CMMC Compliance: How to Secure End-Users and Endpoint with VMware EUC
Overview
Introduction
In this document, we will briefly review Cybersecurity Maturity Model Certification (CMMC) components and how VMware Workspace ONE End-User Computing (EUC) solutions can logically align to the National Institute of Standards & Technology (NIST) Special Publication (SP) 800-171 protecting Controlled Unclassified Information framework to provide a Defense Industrial Base (DIB) contractor/integrator/service provider (SP) (or A.K.A. GovCons) a roadmap to meet certification requirements.
The goal is to explain how the CMMC, a Federal mandate for DIB contractors (e.g., VMware itself <and> its DIB customers) can protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) against unauthorized access and disclosure while establishing a way to implement and maintain reasonable security processes and practices for an organization through use of VMware’s services. All of this is done in-line with the CMMC level 3 requirements (110 Practices and up to 60+ additional process & practices within the new 2.0 guidelines) for their unique enterprise for those with access needs to FCI & CUI.
This document will focus on now re-classified > CMMC Level 3 = Expert (see below), which is designated as the highest level of CMMC certification criteria based on the NIST SP 171. And as a general guideline, we will highlight those CMMC practices up to Level 3 against applicable VMware EUC products that would provide the capabilities within the suite to satisfy the controls for those practices.
Many of these CMMC practices are already deployed within numerous FedGov and private sector customers as on-prem solutions and are guided by controls aligned to 800-171 via National Information Assurance Partnership NIAP: VMware Product Compliant List. Some practices are included within VMware-hosted FedGov EUC solutions within GSA FedRAMP Marketplace for VMware. Finally, some are included within the DoD’s own DoD STIG for UEM - VMware Security Technical Implementation Guides (STIGs), which make up a customers’ ability to deploy, manage, and secure endpoints within an enterprise and how they may support the implementation of CMMC practices based on the 800-171 Controls that align to them.
In an update as of Nov 1st, 2021, the DoD has updated the levels. The “Advanced” level (formerly level 3) will be the equivalent to NIST SP 800-171. Similarly, the “Expert” level (formerly level 5) will be based on a subset of NIST SP 800-172 (Enhanced Security Requirements for Protecting CUI: Supplement to 800-171). If implemented, these proposed changes would align with many industries’ recommendation to leverage existing standards rather than introducing new ones. See the updated website for details.
Lastly, this overview is not meant to cover the recent Executive Order 14028 on Improving the Nation’s Cybersecurity, nor those specific enhancements targeted for the NIST Secure Software Development Framework (SSDF). Those are being addressed separately from this guidance as a part of VMware’s critical software & secure software development lifecycle model (SSDLC) and Security Development Lifecycle (SDL).
Audience
This document is intended for IT administrators and product evaluators who are familiar with VMware's Anywhere Workspace powered by EUC and VMware Workspace ONE. Familiarity with the End-User Computing environment and modern management that include device, app, and identity management is assumed. Knowledge of other technologies, such as VMware Horizon, Security, Secure Access Service Edge (SASE), and Zero Trust Architecture (ZTA) is also helpful.
Note: This document is only intended to provide a brief product capabilities guideline, which could be used when mapping to CMMC requirement areas and practices/controls. It is not intended to be specific or fully navigate readers through the entire CMMC accreditation process, for example, working with a third-party certified assessor for the Department of Defense’s supply-chain cybersecurity program or going through a Third-Party Assessment Organization(s) (3PAO)’s audit for full certification, and so on.
It is also not intended to provide mapping of other VMware solutions beyond the EUC arena. See the CMMC whitepaper for further VMware product analysis for the data center/network/boundary elements.
Cybersecurity Maturity Model Certification Overview
What is CMMC?
The DoD Cybersecurity Maturity Model Certification (CMMC) is the brainchild of the U.S. Department of Defense (DoD) in order to incorporate the existing National Institute of Standards & Technology (NIST) Special Publication (SP) 800-171 - Protecting Controlled Unclassified Information (CUI) in Non-Federal Systems framework, as well as guidance from CERT-Resiliency Management Model (C-RMM) into measurable requirements to vet the controls implemented through certification by an auditor.
