How VMware can Secure Mobile Endpoints with Threat Defense (MTD)
Overview
In this whitepaper, we will help clear the airwaves between mobile endpoint protection being regarded as a ‘nice to have feature’ vs. ‘an absolute necessity’. This will be showcased in a uniform theme, that in order to compliment the necessary tools a company <or> agencies possess within its Cybersecurity matrices, they must be capable of deploying security controls with visibility, alarming & notification for actionable protection of not only standard endpoints but also the mobile-enabled, to properly address a true Endpoint Detection & Response/Incident Response (EDR/IR) delivery.
Importantly, we will review how Workspace ONE Mobile Threat Defense (MTD) powered by Lookout, as a newly combined component of the VMware Workspace ONE End-User Computing (EUC) solution suite is the best tool and weapon to answer the call, unlike any in the industry.
Our goal will be to explain how MTD provides enhanced security for mobile-enabled endpoints and to address the rising threats associated with security and privacy drivers, such as malware and to meet compliance, regulatory requirements, as well as industry standards and how VMware’s Workspace ONE MTD launch best fits that model.
Lastly, this overview will provide a segue into real-world examples in the multitude of actors, gaps, and threats in the securing of mobile devices landscape to help drive home the necessity of Mobile Threat Defense as an integral part of the EUC and Zero Trust Security (ZTS) solution mix for all verticals.
Note: As a follow-up to this whitepaper, stay tuned for our release of the ‘Industry & Regional Drivers for MTD Whitepaper’ coming soon.
Audience
This document is intended for IT (Information Technology) administrators and product evaluators who are familiar with VMware's EUC powered by Anywhere Workspace and VMware Workspace ONE. Familiarity with the End-User Computing environment and modern management that includes device, app and identity management, and security measures is assumed. Knowledge of other technologies, such as VMware Horizon, Security, Secure Access Service Edge (SASE), and Zero Trust Architecture (ZTA) is also helpful.
Note: This document is only intended to provide a brief industry overview and associated product capabilities guideline, which could be used when mapping to Cyber Security Framework (CSF) requirement areas and practices/controls from numerous framework sources globally for mobile security. It is not intended to be specific or fully navigate readers through the complete set of compliance or accreditation processes, for example, that working with a third-party auditor or assessor for those respective certifications from Third-Party Assessment Organization(s) (3PAO)’s would require for full certification, and so on.
It is also not intended to provide mapping of other VMware solutions beyond the EUC arena. For a full and complete solution matrix of VMware solutions, see the links above on SASE and ZTA to address and cover further VMware product analysis for the data center/network/boundary elements.
Executive Summary
In the past five years, the mobile operating platform and the devices which run off them have become the most common operating system (OS) for any environment, private or public sector in the world. They have even bypassed MS Windows and power more than 4 billion total devices globally and are growing. Malicious actors have taken notice and are increasingly targeting vulnerable mobile-based systems, in an attempt to infiltrate both individual and corporate resources, data, as well as private and government networks.
Threat actors know that current malware countermeasures are mostly focused on addressing Windows <or> network perimeter-based threats, leaving many public and private mobile deployments vulnerable to mobile or wireless-based attacks. These public and private devices can be high-value targets for cybercriminals, providing access to critical applications and services and substantial direct or indirect fiduciary and privacy-related resources.
In fact, mobile devices and wireless networks contain key components connected to such core business services, as email, user interfaces for customer records and interaction with databases and a large mix of the apps installed on those devices used as the interface with the backend systems that contain financial, medical, business and government data.
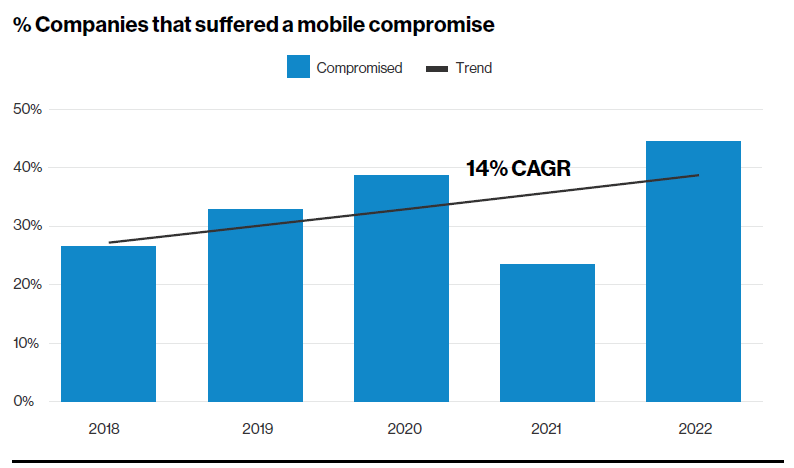
Figure 1: Credit: Verizon Mobile Security Index Report – 2022
In 2021, the FBI’s Internet Crime Complaint Center (IC3) team received a record 847,376 complaints—a 7% increase from 2020. The estimated potential losses were over $6.9 billion. As would be expected, ransomware, Business Email Compromise (BEC) and the criminal use of cryptocurrency were among the most commonly reported types of incident documented specifically to mobile. And there have been valuable targets for intelligence-gathering breaches in the past two years. Some of these have been in possession of high-profile persons on the planet, as in the case of SMS Bezos Amazon fame. The CEO was the target of a phishing attack through a messaging and social media app on his iPhone, then had extremely sensitive data and information exfiltrated, used as blackmail, and exposed to the public. The operation was largely seen as a model use case for a cyber-terror attack on a journalist that resulted in his death. And aside from the slight downturn in 2021 during the pandemic, these attacks are only increasing as represented by the Compound Annual Growth Rate (CAGR) data collection for mobile shown in the Verizon graph in Figure 1 above.
Other large-scale campaign activities carried out prior to 2022 on mobile-enabled platforms are:
- Listening to actual phone calls in real-time
- Secretly reading Short Message Service (SMS) or Apple iMessage texts, call logs
- Listening through the phones microphone the surroundings (e.g., use as remote bugging device)
- Viewing phone GPS (Global Positioning System) and location data
- Reading and forwarding of emails and calendar events or contacts to another inbox
- Remotely controlling all phone functions via SMS
- Accepting or rejecting communication based on predetermined lists
- Intercepting data communication via unsecured or improperly secured or compromised Wi-Fi APs or cellular base station (i.e., Machine-in-the-Middle (MitM))
These threats take advantage of weak authentication, vulnerabilities, and misconfigurations in container-based infrastructures to infiltrate the environment. After the attackers have obtained a foothold in their target device, network, or cloud environment, they often look to perform two types of attacks: execute ransomware or deploy crypto mining components.
Organizations need to bolster their ability to identify and defend against these types of attacks for not only the traditional environments within the enterprise’s physical facilities, but more importantly in today’s work-from-home or remote world, the mobile-enabled platforms. Thus, given the distributed, dynamic, and heterogeneous nature of today’s enterprise workloads and networks, organizations need to extend telemetry across the entire infrastructure—from endpoints to multi-cloud environments. This will allow organizations to better monitor traffic and identify abnormal behavior, including specifically for mobile endpoints and provide enhanced mitigation to the potential impacts of attacks on the enterprise from them, while increasing overall efficiencies and reducing operational costs.
In this WP, we have based many of our conclusions on our own previously released report, Global Security Insights for Intelligence from the Global Cybersecurity Landscape, which was based on our own experience with a diverse customer base, as well as through the assistance of our Workspace ONE Mobile Threat Defense partner, Lookout, will offer a comprehensive view into mobile-based malware threats to these devices and environments. Rounded out by supporting industry reports and metrics, it should provide the reader with a profound overview into the realm of the mobile security landscape today and our recommendation on how best to protect yourself and your organization from mobile threats.
As indicated, unique metrics and insights have been observed, based on the characteristics of this particular class of threats and highlighted within the report. It provides guidance on how combining endpoint detection and response (EDR) and network detection and response (NDR) solutions can help organizations stay ahead of the threats that mobile-based malware poses. References to both Mobile Threat Management (MTM) and Mobile Threat Defense (MTD) may be used ‘interchangeably’ both in the WP as within industry; both terms rely on the coverage and protection of the following areas:

