Horizon on VMware Cloud on AWS Configuration
This chapter is one of a series that make up the VMware Workspace ONE and VMware Horizon Reference Architecture, a framework that provides guidance on the architecture, design considerations, and deployment of VMware Workspace ONE® and VMware Horizon® solutions. This chapter provides information about deployment and configuration of VMware Horizon on VMware Cloud on AWS. It is not intended to replace the product documentation, but to reference and supplement it with additional guidance.
Deploying Horizon on VMware Cloud on AWS
This chapter covers specific information for deploying and configuring Horizon on VMware Cloud on AWS. For more general information on deploying and configuring Horizon, see Horizon Configuration.
To deploy Horizon on VMware Cloud on AWS:
- Create an SDDC instance on VMware Cloud on AWS. See the VMware Cloud on AWS documentation.
- Deploy Horizon 8 or Horizon 7.5 or later on VMware Cloud on AWS.
- For more details on supported versions of Horizon on VMware Cloud on AWS, see VMware Interoperability Matrix.
- Check the knowledge base article 58539 for feature parity between Horizon on VMware Cloud on AWS and Horizon on-premises.
- See the Horizon product documentation for more information on Horizon.
- Set up the Horizon environment on VMware Cloud on AWS.
SDDC Preparation
Create an SDDC instance on VMware Cloud on AWS and set up the required networking. See the VMware Cloud on AWS documentation for more details.
Provision an SDDC
- Using a browser, go to https://vmc.vmware.com.
- Select Create SDDC and choose the region, deployment model, SDDC name, and number of hosts.
- When prompted, select your AWS account and the VPC and subnet to use with this SDDC.
- Define a management subnet for the vCenter Server, NSX Manager, and ESXi hosts.
- Finish by selecting Deploy SDDC.
Create Network Segments
Network segments can be added using the VMware Cloud admin console:
- View Details of the SDDC.
- Select Networking & Security > Network > Segments.
- Under Segment List, select Add Segment.
- Add segments for the following networks, defining a Segment Name and Subnet. The Type should be left as the default Routed.
- Add segments for External-DMZ, Internal-DMZ, Horizon-Management, VDI, and RDSH.
- For the VDI and RDSH segments, also launch and complete the Set DHCP Config wizard.
Other Networking Configuration
- Create security groups.
- Set firewall rules.
- Configure DNS.
- Request public IP addresses.
Create Resource Pools
Two vSphere resource groups are automatically created when the SDDC is created. It is recommended that the Compute-Resource Pool has child resource pools created in it to allow prioritization of the management servers and desktops/ RDS Hosts.
In the vSphere Client:
- Click Menu and select Hosts and Clusters.
- Browse to and expand vCenter > SDDC-Datacenter > Cluster-1 > Compute-ResourcePool.
- Right-click and select New Resource Pool.
- Create two new resource pools for Horizon-Management and Horizon-User.
See Managing Resource Pools for more information.
Window Server Template
To facilitate the creation of Windows servers for the various Horizon management components, either import an existing vSphere VM template or create a new VM and convert it to a template.
- Upload VM template or Windows Server ISO.
- Import customization specifications.
Horizon Deployment
When you set up the Horizon environment on VMware Cloud on AWS, you must install and configure the following components:
- Install Active Directory, DNS, DHCP, and KMS servers.
- Optionally, install RDS license servers.
- Install Horizon Connection Servers.
- Register the SDDC vCenter Server.
- Install Unified Access Gateway appliances.
Connection Server
With Horizon 8, when deploying the first Connection Server in the SDDC, make sure to choose AWS as the deployment type. This sets the proper configuration and permissions on the Connection Server and Virtual Center.
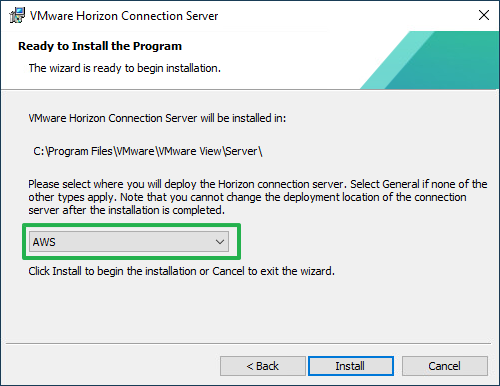
Figure 1: Choose the Horizon Deployment Location
Deploy the Connection Servers to the following locations:
- Folder = Workloads
- Compute resource = SDDC-Datacenter > Cluster-1 > Compute-ResourcePool > Horizon-Management
- Storage = WorkloadDatastore
Horizon 8 and Horizon 7.5 and later are supported on VMware Cloud on AWS. For details, see the Knowledge Base article: Horizon on VMware Cloud on AWS Support (58539).
vCenter Server
When registering the vCenter Server with the Horizon Connection Servers, use cloudadmin@vmc.local for the vCenter Server credential username.
If using a single-node vSphere cluster (usually for a proof of concept), you will need to modify the vSAN VM storage policies to “No data redundancy.” These policies are automatically created when the first desktop pool or RDS Farm is deployed.