Additionally, CMMC is a true tangible certification path for the companies that serve within the Defense Industrial Base (DIB), and it covers all DIB and the DoD / 4th estate Gov't Contractor(s) (GovCons). However, other FedGov agency groups, including Intel Community (IC) and Dept. of Homeland Security (DHS) & General Services Administration (GSA) are looking to incorporate the program into its acquisition and contracting vehicles as well. So, it will soon no longer be possible for a GovCon to ignore compliance or to claim a ‘self-attestation’ of compliance.
What is the goal of CMMC?
In concert with the NIST SP it is derived from, the goal is to protect FCI & CUI data that may reside on or pass-through non-government systems outside the direct control of federal / DoD purview and in use by contractually obligated DIB GovCons. CMMC compliance ensures that the minimum controls are in place to fend from foreign/nation-state actors and third-party malicious actors gaining access to these systems or the data on or passing through them.
Protecting the government’s Intellectual Property (IP) while in support of the supply chain is paramount. As has often been the case, past penetrations/exfiltration’s or cyber espionage activities originated from outside the government’s physical/ logical perimeters; rather, through these entities or affiliated GovCons, as was the case in recent high-profile SolarWinds or the previous Lockheed F-35 Joint Strike Fighter program breaches.
The NIST framework provides the foundations of Controls, referred to within the CMMC as Practices, to be the foundation of the certification criteria. CMMC's Accreditation Body (AB) (Update: Rebranded as of June 2022 as CyberAB) has a certification path for authorized third-party assessor organization (3PAO) assessors that will be performing audits and evaluation for CMMC. Registered Provider Organization (RPO) and their Registered Practitioner(s) (RPs) provide advice, consulting, and recommendations to their DIB clients prior to the audit. So, the auditor would assess those Practices that a DIB and potentially an RPO/RP had implemented for an entity’s certification against one of five escalating CMMC maturity levels, ranging from Basic > Advanced/Progressive Hygiene.
How do I define the data or systems to be inclusive or necessary to comply with CMMC?
The agency or branch in question would define what level and compliance/certification is necessary through the existing acquisition regulations under Defense Acquisition Regulations Supplement (DFARS) and specifically, clause 252.204-7012 which is defined under DFARS within Request for Proposals/ Information/ Quotes (for example, RFx's). Thus, the government agency/branch specifies this data, typically after their own security/compliance and the agency authorizing official leverages a process, such as the NIST Federal Information Processing Standards FIPS 199 for Security Categorization of Federal Information and Information Systems or the FIPS 140-2 Encryption Standards guides. After this classification audit and process is performed, the subsequent level of CMMC would be designated (for example, Levels 1>5).
CMMC Applicability & Function
The types of information to be protected will determine what levels of CMMC are required and contained within the RFx submission and compliance obligation of the responding organization and their subs. Thus, CMMC will be required of DoD contractors who process, store, or transmit federal contract information (FCI) which is CUI in nature, on behalf of the DoD. For each contract, the government must stipulate the CMMC level of protection based on the sensitivity of the information and the potential threat. Organizations must select and maintain a CMMC level that can be accomplished efficiently and cost-effectively.
At a minimum, contracts that involve FCI data will require CMMC Maturity Level 1 compliance, and contracts that involve CUI will require CMMC Maturity Level 2 or 3. CUI is data that is created or processed by, or on behalf of, the federal government. The National Archives CUI Registry organizes CUI data into 20 different data categories: Intelligence, critical infrastructure, financial, NATO-related, statistical, legal, defense, export control, tax, and so on.
The CMMC Advisory Board Accreditation Body (AB) recognizes that not all contractors will store, process, or transmit equally sensitive data. Therefore, the CMMC model is based on this multi-tiered approach to allow a more cost-effective opportunity for smaller businesses to support contracts at a lower CMMC Level for contractors that handle data with lower sensitivity.
The CMMC model has 17 domains. Each domain outlines specific processes, capabilities, and practices. Figure 1 describes the relationship between these key terminologies.