Figure 2: VMware MTD Solution Coverage; Application, Web/Content, Device & Network protection
Mobile Threat Defense Overview
This section provides an overview of Workspace ONE Mobile Threat Defense.
What is Mobile Threat Defense?
Mobile Threat Defense (MTD) is the specifically designed protection for mobile-enabled devices and operating systems from attacks in key areas, such as phishing, applications, devices or Operating Systems themselves, and through connections to rogue network originated access points. MTD technology covers mobile-enabled platforms and extends coverage from the legacy Endpoint Protection (EPP) solution domain <and> is custom for mobile and MTM and provides for both the security and visibility into enterprises existing Security Information & Event Management (SIEM) for logging and actionable capabilities through (EDR/IR).
What is the goal of Mobile Threat Defense?
Mobile devices require specialized security to address the unique architecture and resource based on their architecture and operation that differs from a traditional endpoint, from the kernel to the firmware and the operating system, to the applications that run on top of them. Some of these dangers, such as phishing and web content can be ubiquitous across endpoints, but for example, traditional Win10 endpoints don’t typically receive messages through apps, such as iMessage or a specifically designed messaging app, e.g., WhatsApp. Couple this with threats, vulnerabilities, and behaviors unique to mobile-enabled devices with mobile OS’s, such as Apple’s iOS, Google’s Android OS and Chrome OS.
This enhanced protection is designed to secure the mobile workspace and enhance Zero Trust (ZT) initiatives to extend to these unique endpoints and the applications on them. Figure 3 is a visual representation of the unique factors that mobile enabled devices must be protected, including web/content, applications, network and device-based threats and vulnerabilities:
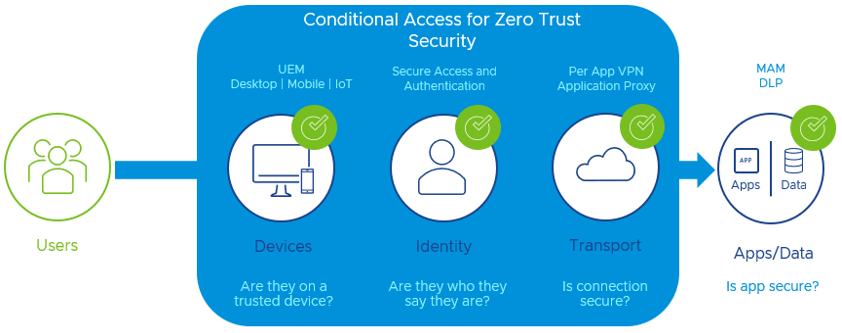
Figure 3: VMware Anywhere Workspace Overlay of our ZT solutions to enable ZT framework
What is Workspace ONE MTD?
VMware’s mobile device security Workspace ONE Mobile Threat Defense (MTD), powered by Lookout integrates with Workspace ONE in a unique way with the key services of the suite, Unified Endpoint Management (UEM), Intelligence and most importantly, embedded within the Intelligence Hub agent to form a robust endpoint protection suite onto these managed devices. This lightweight mobile app activates security via Hub and provides mobile security in an easy to deploy and manage way while offering integrated management of the device and the ability to provide actions on alerts and threats on the device without user interaction.
One of the highlights of VMware’s MTD solution over others in the industry is within the embedded threat SDK (Software Development Kit) from Lookout; customers do not have to install and activate a separate security app. The Hub option can detect device, application, and rogue network threats immediately upon activation and does not require end-user interaction. This eases organization-wide mobile security compliance by activating applications, devices, and network-based threat detection within the Workspace ONE Intelligent Hub with no separate apps or agents to deploy or activate.
And with Intelligence, the collected data from the sensors within Hub can be aggregated and reported on and most importantly, acted upon for remediation that provides a path for Endpoint Detection & Response/Incident Response (EDR/IR) for Security Operations Center (SOC) or IT teams and provide the necessary tools to automate responses to intrusion attempts on the devices, etc.
Throughout this white paper, industry referenced details regarding the drivers of mobile endpoint management and security will be highlighted as we take the Workspace ONE Mobile Threat Defense solution necessity into the fold of these MTD drivers. This past month the Gartner® Magic Quadrant™ for Unified Endpoint Management (UEM) Tools (August 2022 edition) came out and addressed within the ‘Market Definition / Description’, seven key features of an Enterprise-grade solution, VMware is the only vendor in this research with a complete package that includes:
- Integrate identity, security and remote access tools to support zero-trust access and contextual authentication, vulnerability, policy, and configuration and data management.
VMware’s solution, for the fifth year in a row, was named a Leader in the report. VMware scored highest in 4 of 5 Use Cases in the 2022 Gartner® Critical Capabilities for UEM Tools and scored in the Security-Centric Management category a 4.21/5.0 and the only product strategy fully developed to include: device management, single sign-on, remote support, remote access, endpoint security, analytics, automation and virtualization.
The following figure is a visual representation of VMware’s solution providing a unique, integrated way to protect each of the foundational zones of attack and infiltration of mobile threats through UEM & MTD, including:
Figure 4: VMware’s Workspace ONE Mobile Threat Defense enabling Endpoint Protection and EDR/IR
MTD External Drivers
This section discusses Mobile Threat Defense external drivers.
Malware Overview
Malware attacks have been making headlines lately.
The term malware is short for malicious software, and it refers to any program or process whose purpose is harmful, even criminal, or malicious. The earliest and widely known form of malware was the computer-based virus, which is the name for a program that infects other programs with its code, and replicates after the infected program is run (a worm is similar but is its own program and attempts to replicate itself on its own). Several early viruses had no malicious payload at all; they just served to show-off the coder’s skills, or to gain attention as a programmer. Because viruses were the first type of malware present within the industry, many applications that came before and today still use the name antivirus for software that protects against all kinds of malicious software.
Today’s malware has become more sophisticated, easier to deploy and in most cases, does indeed have a nefarious or malicious intent; whether that be for Denial of Service (DoS), or just the ‘lulz’ = fun, laughter, or amusement, especially that derived at another’s expense. This latter point is the prevailing derivative of the 21st century and the landscape we find ourselves in this current decade—they are in it for the money! This can represent true monetary assets but also intangible ones, such as Intellectual Property (IP) or Private Personally Identifiable Information (PII). Regardless, since there’s not a lot of money in viruses and worms any longer—unless associated with entities that take on more ‘hacktivist’ roles, such as the group ‘Anonymous’ and efforts to thwart that community’s current nemesis and assistance (e.g. Russia invasion of Ukraine), it’s all about the $ money no matter how you slice it!
Also, there's been a fundamental restructuring of cybercrime cartels thanks to a booming dark web economy of scale. Powerful cybercriminal groups now operate like multinational corporations and are relied upon by traditional crime syndicates to carry out illegal activities such as extortion and money laundering and have reached new theft of digital asset wealth, rivaling larger nation state GDP’s at approximately $1.5 trillion value as of 2021.
As a result, and flush with new currency and wealth from these previous pandemic era activities, cybercrime cartels are more organized than ever before and often enjoy greater protection and resources from the nation-states that view them as national assets, as in the case of but not limited to: Russia, China, North Korea and Iran. A recent report from VMware found that 63% of financial institutions experienced an increase in destructive attacks, a 17% increase from last year.
Destructive attacks are launched punitively to destroy, disrupt, or degrade victim systems by taking actions such as encrypting files, deleting data, destroying hard drives, terminating connections, or executing malicious code. Although these financial gains are of benefit, targeting the west and those countries did not deem an ally to these nation-state attackers are fair game, and enjoy cult popular status within their own borders and ranks and have little to fear from repercussions from their external penetrations and successes!
Malware, throughout this WP and specifically for security protection universally-speaking, the industry and VMware will use the term ‘anti-malware (AM)’ or malware as a reference, instead of anti-virus (AV). As a virus is specific to a legacy category of malware, while the latter is all encompassing. As we continue to explore these NextGen agents of malware it is also of interest to understand at which level within the Open Systems Interconnection (OSI) Model in which they attack.
Previous versions typically used application level attack but most of the more advanced and newer, state-sponsored ones for surveillance are doing so at the kernel or memory level. And although app level malware still is prevalent, many are becoming more modular, such as invasive spyware like ‘Hermit’. And without the right tools in place, company’s IT / SOC and SecOps teams will suffer the consequences. The best resolution beyond training, coaching and other personnel techniques is to provide the proper tools and configuration of both policies and procedures for detection and mitigating attacks before they get a foothold (see Beachhead) and if an intrusion occurs, be able to maximize the team involved efforts to root out the attacker(s). For mobile, Workspace One MTD provides for that EDR/IR extension to complete the NexGen - eXtended Detection Response (XDR) toolset.