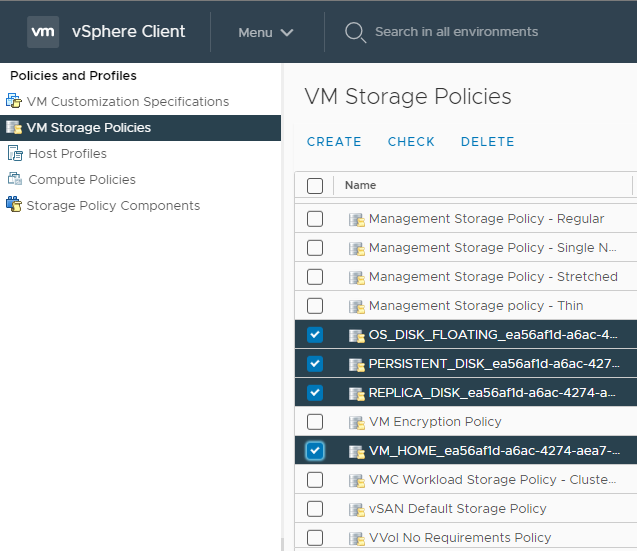
Figure 2: vSAN Storage Policies for Horizon
Unified Access Gateway
Deploy the Unified Access Gateway appliances and register them with the Connection Servers if your deployment supports remote users.
Deploy the Unified Access Gateway appliance to the following locations:
- Folder = Workloads
- Compute resource = SDDC-Datacenter > Cluster-1 > Compute-ResourcePool > Horizon-Management
- Storage = WorkloadDatastore
Use Unified Access Gateway version 3.3 or later.
Instant Clones
When you install and configure Horizon for instant clone for deployment on VMware Cloud on AWS, do the following:
- CBRC is not supported or needed on VMware Cloud on AWS. CBRC has been turned off by default.
- On the golden image VM, add the domain’s DNS to avoid customization failures.
When creating Horizon instant-clone pools on VMware Cloud on AWS, use the following settings in the provisioning wizard:
- Folder = Workloads
- Compute resource = SDDC-Datacenter > Cluster-1 > Compute-ResourcePool > Horizon-User
- Storage = WorkloadDatastore
Firewall Rules
The firewall service on VMware Cloud on AWS is based on NSX-T and provides both Distributed (Micro-segmentation) and Gateway Firewall Services.
To simplify the management of Gateway Firewall VMware recommend using Groups (located under Networking & Security -- Inventory) both for Compute and Management.
- Pre-create groups for your on-premises vSphere managements components, VDI components, and applications to be accessible from VMware Cloud on AWS.
- Do the same for VDI components deployed on VMware Cloud on AWS. Groups for vSphere management components are already pre-created by VMware. While creating a group, you need to specify IP addresses using CIDR notation.
- You can include a single host as a member by specifying /32 mask or a continuous range of IPs using relevant CIDR (such as /24 to include all IPs within a 24-bit subnet).
Note: Default behavior of both Management and Gateway Firewall is set to deny all traffic not explicitly enabled.
You can run the Firewall Rule Accelerator in VMware Cloud on AWS for all VPNs to create all the required firewall rules.
Management Gateway Firewall Rules
At minimum, you need to enable the traffic flow between the Horizon management components, such as the Connection Servers, and the SDDC provided vCenter and ESXi hosts in VMware Cloud on AWS.
Note: There are a predefined set of services that you can use while configuring rules for the Management Gateway Firewall. You cannot add or modify theses services. Each group (ESXi hosts, vCenter, and so on) has its own set of services.
You can achieve this by creating the following rules:
Table 1: Management Gateway Firewall Rules for Horizon Connectivity to vSphere
| Sources | Destinations | Services | Action | |
| ESXi Inbound | Horizon Management Servers | ESXi | Provisioning & Remote Console ICMP All VMware VMotion HTTPS | Allow |
| vCenter Inbound | Horizon Management Servers | vCenter | SSO ICMP ALL HTTPS | Allow |
Compute Gateway Firewall Rules
The Compute Gateway Firewall runs on the SDDC router (Tier 0) and provides firewalling for the Compute Gateway and the network segments defined on it. You will need a rule to allow Horizon connections into the External DMZ network segment and the Unified Access Gateways. You will also probably want to add a rule to allow the virtual desktops or published applications to access the internet.
Table 2: Compute Gateway Firewall Rules
| Name | Sources | Destinations | Services | Applied To | Action |
| External DMZ Inbound | Any | External-DMZ-Segment | HTTP HTTPS Blast PCoIP | Internet Interface | Allow |
| Outbound Internet Access | VDI-Segment Horizon Management-Segment | Any | HTTP HTTPS DNS DNS-UDP | Internet Interface | Allow |
Summary and Additional Resources
Now that you have come to the end of this Horizon on VMware Cloud on AWS configuration chapter, you can return to the landing page and use the tabs, search, or scroll to select your next chapter in one of the following sections:
- Overview chapters provide understanding of business drivers, use cases, and service definitions.
- Architecture chapters give design guidance on the products you are interested in including in your platform, including Workspace ONE UEM, Workspace ONE Access, Workspace ONE Assist, Workspace ONE Intelligence, Horizon Cloud Service, Horizon, App Volumes, Dynamic Environment Manager, and Unified Access Gateway.
- Integration chapters cover the integration of products, components, and services you need to create the platform capable of delivering the services that you want to deliver to your users.
- Configuration chapters provide reference for specific tasks as you build your platform, such as installation, deployment, and configuration processes for Workspace ONE, Horizon Cloud Service, Horizon, App Volumes, Dynamic Environment Management, and more.
Additional Resources
For more information about VMware Horizon on VMware Cloud on AWS, you can explore the following resources:
- VMware Horizon on VMware Cloud on AWS product page
- VMware Horizon on VMware Cloud on AWS documentation
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2023-07-25 |
|
Author and Contributors
This chapter was written by:
- Graeme Gordon is a Senior Staff End-User-Computing (EUC) Architect in End-User-Computing Technical Marketing, VMware.
- Hilko Lantinga is a Staff Engineer 2 in EUC R&D, VMware.
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware End-User-Computing Technical Marketing at euc_tech_content_feedback@vmware.com.
