Introduction to VMware Zero Trust
What is Zero Trust?
Security is an ongoing challenge for organizations, and with today’s dynamic workforce, the challenge is ever-increasing. John Kindervag, the analyst who first coined the term Zero Trust while at Forrester in 2010, referred to a security model that does not automatically trust entities within the security perimeter. Since then, rapidly changing work styles and increased use of SaaS applications have resulted in Zero Trust becoming one of the most important forms of alternative security, an architectural mindset aimed at securing and protecting your data.
VMware is dedicated to the Zero Trust model, which means building a dynamic, modern security architecture that builds trust on a much broader and deeper basis than traditional security measures.
Purpose
This guide introduces you to the VMware Zero Trust model, including detailed summaries of the five pillars of Zero Trust: device trust, user trust, transport/session trust, application trust, and data trust.
Audience
This guide is for IT decision-makers, architects, and information security administrators who want to implement a Zero Trust security solution. Both current and new administrators can benefit from using this guide. Familiarity with networking in a virtual environment, device-management, identity solutions and standards, and firewall policies is assumed, as well as knowledge of VMware components, virtual machines, and virtual desktop infrastructure (VDI) concepts.
Overview of Zero Trust Architecture
With traditional security architecture, the local network usually consists of a single large perimeter, which can be a single point of failure. If an attacker succeeds in penetrating this perimeter, the attack can move horizontally throughout the entire DMZ. Since the security is focused primarily on the perimeter, the attack can be very difficult to contain.
The concept of micro perimeter changes the architecture from a single large DMZ to multiple smaller boundaries around each application and that application’s data. If an attacker succeeds in penetrating one of these boundaries, it can move only within that perimeter, and can more easily be contained. This multi-layered approach provides superior security.
The multi-layered approach includes adding security around the data and the application, making sure the transport or access is secure, and having a strong knowledge about the user and the device used to request access. Security checks at each layer enable you to extract audit logs and build analytics. And with logs and analytics, you can achieve automation and orchestration in which all applications and data are equally protected, and no users or devices are trusted by default.
The following VMware Zero Trust: Technical Overview video provides a technical overview of the VMware Zero Trust architecture, and the sections that follow provide a brief summary.
For more information, see also Introduction: What is Zero Trust?
The Five Pillars of Zero Trust
The Zero Trust architecture consists of five pillars—device trust, user trust, transport or session trust, application trust, and data trust. You must establish trust in each pillar to make decisions to grant or deny access. By establishing trust across the five pillars, you can gain visibility and can gather analytics across the board. Visibility and analytics are a critical part of the Zero Trust architecture, and they help to establish a deeper and broader footprint in each pillar.
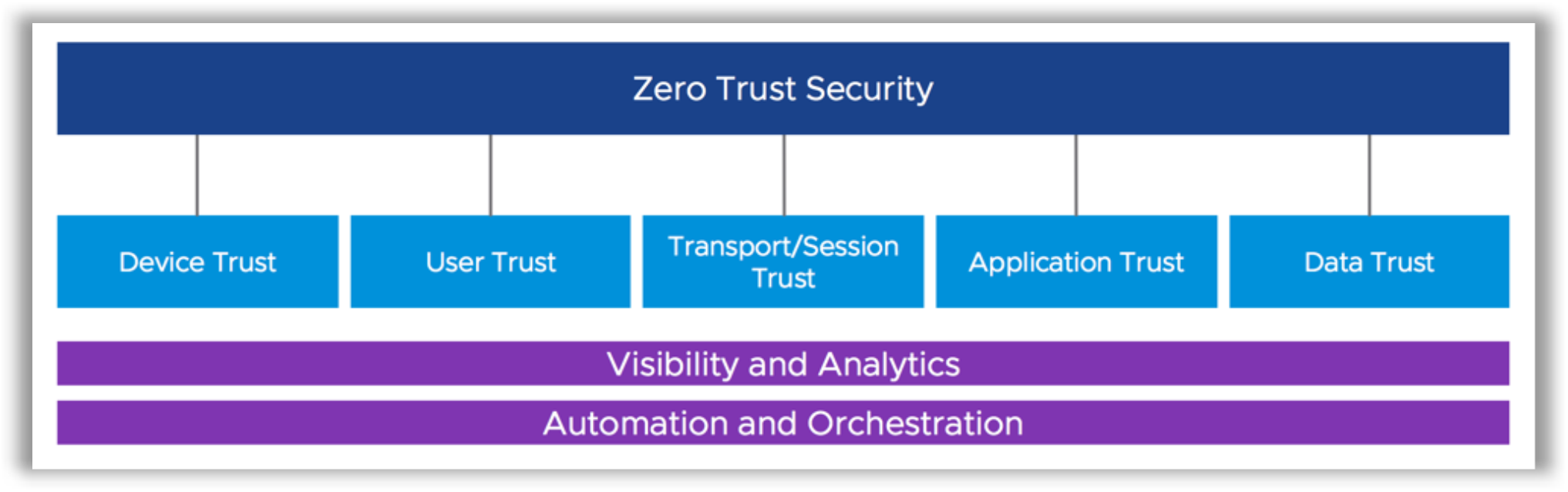
VMware is uniquely positioned to help you on your Zero Trust journey, with the broadest portfolio of solutions covering all five pillars of trust.