Figure 5: Credit – VMware Global Threat Insight Report Metrics 2022
Most Popular Malware
So back to the money; a Trojan horse program can be more lucrative. This sort of malware being monetarily useful has now come to the forefront. However, once installed or within the perimeters of an enterprise or on those endpoints, it turns loose a slew of activities and executable instructions that can for example, attempt to infiltrate your databases for personal and financial info, install additional programs to earn per-installation cash, or anything the coders can think of to monetize such control of those devices, and such is the newer more recent flavor of malware,
Ransomware is a type of malware from cryptovirology that threatens to publish the victim’s personal data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system without damaging any files, more advanced malware uses a technique called ‘cryptoviral extortion’. So, Ransomware from a worm-based attack spreads without any help. It encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
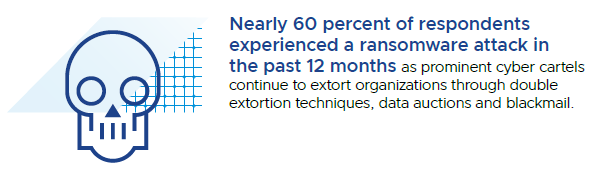
Figure 6: Credit – VMware Global Threat Insight Report Metrics 2022
Ransomware is an epidemic that companies can ignore. Malware attacks are becoming more pervasive and sophisticated, while ransomware as a service now targets governments and companies of every size. And the threat is growing: Globally, ransomware cost $20 billion in 2021 and is projected to cost $265 billion by 2031, according to Cybersecurity Ventures, and it’s just a matter of time before more sophisticated and mobile-born versions are available.
State-funded hackers <or> Advanced Persistent Threats (APTs) teams are well trained, well-resourced, and persistent. The use of new tactics, techniques, and procedures combined with more invasive malware can enable motivated malicious personas to move with previously unseen speed and accuracy. Any new security capability must be resilient to evolving threats and effectively reduce threat vectors, internal and external (more to follow on Zero Trust (ZT).
Other Types of Mobile-based Malware
Now that we’ve covered the background into the evolution of malware and some of the more prevalent types, below represents the most prevalent categories for malicious attacker tools today for mobile, as well as threats & vulnerabilities specialized for those devices, apps and communications. Other attacks in these categories include:
| Root Enabler | Bots | Adware | Riskware |
| Spam | Chargeware | Toll Fraud | Click Fraud |
Table 1 contains a list of the broader attack vector categories we'll be focusing on throughout the whitepaper and where each is aligned to, as well as the threats they pose and their resolutions:
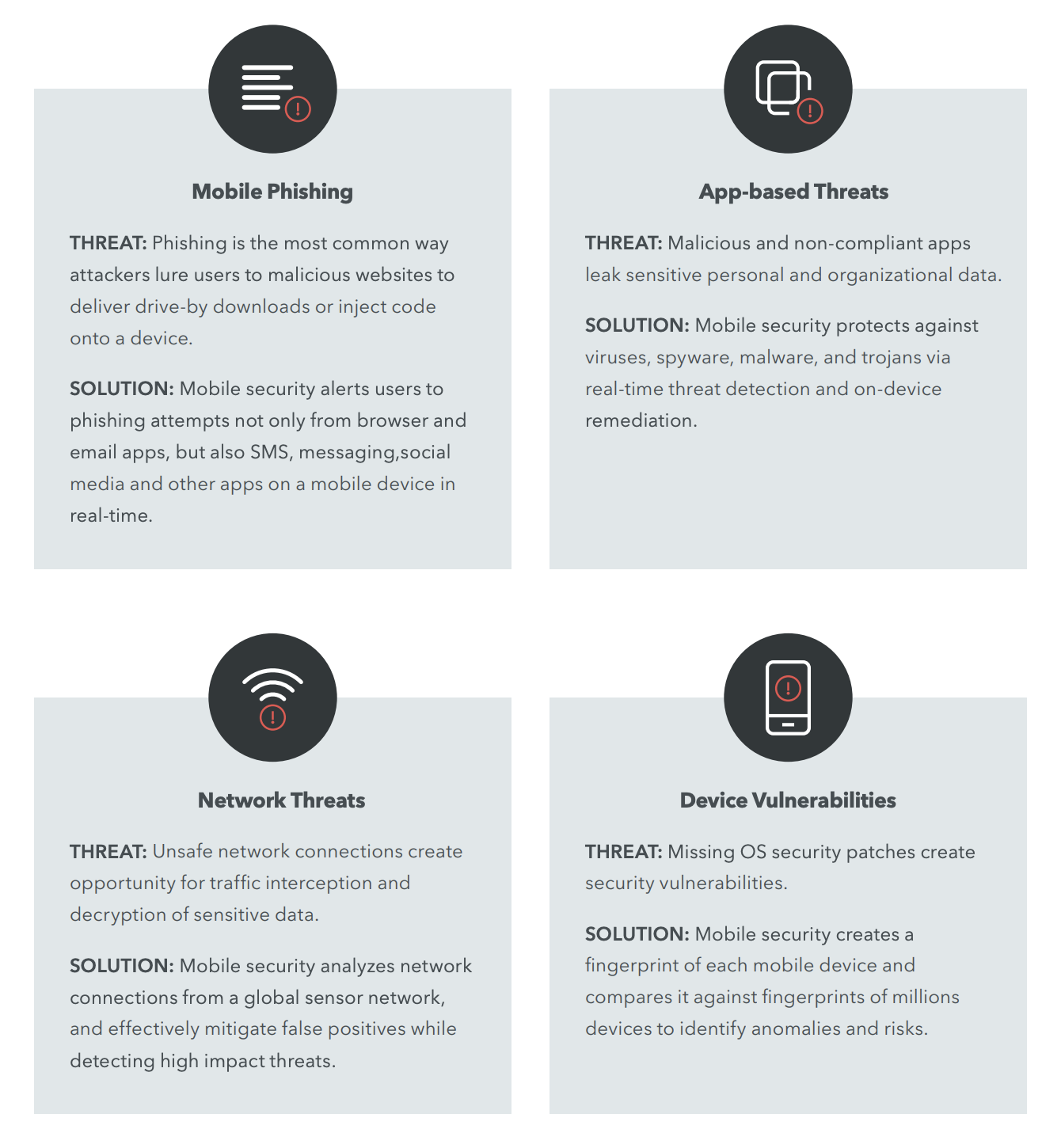
Table 1: Credit – Lookout, Business Case for Mobile Security
Beachheads
A beachhead is a temporary foothold created when an offensive unit reaches a landing spot and begins to defend the area as other reinforcements arrive <or> can establish an area of operation. Once a large enough unit or force is assembled, the invader or intruder can begin advancing further inward.
An example of this threat came to reality within the U.S. Gov't back in 2008 was when Russian malware made its way into the Secret Internet Protocol Router Network (SIPRNet) system by way of a thumb-drive which was plugged into classified-level computers accessing the network. This was even before another widely published and documentary movie-based attack on the Iranian Nuclear program, called Stuxnet that infiltrated and did significant damage to their centrifuge infrastructure of the plant through a similar means of an infected stick and gaining access to a closed network.
In both of these and other cases like them, the computers lacked virus protection due to their detachment from the internet and were compromised as a result. Worse off, they lacked any visibility into the intrusions erroneous and communications or activities from a program standpoint. Those viruses, once gaining access to these networks, acted as a 'beachhead' which allowed the transfer of data to foreign computers. The hack was, at the time, the largest compromise of US (United States) cybersecurity in history, and initially led to a ban on the use of thumb-drives. Although this was later repealed largely due to the addition of endpoint security and visibility afforded to traditional endpoints.
However, where this picks up in our discussion surrounds gaps in coverage for ‘all’ devices, including mobile-enabled ones. In order for these threat actors and their tools to get a foothold, often take several gaps in the defenses of a device, network and backend. And as the mobile device has 2 of 3 elements directly in the crosshairs, e.g. the app / web session, on the device and interacting over a wireless network based connection, this leaves the device’s OS, the app itself and the network in question, all as potential footholds to be used to gain access to the device, the app data or the communications being sent over that connection and ultimately to that backend server/service, cloud or enterprise hosted?
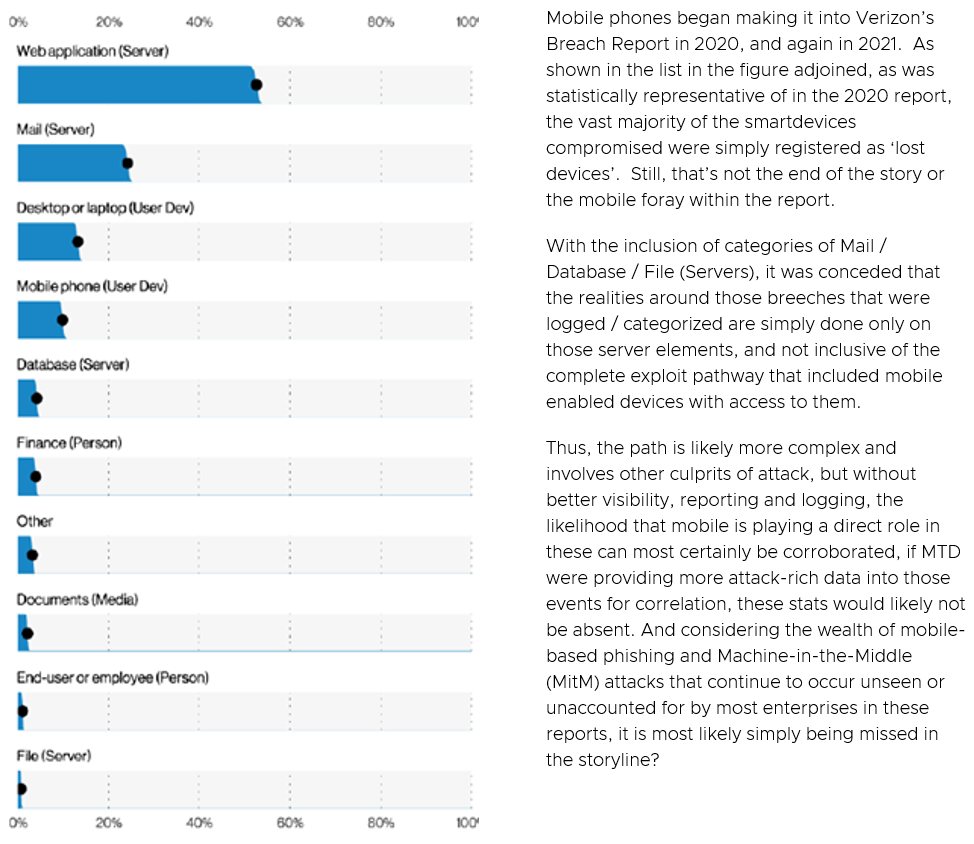
Figure 7: Credit – Verizon 2021 DBIR
Regardless, on a device, whether COPE / BYOD or otherwise, all these factors can be a challenge to manage without the right tools in place to not only enforce policies, controls and protection, but having visibility at the end-user level or admin level to protect against these numerous malware categories above <or> the intruder gaining a beachhead for even larger scale attacks through capturing / controlling the mobile device? Without active defenses that can detect anomalies activity on a device, how does an end-user or the admin managing the device know if there’s been a compromise? Without Workspace ONE MTD on a mobile phone / tablet, the answer is clear, they won't!
So, what’s a good, clean-cut, security-conscious organization to do? Based on the figure below, patching performance this year for organizations has not been stellar. Granted, it’s never been great. There are several likely hypotheses to explain why this year might be underperforming. The ideal state for any organization is to patch smarter, not harder, by using vulnerability prioritization (ex. Based off the CVE (Common Vulnerabilities and Exposures) lists) not necessarily just when the next release comes out?
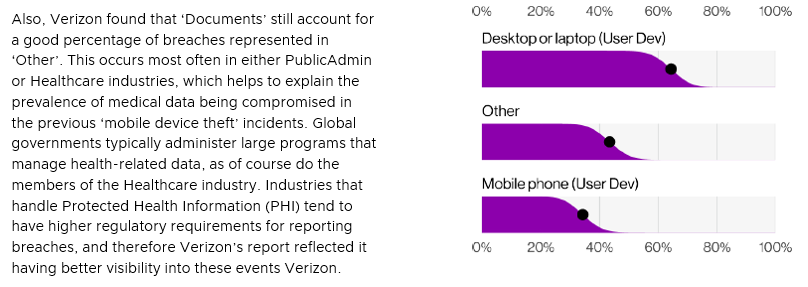
Figure 8: Credit – Verizon 2022 DIBR
Without visibility or the ability to detect a breach has occurred, “… you don’t know, what you don’t know”!
As cyberattack volumes have grown, the simultaneous and rapid pivot to remote working means businesses are more than ever not seeing the full picture of endpoint metrics for security. Coupled with erratic employee behavior, personal devices, and home network use reduce visibility, are creating blind spots and dark corners where attacks go undetected. Consequently:

