: VMware Cloud
- VMware TechZone: VMware Cross-Cloud Services & Multi-Cloud
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2022/12/08 |
|
About the Authors
Seth Milstein—guest contributor to VMware Tech Zone and co-author—is serving in a role at VMware as a Senior Solution Architect supporting Public Sector in improving their information environment, including cloud infrastructure, rapid software development, and data organization. Prior to VMware, he was a serial entrepreneur and an inventor with patents in mobile phone technology. He founded and ran an ethical hacking academy for JPMorgan Chase & Co. and is a Colonel in the US Marine Corps Reserve.
Andrew Osborn is serving in a role at VMware as a dedicated ‘Staff Technical Marketing Architect’ for all things End-User Computing (EUC) compliance / regulatory. He has over 20 years’ experience in the IT Industry, including the last 9 years within Public Sector, with roles spanning Cybersecurity, Networking, Enterprise Ops, Mobility & Telco solutions, encompassing numerous technologies and architectures. Prior to VMware, Andrew spent 15 years within AT&T in different roles and received an MIS degree from the University of Oklahoma with certs from ISC2 CISSP & GIAC GSLC and is based out of San Antonio, TX.
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware End-User-Computing Technical Marketing at euc_tech_content_feedback@vmware.com.