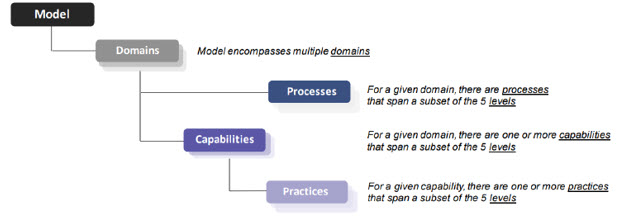
Figure 1: CMMC Model Framework (Simplified Hierarchical View)
As previously mentioned, each CMMC level comprises its own practices and those of the levels below it. For example, Level 2 requires all practices from Levels 1 an additional 93. Level 3 is cumulative and requires all 110 practices found in Levels 1 & 2, plus an additional TBD practice (see Figure 2) of the previous CMMCv1 Levels 4 & 5, which could be as many as another 50+ practice controls. So, to achieve an audit and certification for CMMC, each of those level’s controls must both be shown to be ‘implemented’ and ‘in-practice’ from a historical standpoint (this latter point has been a challenge and under discussion and review as of writing and CMMC 2.0 has new updated targeted language around Plan of Actions & Milestones (POA&M)). This will provide for accommodations of gaps identified for future closure during audit discovery.
CMMC 2.0 Update
In an update as of Nov 4th, 2021, DoD Strategic Direction for (CMMC) Program 2.0 - Press Release, the DoD is no longer intending to approve inclusion of a CMMC requirement in any near-term contract, prior to completion of the CMMC 2.0 rulemaking process and will suspend all current trialling phases. When CMMC 2.0 is fully authorized through the rulemaking process, the DoD will require a certain set of companies, based on contract assignments to adhere to the revised CMMC framework, as well as according to requirements set forth in regulation and that rulemaking process. The timeline of which could take between 9-24 months.
Additional highlights form the 2.0 announcement / update:
- The DoD has reduced the levels for the model down from (5) to (3) and provided clarity to their alignment:
- “Advanced” level (formerly level 3) will be the equivalent to NIST SP 800-171 ‘Protecting CUI’.
- Similarly, the “Expert” level (formerly level 5) will be based on a subset of NIST SP 800-172 (Enhanced Security Requirements for Protecting CUI: Supplement to 800-171) but is still under development.
- Finally, the “Functional” level (Formerly Level 1 – Basic) would be based on the contractor ‘annual self-audit’ for the 17 practices.
- If implemented, these proposed changes would align with many of the industry’s recommendations previously made to leverage existing standards rather than introduce new ones ex. FISMA / FedRAMP and the hopeful ‘reciprocity’ inclusion of those standards in favor of complying with a segmented CMMC on top of those existing accreditations etc.
- Levels 2 & 4 will be removed from the 2.0 version and no longer be a consideration or tracked (see below):
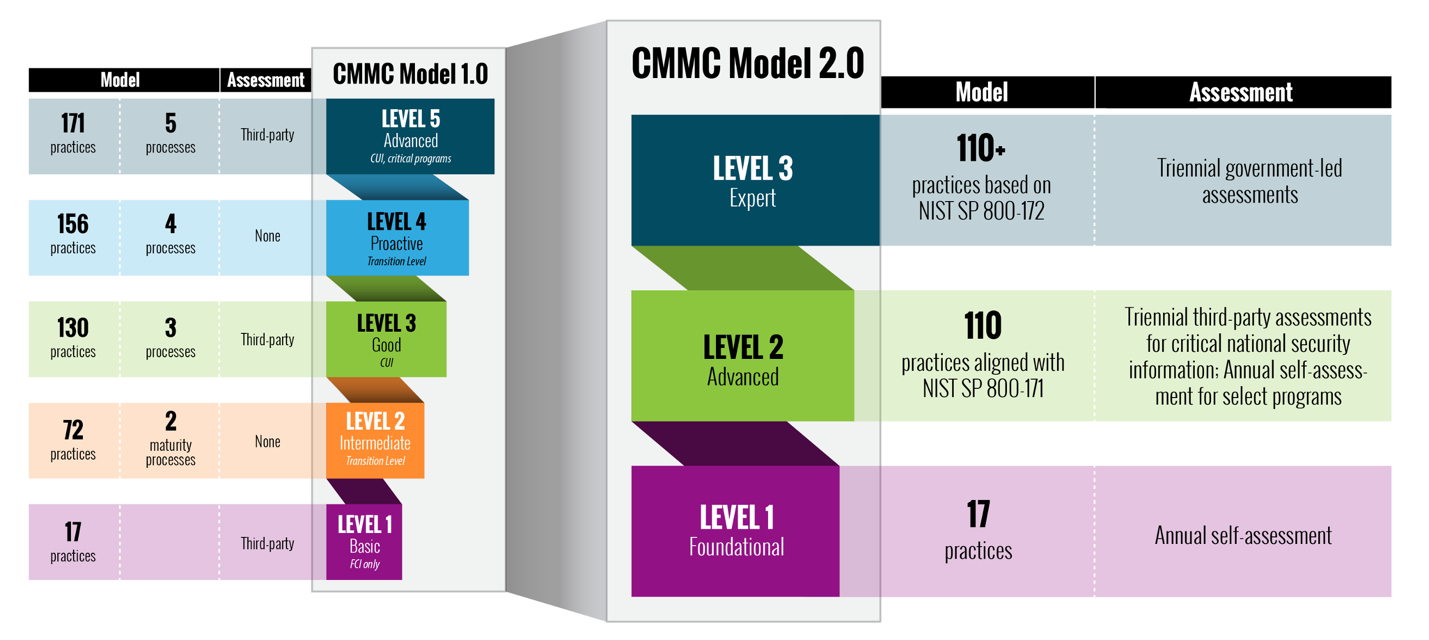
Figure 2: CMMC Practices Per Level and mapping from model version 1.0 to 2.0
For more details, see:
The CMMC model addresses the following 17 security domains, 14 of which are derived from the NIST FIPS Pub 200 and NIST 800-171, as well as 3 additional new control domains represented in Table 1:
| Access Control (AC) | Asset Mgt. (AM) * | Audit & Accountability (AU) |