Figure 9: Credit – VMware Global Threat Insights Report Metrics 2021
And when combining those factors, along with the fact that of the Top 5 Breach types from the report shows that 3rd party apps, out-of-date OS vulnerabilities together factor into over a third of the reasons they occur, it becomes imperative that organizations take note and serious the threat of a mobile-enabled attack and leverage the most feature and function rich tool they can deploy in protecting, detecting and defending against these potential beachheads and vectors through VMware’s Workspace ONE UEM & MTD.
Zero-Day Exploits
Taking in the threat landscape discussed above and where cyber attackers are focusing their efforts on either incorrectly configured, patched or protected systems, the zero-day exploit becomes a particularly insightful area to examine. “Zero-day” (Z-Day or 0-Day) refers to exploits that were not known to the public or the affected vendor at the time of discovery, thus no protection or patching are available. This gap leaves the community using the product, either closed or open-source (and scarier, open-source embedded into a closed-source, OEM software provider’s solution) unprotected from potential malicious actors configuring hacking tools to leverage the exposure against the code on customer devices etc.
Figure 10: Credit – VMware Global Threat Insights Report Metrics 2022
Google’s Project Zero team tracks and studies instances of zero-day exploits that were discovered in real attacks against users, and the data they’ve generated is truly astounding. Numerous zero-day exploits have been seen in the wild in the past 3 years.
Google has been tracking the activities of commercial spyware vendors for years and taking steps to protect people. In July 2022, just previous to this WP publication, Google testified at the EU (European Union) Parliamentary hearing on “Big Tech and Spyware” about the work we have done to monitor and disrupt this thriving industry.
‘Seven of the nine’ zero-day vulnerabilities our Threat Analysis Group (TAG) from VMware discovered in 2021 fall into this category: developed by commercial providers and sold to and used by government-backed actors. TAG is actively tracking more than 30 vendors with varying levels of sophistication and public exposure selling exploits or surveillance capabilities to government-backed actors.

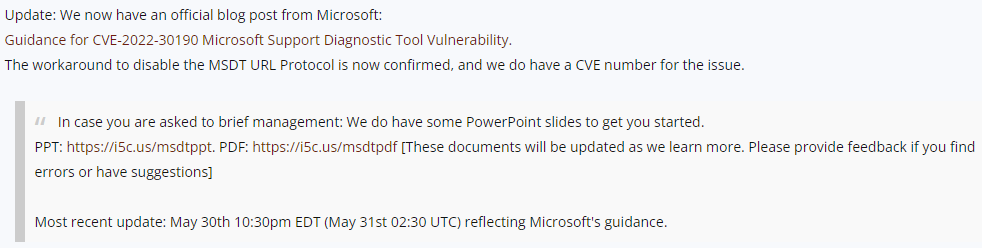
Note: The file is detected by only 17 antivirus engines on VT; when you open the file, nothing is displayed (it seems like a blank document), but, looking at the document specs, you see something interesting: The document contains an external reference pointing to a malicious URL.
Figure 11: Credit – Microsoft Support Team
Figure 11 is a classic example of a real-world threat that comes up time and time again. A new exploit discovered in the wild that was not present previously and only after the exposure to it is the alarm sounded and sometime thereafter a fix will be made in the form of an in-cycle or out of cycle patch depending on the severity. Only those AV engines with the most robust Artificial Intelligence (AI) or Machine Learning (ML) engines will typically root out the action based on ‘behavioral’ aspects of the malware, such as Workspace ONE MTD; and those that must rely solely on a ‘signature’ basis will fail to detect and protect against it.
These factors are why VMware partnered with Lookout to bring the industry the best of breed, the best Unified Endpoint Management (UEM) solution for enrollment, management, control, inventory, content/app enablement and enforcement with the best Mobile Threat Defense to provide true EDR/IR capabilities against known and ‘unknown’ threats that are based on behavioral detection through Machine Learning. And there is no more direct way to incorporate the Zero Trust Pillars or Tenets outlined from the source governing bodies on ZT (e.g. NIST & CISA) to provide visibility and analytics about the health and security of those mobile-enabled assets than to ensure your ability to protect the device and its network connections, the applications that reside on it and the data that those apps use, and for the authentication, automation and orchestration of that security model than through VMware’s Workspace One MTD.
Figure 12: Credit – CISA ZT Pillars
VMware’s Workspace ONE MTD solution provides for protection from each of the areas being attacked via mobile-enabled malware threats from Device / OS & Data-at-Rest > Applications > Web / Content (URL & Phishing) to Network-borne (communications in-Transit). Thus, it does not solely rely on static detection capabilities and regardless of the zero-day threat, the actions that it takes, whether to compromise the device, the app and it’s data, or if it’s a MitM attack against the in-Transit data transfer to the cloud or enterprise server resource, our MTD solution will detect and based on policies configured can help remediate those for your IT or SOC teams.
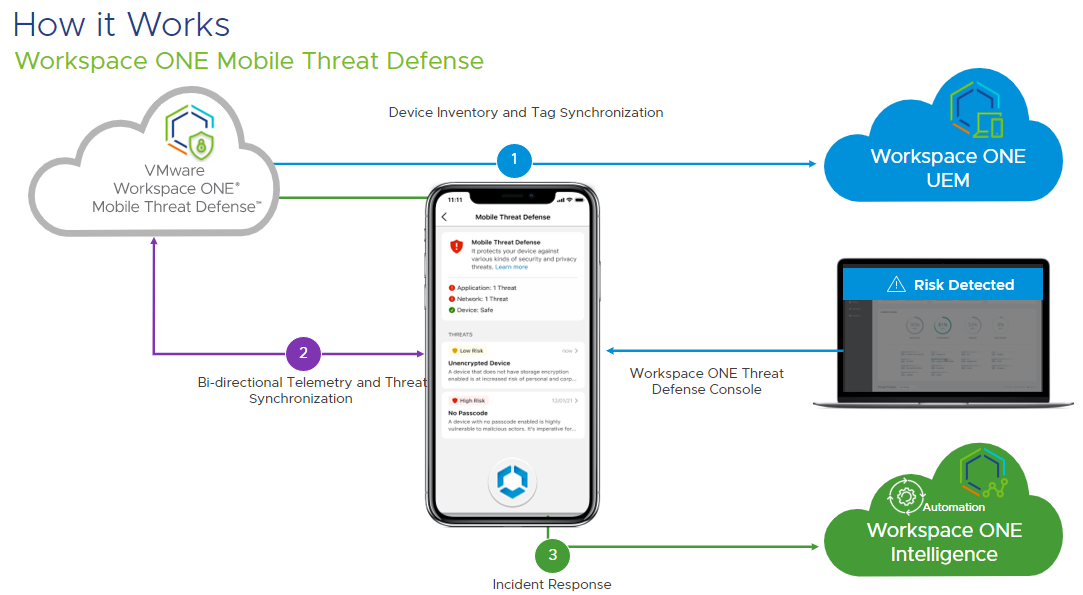
Figure 13: Workspace ONE MTD Detection, Reporting and Response for Remediation Overview
Malicious Activity Increasingly Focused on Mobile-enabled Services
VMware’s findings from the Global Security Insights Report, underscore the extent to which commercial surveillance vendors have proliferated capabilities historically only used by governments with the technical expertise to develop and operationalize exploits. This makes the Internet less safe and threatens the trust on which users depend.