The following sub-sections provide examples of the parameters that might categorize each pillar and indicate which VMware solutions can help to establish trust.
Device Trust
By interrogating device trust, you can get details on the following parameters:
| Device Trust Parameters | Products to Solve Device Trust |
|
|
User Trust
| User Trust Parameters | Products to Solve User Trust |
|
|
Transport / Session Trust
By using the principle of least-privilege access to resources, you can limit access rights to users and grant the minimum permissions required to perform their work.
| Transport / Session Trust Parameters | Products to Solve Transport / Session Trust |
|
|
Application Trust
| Application Trust Parameters | Products to Solve Application Trust |
|
|
Data Trust
Finally, you must make sure that the data stays secure.
| Data Trust Parameters | Products to Solve Data Trust |
|
|
Analytics and Automation
By establishing trust across the five pillars, you can gain visibility and analytics. You need a system that gives you visibility by logging all traffic. This information can then be used to learn and monitor network patterns. The resulting analytics help you make effective dynamic policy and trust decisions.
With visibility and analytics, you can build automation and orchestration. Workspace ONE and Horizon platform services allow you to collect contextual information from across the entire environment. This contextual awareness feeds intelligence, allowing you to make just-in-time decisions, and use automation for threat remediation.
The following sections provide for details about the elements required for analytics and automation, and to help you determine which VMware solutions can help.
Visibility and Analytics
Achieving visibility and developing analytics depends on the following parameters:
| Visibility and Analytics Parameters | Products to Build Visibility and Analytics |
|
Automation and Orchestration
As part of Zero Trust, you must use more secure user authentication methods. This pillar requires a strong conditional access engine that can help make decisions using dynamic and contextual data.
| Automation and Orchestration Parameters | Products to Build Automation and Orchestration |
|
For details about VMware Horizon and Workspace ONE features that give you visibility and help you analyze behavior, and for descriptions of the automation features for Workspace ONE UEM and Workspace ONE Intelligence, see the new guide Zero Trust Secure Access to Traditional Applications with VMware.
Summary and Additional Resources
Additional Resources
To learn more about the Zero Trust model, follow the Zero Trust Activity Path, which contains a curated list of assets to help you master the VMware Zero Trust architecture. This activity path and more resources are available on Digital Workspace Tech Zone. You can also explore the following resources:
- Activity Path: Understanding Zero Trust
- Video: VMware Zero Trust: Technical Overview
- Product page: Zero Trust Security for the Digital Workspace
- Blog post: Brian Madden: What is zero trust, and how real is it today?
- Guide: Zero Trust Secure Access to Traditional Applications with VMware
- Guide: Zero Trust Secure Access to On-Premises Web Applications with VMware
Changelog
The following updates were made to this guide:
|
Date |
Description of Changes |
|
2022/10/18 |
|
|
2020/04/14 |
|
About the Author and Contributors
This Operational Tutorial was written by Peter Bjork, Principal Architect, End-User-Computing Technical Marketing, VMware.
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware End-User-Computing Technical Marketing at euc_tech_content_feedback@vmware.com.