Figure 14: Credit – Rapid7, Ransomware per industry from 2021
Apple’s high-profile release in Jan of 2021 of iOS 14.4, included security fixes for (3) critical Common Vulnerabilities Exposures (CVEs) being tracked by CISA / US-CERT and cataloged by NIST, that were said to have been exploited by hackers in the wild, and yet even with these alerts, nefarious parties leveraging tools like NSO’s Pegasus were once again able to bypass these security steps because newer zero-day holes are found.
Another example of the complexity being posed in today’s sophisticated actor world, Shlayer, a combo, downloader and dropper for MacOS malware is primarily distributed through malicious websites, hijacked domains, and One Updater as a fake Adobe Flash updater. In December 2021, malvertisement accounted for the greatest number of alerts. Malvertisement continues as the top initial infection vector due to Shlayer’s activity and that it’s iOS / mobile specific provides a glimpse of what could become the norm of the rest of the decade?
Fortunately, VMware’s Workspace ONE MTD protects against these combo- <and> zero-day attacks!
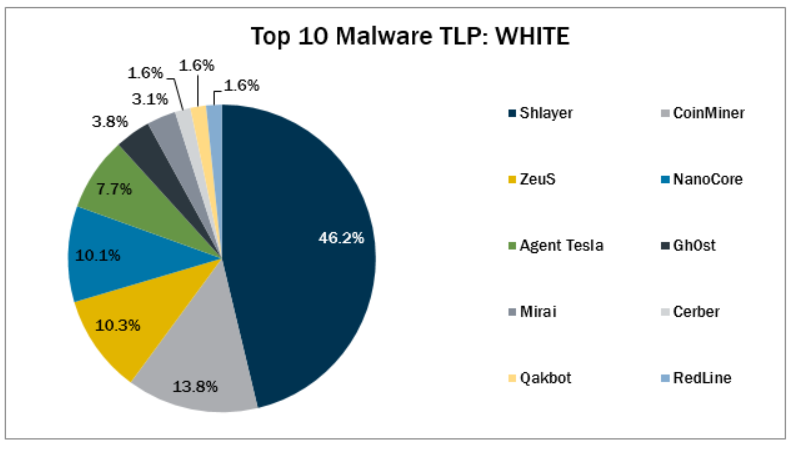
Figure 15: Credit – CISsecurity.org, Top 10 industry malware from 2021
Some additional, specialized categories for mobile threats and zero-day attack exploits that the VMware Workspace ONE MTD solution protections against are listed in the following table:
|
Dropped |
(A.K.A. Droppers) is malware delivered via other malware, which already resides on the target system contains an exploit kit, infected third-party software, or manually by a iOS threat actor. Current examples of this are > Mirai, and Qakbot. |
|
Multiple |
Malware that favors at least (2) vectors of vulnerability; current versions are > CoinMiner, RedLine, and ZeuS, which are all utilizing multiple vectors. |
|
Malspam |
Are contained within unsolicited emails, which either direct users to malicious web sites or trick users into downloading or opening malware. Top 10 Malware using this technique Agent Tesla, Cerber, and NanoCore. |
|
Malvertisement |
Malware which is introduced through malicious advertisements; currently the Shlayer variant, and although it is the only Top 10 Malware using this technique and specific to targeting mobile, it is currently #1 on the list of Top 10, according to Center for Internet Security. |
Table 2: Other Zero-day Malware Categories
Mobile Code Vulnerabilities
In today’s fast-moving and get to market first mentality, code quality assurance is typically designed around the end-user experience or user-experience (UX) which has been most often associated with how the app or operating environment best works for the app or device interactions with the end-user. Cybersecurity measures, although they have improved since the wild-west days of the early 2010s, still have gaps and those gaps can be exploited. Thus, it is imperative to operate for an agency or enterprise under the notion that the devices, the operating systems and the apps running on them, could be a potential supply-chain risk and must not only be vetted prior to deploying, but also have ongoing visibility into their dynamic activities when engaging with data resources of the organization from a business and enterprise aspect. It is challenging enough to concern oneself with their own financial or confidential data, it’s another to be legally or regulatory wise for others.
Below is a list as of July 2022 for active CVEs for both Android OS Apple iOS/iPad OS with their corresponding Common Vulnerability Scoring System (CVSS) scores included with the Known Exploited Vulnerabilities Catalog (KEVC). This is a living list of known CVEs that carry significant risk to the federal enterprise (but also all external organizations) and should be monitored and tasked for evaluation and deployment as well.
But as for the Binding Operational Directive (BOD) 22-01, it requires US FedCiv agencies to remediation of specified vulnerabilities by the due date to protect U.S. Federal Civilian Executive Branch (FCEB) networks against active threats. Notice below the red font for the more severe details for the CVEs, the highlights of the potential exploit and the bolded dates of the vulnerability being added to the catalog and the atypical 6-month window until the agency has to apply / fix the systems in question. But again, this time-window, although a best practice is only targeted for U.S. federal systems; other entities are not so required and iOS take longer to apply the fix in question, leaving potentially a longer window of opportunity open?
As you can correlate from below, it is a continuous cat & mouse game that never ends. Although both vendors have a reputation for making attentive efforts to provide timely patches in the form of both .dot releases (x.Y) and incorporated in new versions (#.0) of the OS, it is only a matter of time before malicious actors leverage that window, or what is more crucial, the typical time it takes for users to perform or allow performing updates on their devices within their control? And as noted, this can be up to and longer than 6 months in many cases.

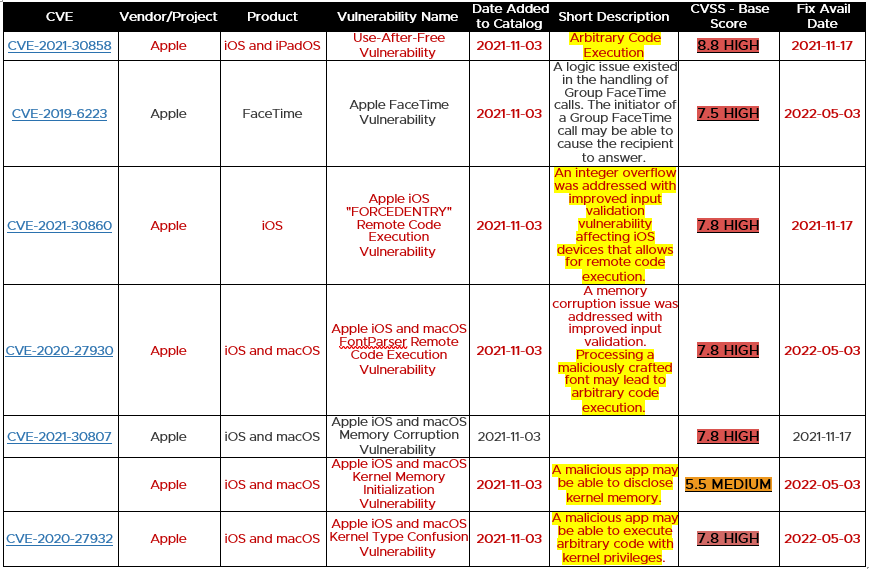
Table 3: Credit – US-Cert / CISA list of active CVEs for mobile from 2021 >2022
So, in lieu of waiting on the OEM to provide a patch, or for the deployment of it onto all mobile devices, the only true way to protect users / devices and most importantly the data they access is to leverage protection and visibility onto those endpoints. Thus the necessity for Mobile Threat Defense and even more importantly, one with an integrated UEM & MTD that can provide for not only detection, but alerting to both the end-user, Security Operations Center (SOC) or Information & Technology teams <and> provide for automated remediation, such as with VMware’s Workspace ONE MTD.
The timing of discovery and ‘time to patch and apply the fix’, leads us to our next topic. Zero-day attacks, or attacks in which there are ‘0’ days’ notice prior to an exploit being available and used in the wild against targets. Google several years ago decided to develop a specific group, called the Zero Day Project where they are charged with discovering, notifying the industry, and tracking vulnerabilities such as this. Below is an excerpt from one for Apple iOS from 2022 and a table from Google’s Zero-day project metrics collected regarding ‘exploited ‘In-the-Wild’ Z-Day exploits for mobile:

Figure 16: Credit – Google’s zero-day; exploited vulnerabilities year over year stats
From these stats and the 1H22 zero-day log below alone, it’s easy to extrapolate the growth of mobile-focused attacks and that it will continue to rise as a linear average over time, as these base years modeling that provide an upward trajectory as they continue becoming increasingly popular for remote teleworker use for doing business both within public and private sectors across the globe, meaning mobile devices will continue to store and access more sensitive, business-related data and relevant applications. Thus, if these devices fail to be secured at the same level as traditional windows or desktop endpoints, they’ll represent a potentially bigger focus for nefarious agents and attackers looking for the weakest link in the chain.

Table 4: Credit– Google’s zero-day; exploited vulnerabilities year over year stats
As can be seen, no OS or OEM is shielded. This year has seen some high-profile malware found, including at least (6) different apps disguised as legitimate anti-virus apps Dubbed “Sharkbot” the malware steals credentials and banking information from Italy and the UK, truly making emphasizing this global issue.
Mobile Vulnerabilities into 2022 and Beyond
Early 2022 tracking of all major vectors e.g. Apps & OS’s, clearly reinforces the previous section. When you combine the above Table 4’s tracking of Chromium, those and the ones in Table 5 emphatically provide concrete evidence that indeed ‘no OS or OEM is shielded’. As these Common Vulnerability & Exposure (CVE)s from MITRE > CISA continue to pile up, each is providing a window of opportunity for a malicious actor to take advantage of while the OEM is developing a patch, or by the time that the end-user gets one or actually ‘implements’ it?


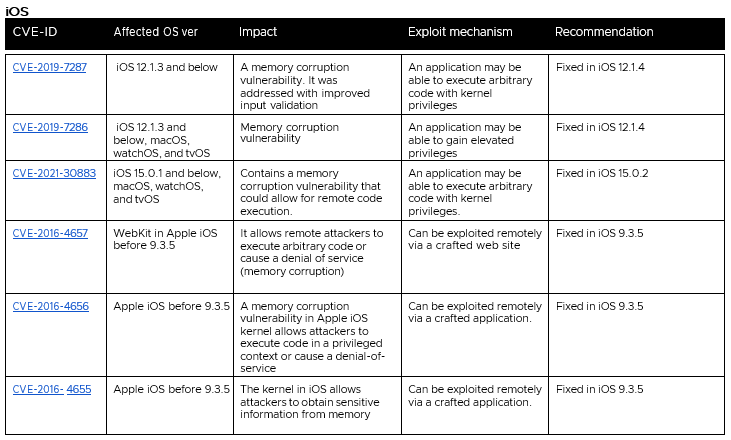
Table 5: Credit – Lookout Threat Lab, Mitre / CISA CVEs for Mobile 1H22
Additional Industry Mobile Threat Insights
Below are some additional highlights from different areas of perspective and insights, that when taken as a whole, can provide some truly relevant and tangible details for mobile security that provide some additional validation of VMware’s and the other referenced industry take on mobile vulnerability over the past two years, from regional aspects to vendor specific to industry compromise and malware details and stats:
- Global: In 2021 there were just under 3.5 million malware installation packages globally - with the majority of these in countries such as Iran, China and Saudi Arabia. In Iran specifically, almost 40% of mobile users were attacked by phone malware. And although malware is present all over the globe, some countries have it worse than others. Iran, Algeria, and Bangladesh have the highest percentage of mobile malware victims, with near ~ 39, 21, and 18% respectively.
- Incident Rate: A malware incident has affected 36.5% of organizations; Once the malware is installed on a mobile device, it can secretly steal all data about the user and potentially grab the work-related information.
- Google: The Google Play Protect scans over half-million apps; no enterprise can stay on top of the validation of the apps from even the trusted sources themselves and VMware’s partner, Lookout is a part of that app scanning solution
- Apple: iOS faces less than 1% of total mobile malware threats; and although in the past it’s been truer that it was harder to penetrate an iOS device security control, it’s possible to breach as has been shown repeatedly via the NSO (see Pegasus). XcodeGhost was the most famous iOS malicious code back in 2015. It was inserted into iOS apps via tampered Apple Xcode and made its way to the Apple App Store. It has been the largest attack on the Apple App Store thus far, but not the only one since.
- Obscurity: In 2020, nearly half of malicious apps were hidden from an end-user and could make up almost half of malicious telemetry. By hiding their presence on the devices, they can project ads to users as bait-click and can be extremely hard to find on the device and uninstall and can consume lots of system resources as well.
- Trusted Apps: Even Apps with a 4.5 star have proven to be scams or be providing data and skirting privacy see SharkBot above & WhatsApp / TikTok (= Russian / Chinese hosted backend servers configured in the apps)
- SMShing: Thousands of people a year are victims of SMS phishing (A.K.A. smishing) attacks as more people have started using mobile phones for banking, and cybercriminals have found a way to obtain their data. They send fake SMS or other mediums, such as in-app messaging or vendor platform messaging (ex. Apple’s iMessage), pretending to be the bank, asking users to click on a malicious link that steals their confidential information. These typically fall out of the normal corporate domain and can be missed by permitter / network defenses for that reason.
Recently, phone numbers of close to 1,900 Signal app users were exposed in the data breach Twilio cloud communications company suffered at the beginning of the month. Twilio provides phone number verification services for Signal and last week disclosed that an attacker hacked its network on August 4, 2022, and confirmed that data belonging to 125 of its customers was exposed after the hackers gained access to Twilio employee accounts by sending them text messages with malicious links.
Two other high-profile cases involving financial institutions PayPal and Zelle, were both having their potential customers harassed by ingenious fraudsters with adaptive hijacking methods by leveraging the very same tools that those financial institutions have long taken advantage of, to serve those same clients in order to make those customers feel safe about transacting online. Thus, it’s no wonder why the incident rates are some of the most prolific scams going currently. The Zelle Fraud Scam for instance, started with an SMShing message about an unauthorized payment appearing to come from a customer’s legitimate bank. After all, financial institutions have spent years encouraging customers to sign up for mobile alerts via SMS about suspicious transactions, and to expect the occasional inbound call about possibly fraudulent transactions.
Also, today’s phishing artists are less interested in stealing a PayPal or Zelle login verses your entire computer and online life with remote administration software, which seems to be the whole point of so many scams these days. Because why rob just one online account when you can plunder them all? No option is left off the table for today’s attacker, including this author’s own Yahoo account.

Figure 17: Credit – Reddit & Yahoo
The best advice to sidestep phishing scams is to avoid clicking on links sent through emails, text messages and other mediums, but relying on the diligence of users to be able to navigate the minefield of today’s environment of sophisticated Spear-SMShing attacks arriving in the busy, inattentive or distracted end-user isn’t realistic. Most phishing scams invoke a behavioral element, praying on them to take immediate action or dire consequences will befall the individual or their organization they represent. Complicating this on the mobile end are device screens, that although are superior to those of 1st generation quality can still be difficult for the user overusing a standard PC-based browser or client to view the details. The URLs are often truncated and hard to read, disappears on scrolling and you can't hover over a link to validate it. MTD’s Phishing protection can provide the analysis and protection necessary to keep these end-users out of harm’s way.
- Adware: ZDnet reported that 2.5 million people downloaded multiple mobile adware apps that typically take data, not related to the app itself and provide it back to the malware developer’s servers / storage. More than (7) different adware apps were downloaded from Google Play & Apple App stores thousands of times; these apps were promoted on TikTok and other social media by simply showing an aggressive pop-up ad to end-users, asking them to click to remove it. These apps can be laced with identity and privacy capturing capabilities.
- 3rd Party Appstores: 6.8% of iOS and 3% of Android devices are connected to third-party app stores, and these app stores can be a source of threats and typically require end-users to have to jailbreak their iPhones and root / configure their Android devices, making them more vulnerable.
- OS Compliance: 29.1% iOS and 0.7% of Android OS-based devices run on old / outdated operating systems; the percentage of users who don’t update their OS is down for Android but up for iOS. Software vulnerabilities are common and being unpatched is one of the most important security updates of all and without so, provide space for malware to take advantage of and perform malicious activities on them, e.g., data exfiltration.
- Jail/Root: 50% of iOS and 20% of Android users jailbroke and rooted their devices in 2019. Because of this, users can deliberately and ‘inadvertently’ install unauthorized apps and might be unaware of what they’re installing.
CISO Concerns on Malware as Drivers
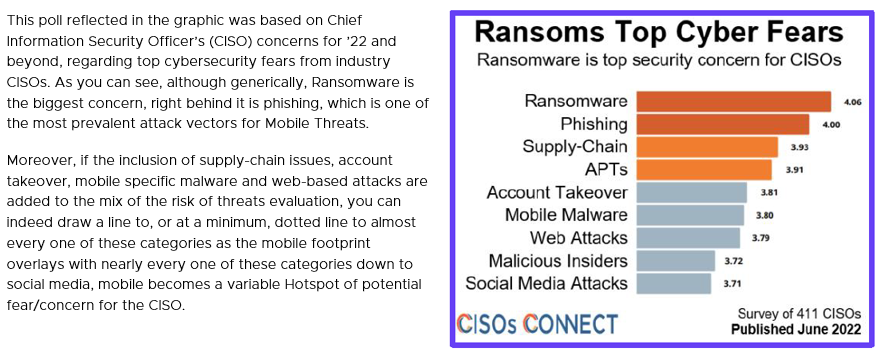
Figure 18: Credit –CISOs CONNECT
Threat Landscape Report Drivers for MTD
Through the release of VMware’s annual Threat Analysis Unit (TAU) Threat Intelligence Report Landscape Report, several key summations could be made regarding different data collection around findings observed through millions of networks, network segments and endpoints from was highlighted in the report. And in that report, coupled with the Verizon Mobile Index Reports, as well as Lookout’s own Threat Lab analysis and collection data, were details specifically regarding threats that evaded perimeter defenses and were identified by VMware sensors placed inside the perimeter or on Lookout’s endpoints, where key findings and conclusions could be made about the upcoming future in Mobile Endpoint Security.
3rd party apps and ransomware are the leading breach causes
Three vectors almost tied at the top to build a picture of external threats and internal weaknesses. Third-party applications were the most common culprit, followed closely by ransomware and out-of-date security technology. The rapid pivot to work from anywhere has exposed organizations that had lapsed in security hygiene and failed to implement multifactor authentication, while process weakness and OS vulnerabilities were also common causes of a breach.
Mobile devices have their own specific risks
Just like their big brother, the laptop, they can be lost easily, which can lead to the exposure of sensitive data on them, but often the biggest impact when they are is on the end-user's productivity. And because they are often used in public places—depos, stations, airports, and coffee/bistro shops—the devices are more susceptible to eavesdropping, especially when combining the inherit nature of end-users to connect to unprotected / untrusted Wi-Fi hotspots. Security required for a mobile platform and its ecosystem require unique and custom tools for protection = VMware MTD.
But it’s simply not just Over-the-Air issues; since 2015, when the NSA divulged that a cable could be configured and used to exploit the device or network hardware as targets for espionage. One of those tools was a USB cable with embedded hardware called Cottonmouth-I and since then, cheaply obtained cable versions for both Android and Apple-based hardware, that are well under $100 can be obtained and have been increasingly leveraged over the last 5 years to include ones with wireless transponders to bridge them to the target system, in order to send executables from a Command & Control (C2) server in order to place malware on to collect or eavesdrop data from an agent or worse, take control of a device.

Figure 19: Credit - NSA / OMG Cables / L.A. DA Office
Another favorite target to infect a smart device, is through public charging stations, called ‘Juice Jacking’ in such as at airports or convention centers contain the malware within the port hardware and when plugged in, transfers it onto the unsuspecting device for similar effect as the cable. Without a detection and response for the endpoint that can see these attacks as they occur on the device, they can be taken advantage or control of for nefarious purposes, including both personal and enterprise exposure. Workspace One MTD can detect, warn and help mitigate these attacks.
Mobile platforms will provide gateway risks for the enterprise
Attackers have proven that they are creative and only need a gap in the supply chain to take advantage of a large scale of victims. And they can exploit mobile devices to acquire data from the cloud and other systems that those mobile-based platforms connect to; so those hackers can also be attacking and capturing credentials tied to enterprise use, which can then be used to gain access to data in other organizational systems. Thinking of malware as you would specific ingredients for baking, attackers will incorporate new innovations into the ‘mix and match’ with other proven ingredients and keep at it until they find one that works. When you couple that ~ 70% of enterprises expect work-from-home (WFH) or remote to remain in place or even continue near current rates post COVID-19 even after it’s no longer an issue.
The use of spyware will continue to grow
The fact that we carry our mobile devices everywhere we go, and that these devices have GPS, Bluetooth, and so on, makes them fertile, potentially lucrative targets for spyware. What is more, spyware is readily available. New releases are being developed not only by known developers that operate in the same market as Pegasus developer NSO Group Technologies such as RCS Lab and Gamma Group (the latter which created FinFisher). These vendors are collectively branded as “lawful intercept” companies, where they claim to only sell to customers with legitimate use for surveillanceware, such as intelligence and law enforcement agencies.
In reality, such tools have often been abused under the guise of national security to spy on business executives, human rights activists, journalists, academics and government officials. for malicious purposes, versions are shared privately, and commercial versions can be found on common forums like GitHub and Reddit. Spyware (or Stalkerware) is becoming more common place and can get everything from the mobile device, including data, credentials, and more. As in the case of the recent version, Hermit, named after a distinct server path used by the attacker’s command and control (C2), is a modular surveillanceware tool that hides its malicious capabilities in packages downloaded after it’s deployed. For these very reasons, we expect the use of spyware / stalkerware to target mobile devices will continue to proliferate beyond 2022.
A complex supply chain enables malicious actors and will continue to grow
You don't have to look deep into the fabric of the state of cybersecurity and incidents like ‘SolarWinds’ or ‘Apache Log4j’ to understand that the global community is a tightly woven and increasingly ‘interdependent’ state on a global ecosystem of supply-chain for hardware & software. A single or a combination of providers leveraging widely deployed utilities within public and private sector intuitions can wreak havoc if a vulnerability is exposed and either remediation is not available or not heeded prior to the malicious actors taking advantage of them? From a directly mobile aspect, there are few better examples than was in the case of Jeff Bezos’s iPhone hack, vulnerabilities in both the iOS code and a mobile app ex. WhatsApp, coupled with an unsuspecting end-user that was improperly defended by MTD, created this perfect supply-chain storm for an opening by a dedicated and professional actor or force to have initiated these exploits.
As was detailed in multiple analyst summaries of the event, as could be gleaned through Apple’s own security updates for iOS and iPad OS, version 14.4 had (3) code defects opening holes to any device with it installed, which may have actively been exploited in the attack. Coupled with the undetected launch of the attack by Bezos clicking on a contact for download through a popular messaging app ‘WhatsApp’ that it too lacked appropriate security parameters to guard from this, he was unaware of the intrusion as it appeared to be from a trusted contact/source, which then initiated the exploit that was launched, and a great deal of communications and private information was extracted from his device and to others he communicated with.
Since there are more mobile devices being used for both, Bring-Your-Own-Device (BYOD) and Corporate-Owned/Personally-Enabled (COPE) than traditional endpoints, custom visibility, security, and remediation tools are necessary. When you couple that scale and from the fact that nearly 100% of those devices are deployed onto 1 of 2 OSs from either Google’s Android or Apple’s iOS/iPad OS, the supply chain failure potential is extremely magnified.
Threat Landscape Conclusion
When you add into perspective devices interaction with enterprise data, via custom and commercial apps, the more ubiquitous risk that is introduced if one or both vendors have gaps in either the OS security or the app community. Tied to the ever-present truth, that dev teams most often don’t have a security mindset or simply aren't impowered to provide a DevSec path prior to deploying an app to production or the storefront will continue to enlarge this footprint for a beachhead in the coming years from the supply-chain for mobile.
First, software developers create applications by assembling and embedding existing open source and commercial software components to accelerate speed to market, as was obvious in the case of the Log4j issue. But in most cases, they are unaware of any security that was added or developed. Secondly, developers don’t update these components nearly 80% of the time as they can’t keep up with the updates and don’t want to fix something that’s not broken in lieu of assuring the production of the software continues timely to be deployed.

Figure 20: Source - The Hacker News, Chinese threat actors using Rootkit in popular supply-chain OEMs to infect systems
Rogue or compromised wireless networks will continue to provide a vector of compromise
Both the U.S. based MITRE organization and National Security Agency (NSA) track and provide guidance on mobile risks and this threat landscape for wireless-based attacks against mobile devices. In 2021 they provided the following guidance and summary on [Securing Wireless Devices in Public], where they stated:
“The risk is not merely theoretical; these malicious techniques are publicly known and in use... Accessing public Wi-Fi hotspots may be convenient to catch up on work or check email, but public Wi-Fi is often not configured securely. Using these networks may make users’ data and devices more vulnerable to compromise, as cyber actors employ malicious access points (MITRE Technique [T1036] - Masquerading), redirect to malicious websites, inject malicious proxies, and eavesdrop on network traffic (MITRE Technique [T1040] - Network Sniffing).”

Figure 21: Credit – Reuters, China machine-in-the-middle attack for mobile via cell network
When aggregated together for the increase in corporate use of Cloud-hosted apps and resources has climbed to almost 50% of all workloads today, the reliance on internet accessible enterprise productivity requirements can put traveling or remote users at risk? Those users will often find the most convenient, easily accessible access for connectivity, or simply forget or be unaware that they’ve universally granted access to join what are seemingly known networks (ex. Hilton Honors / Marriott Hotel Wi-Fi APs). Typical risks they are subjected to include but not limited to:
- Data sent over public Wi-Fi, especially open public Wi-Fi (e.g. Hotels / Restaurants / Bars / Bistros / Events) that don’t require a password to access is vulnerable to hackers that include eavesdropping, data exfiltration and host take-over:
- Once connected, malicious actors can decrypt even encrypted traffic if they discover the pre-shared key.
- Other MitM attacks can be leveraged with other radio frequencies ex. Cellular based, as were and have been used in eavesdropping toolkits, such as ‘Stingrays’ and can advertise stronger cellular base station signals and get unsuspecting users to connect, handshake and decrypt traffic going over them
- They can also sometimes get the network connection to downgrade into using insecure protocols or obsolete encryption algorithms through downgraded services ex. 5G to 4G or Transport Layer Security (TLS) to Secure Socket Layer (SSL).
- Malicious actors can set up fake access points, also known as a rogue or evil-twin, through a falsity within layer 2 of the OSI model protocol, that can mimic actual, nearby public or business Wi-Fi APs; once connected and joined through some basic ‘acceptance’ clicks, the hacker can gain access to all the data sent over that connection point.
- And when running your business or agency through a remote session such as these, it is entirely possible, without protection for the mobile endpoint to provide an attacker access to valuable cloud-hosted data.
- And as shown in the Figure below, nation-state attacks from either the supply-chain side as with Huawei cellular gear, or simply those within the geographical areas of foreign countries often have backdoor access to those access points and can target, intercept and eavesdrop on voice and data Comms that register and establish connections over them.
Mobile phishing encounter rates that provide another vector of compromise
Several of the forms of phishing, whether SMShing or through email or other messaging application-based URL links all relies on one of two key aspects, a user either making a mistake or getting tricked into a social engineering effort through this malware insertion effort A.K.A. scareware. Training is NOT enough, even pros or highly security-aware individuals can fail to keep their eye on the ball even once. An anti-phishing tool must be used to ensure the protection of this new, prolific predator that is global and on many fronts.

Figure 22: Credit – Lookout, Threat Lab global mobile phishing map
Our MTD can detect and block phishing attacks across any mobile app, stopping employees from exposing credentials or downloading malicious software. Lookout Phishing Protection works across both work and personal email, text messaging (both iMessage and SMS), any social media platforms, as well as all messaging apps like Slack, Skype for Business, and WhatsApp and the stats on phishing are staggering when you account for the scale and scope of the number of projected devices worldwide this represents below.

Figure 23: Credit – Verizon, MSI Report 2022
Mobile Protection Summary
Prioritizing and improving the visibility of organizations has been a key problem that is being exasperated from the rapid switch to home and remote-based working. The true scale of the attack footprint for mobile is indeed hard to discern because defenders can’t see into the corners where personal mobile devices are, while home networks have been grafted on to the corporate ecosystem. Add to this the challenges of monitoring third-party apps and vendors hardware, firmware and operating systems (OSs), along with the sheer quantity of blind spots, put simply, defenders don’t know ‘what they don’t know’, thus businesses are exposed as a result and any potential risk to threat ratio for mobile begin to escalate the matter.
This limited contextual insight into risk puts defenders at a disadvantage when protecting the extended attack surface. Organizations must prioritize improving visibility into all endpoints and workloads to secure the remote work environment. Robust situational intelligence that gives context to threats will help defenders prioritize and remediate risk with confidence.
This leads us to the summation point of the whitepaper, in it there is only one answer for the mail, in regard to mobile platform security and assurance; Mobile Threat Defense provides this visibility into all aspects of the mobile platform operation and use ecosystem, when coupled with Unified Endpoint Management, it clearly has an advantage that few solutions provide in this space and can provide attestation for MITRE’s ATT&CK for Mobile Matrices, that represent the real-world tactics and techniques (TTPs) representing involving device access and network-based effects that can be used by adversaries without device access for both Android and iOS-based platforms and is represented below in this increasingly larger mobile-based attack surface:

Figure 24: Source – MITRE, ATT&CK matrices for mobile
Organizations must prioritize improving visibility into all endpoints and workloads to secure the remote work environment. Robust situational intel that gives context to threats and will help defenders prioritize and remediate risk with confidence and meet the MITRE alignment’s unique aspects from real-world attacks.

Figure 25: VMware Workspace ONE MTD alignment with MITRE matrices
Organizations must prioritize improving visibility into all endpoints and workloads to secure the remote work environment. Robust situational intel that gives context to threats and will help defenders prioritize and remediate risk with confidence and meet the MITRE alignment’s unique aspects from real-world attacks.
Workspace ONE MTD Solution
Today’s technology infrastructure is complex; VMware products aim to simplify that infrastructure and develop a more secure environment for customers. VMware’s approach to enabling them to meet regulatory controls includes compliance kits, validation of capabilities, and VMware products’ ability to meet compliancy requirements (for example, General Services Administration (GSA) – Federal Risk & Management Program (FedRAMP)), as well as producing a framework focused on assembling products to a holistic compliance solution. This same enablement can be leveraged by DIBs (Defense Industrial Base) to address the practice control groups for CMMC (Cybersecurity Maturity Model Certification). But most importantly when considering key aspects of mobile endpoint, there is no better source than the recommendations that are structured around the (5) functions in NIST’s Cybersecurity Framework (CSF), which is widely recognized is also based on ISO standards that takes input from both public and private sector organizations and academia. In it, they detail the most helpful aspects of Cybersecurity and can tie directly into mobile as well.
VMware prioritizes each of the (5) domains of the CSF:
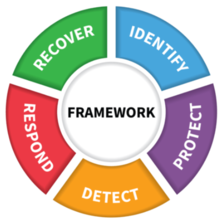
Thus, ensuring that data protection and system security within an enterprise through Workspace ONE and its core components. The framework incorporates both EUC and cloud-hosted product capabilities to enable a customer to perform controls required for compliance product capabilities and leverage those including ex. existing NIST SP (Special Publication) 800-53 FISMA & 171 for Controlled Unclassified Information (CUI), as their foundational security framework to create a series of standards and baselines. These are also reflected in NIST’s SP 800-207 Zero Trust Architecture and CISA’s Zero Trust Guidance previously referenced (stay tuned next month for the 2nd edition and follow-up to the MTD Drivers series with expanded details on the different global compliance, regulatory and framework factors for MTD usecases)
The VMware EUC product portfolio is made up of Workspace ONE, a digital platform that delivers Unified Endpoint Management (UEM) for most end-user device types, and provides device, application, content/end-user experience management, an app store/catalog, and identity & access management (IdM/IAM), as well as an integrated service to provide access controls, application management, single sign-on (SSO), data loss prevention (DLP), securing browsing, conditional access, and multi-platform endpoint management technology that also provides for the standard aspects of Mobile Device Management (MDM), Mobile App Mgt (MAM), including App Storefront (MAS) and integrates with virtual application delivery via VMware Horizon on a common identity framework, including:
WS1 = UEM + Access + Hub Services + Intelligence + Assist + MTD + Horizon
Figure 26: VMware EUC portfolio logical view with product links
And lastly, Workspace ONE Mobile Threat Defense (MTD) is an embedded MTD agent within the Hub client providing a single source for on-device, truly integrated and automated endpoint protection for mobile-enabled devices for a true Zero Trust security for the device, the data it's accessing through applications and phishing detection. Mobile Threat Defense (MTD) specifically provides endpoint security and protection for iOS, Android, and Chrome OS, securing devices against app, device, OS, and network-based threats providing the last leg of the Cyber Security Framework (CSF) domain functions of (Detect & Protect) and both MTD along with the UEM integrated features ensures that (Respond & Recover) both are enhanced as well!
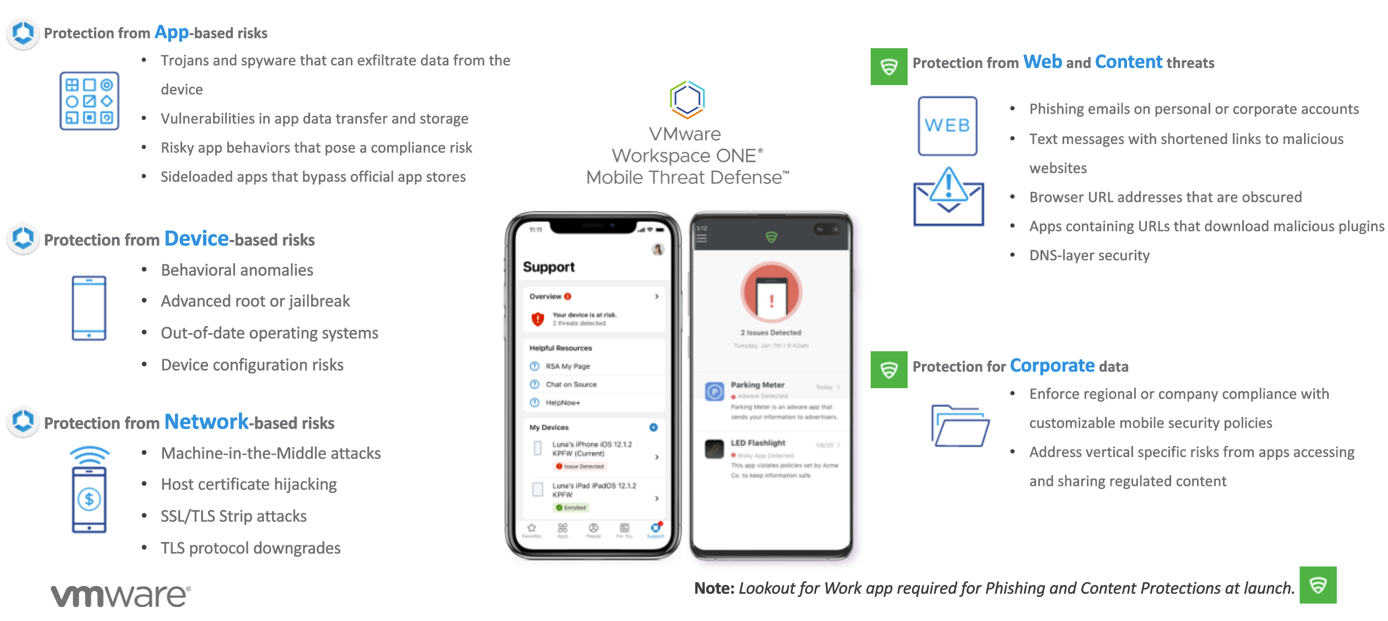
Figure 27: Threat vectors & components of risk for Mobile Protection with UEM & MTD coverage mapping to CSF
Integrating Mobile Threat Defense with Workspace ONE UEM empowers your organization to adopt secure mobility without compromising productivity. It allows the integration of mobile security threat and device events into your security incident and event workflows. Additionally, Mobile Threat Defense allows you to streamline the management of devices and drive enforcement when threats are detected, while complying with whatever framework you may need to or for industry insurance etc.
Note: Stay tuned for the release of the follow-up to this whitepaper, ‘Industry & Regional Drivers for MTD’, This whitepaper focuses on the best use cases for market & global segments for MTD.
Additional Resources
Lastly, VMware is committed to supporting the extended ecosystem / supply chain worldwide as is the case for MTD and we continue to expand our compliance programs to meet the requirements of the most demanding missions.
VMware Security Compliance
For more information on Security Compliance, see the following:
- VMware Global Ransomware Center
- VMware Product Partner Trust Center
- VMware TechZone Security Portal
- VMware TechZone Public Sector Compliance Portal
- VMware’s 2022 Global Incident Response Threat Report
- VMware’s 2021 Global Incident Response Threat Report
- Gartner Magic Quadrant for UEM Tools Report 2022
- Verizon MSI Report 2022
- Verizon DBIR Report 2022
VMware Workspace ONE MTD Technical Resources
Subscribe and look for our enhanced tutorial and design considerations guideline on Digital Workspace Tech Zone for Mobile Threat Defense!
- Tech Zone – Workspace ONE Mobile Threat Defense in Action (Demo)
- Tech Zone – Workspace ONE Mobile Threat Defense Technical Overview
- Tech Zone – Workspace ONE Mobile Threat Defense Architecture and Integrations
Lookout Mobile Threat Metrics and Countermeasures
With intelligence derived from more than 100 million analyzed apps, VMware’s MTD powered by our partner Lookout, has the world's largest mobile dataset, providing visibility into the entire spectrum of mobile risk over numerous industries and geographical regions. This enables Lookout to provide the greatest visibility into true, real-world app-based risks. Their security platform creates a fingerprint of each mobile device and compares it with data from more than 185 million devices to continuously protect against mobile risks. Thus, it provides a unique vision and telemetry into those arenas and help provide true, tangible data regarding threats that exist to these environments.
Every day Lookout inspects more than 100,000 new apps, of which up to 10,000 are often detected and labeled as malicious by their AI Threat engines. The customers through the App Risk analysis are able to quickly identify risky app behaviors and dynamically deny apps to protect their organizations.
Lookout’s detections of app threats around the world powered by the Lookout Security Platform, per industry are included along with industry and VMware analysis to provide a snapshot of key markets, sectors and geographical areas related to threats to the mobile ecosystem and key in on these threat classifications:
While the nature of cyberattacks will undoubtedly continue to change in unexpected ways, there are some clear trends that we see today that should inform our plans and initiatives. To learn more about our assessment of emerging trends, be sure to view our partner’s library at: Lookout Resource Library.
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2022/08/19 |
|
| 2022/08/09 |
|
About the Author
Andrew Osborn is serving in a role at VMware as a dedicated ‘Staff Technical Marketing Architect’ for all things End-User Computing (EUC) security, compliance & regulatory. He has over 20 years’ experience in the IT Industry, including the last 9 years within Public Sector realm, with roles spanning Cybersecurity, Networking, Enterprise Ops, Mobility & Telco solutions, encompassing numerous technologies and architectures. Andrew received an MIS (Management Information Systems) degree from University of Oklahoma with certs from ISC2 CISSP (Certified Information Systems Security Professional) & GIAC GSLC (GIAC Security Leadership Certification) and is based out of San Antonio, TX. He regularly contributes to VMware’s Tech Zone to provide more tailored messaging for Public Sector or Regulated Industry solutions from VMware EUC.
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware End-User-Computing Technical Marketing at euc_tech_content_feedback@vmware.com.