| Awareness & Training (AT) | Config Mgt. (CM) | Identification & Auth (IA) |
| Incident Response (IR) | Maintenance (MA) | Media Protection (MP) |
| Personnel Security (PS) | Physical Security (PE) | Recovery (RE) * |
| Risk Management (RM) | Security Assessment (CA) | Situational Awareness (SA) * |
| Sys Comm Protection (SC) | Sys & Info Integrity (SI) | Key: * denotes new control family for CMMC |
Table 1: 17 Security Domains of CMMC
These control families are based largely on the existing NIST SP 800-171 framework but add an additional three control families, which include Asset Management (AM), Recovery (RE), and Situational Awareness (SA). At Level 3, the CMMC model encompasses all 110 security requirements defined in NIST SP 800-171 and 20 additional controls. Capabilities are core system or program requirements that must be possible within the system. There are 43 CMMC capabilities across the 17 domains of the CMMC model.
For these additional controls and for the controls found in Levels 4 and 5, CMMC incorporated key practices and processes from other standards and references such as NIST SP 800-53, Aerospace Industries Association (AIA) - National Aerospace Standard (NAS) 9933 “Critical Security Controls for Effective Capability in Cyber Defense”, and Computer Emergency Response Team (CERT) Resilience Management Model (RMM) v1.2. Table 2 shows the primary source frameworks for all CMMC controls by level.
| CMMC Levels (v1.0 & v2.0) | NIST 800-171 Requirements | Total Requirements |
| Level 1 (2.0 = Foundational) | 17 | 17 |
| Level 2 (2.0 = Expert) | 110 | 110 |
| Level 3 (2.0 = Advanced) | 110 | 110+ (*) |
| Level 4 (Deprecated in 2.0) | 110 | 156 |
| Level 5 (Deprecated in 2.0) | 110 | 171 |
Table 2: CMMC Source Framework for Controls by Level (Legacy v1.0 vs. 2.0); Note (*) could represent the additional 61 practice controls previously aligned with Level’s 4 & 5 of CMMC v1.0 depending on the Audit requirements
Key CMMC Deployment Considerations
To reach Level 3, GovCons should gauge some key considerations before an audit, such as existing solutions and tools in the IT architecture to create a baseline and what needs to be augmented. In practical terms, there are 5 areas of focus to consider prior to an audit, to ensure whether an organization has an existing investment in the appropriate areas for protecting CUI data:
- Data: Ensure that both the data and all the elements, for example, network, servers, email, databases storing and routing the CUI data are secured, based on the different control groups within CMMC / 800-171 (for example, Access Controls (AC)).
- Other areas should include document marking, Data-at-Rest (DaR) and Data-in-Transit (DiT) encryption of data, as well as DNS filtering, and Intrusion Prevention/Detection solutions to help protect sensitive information under the terms of CUI and so on.
- Conditional access policy enforcement and robust cloud-based content management to both the data and the apps, securely via any device, anywhere.
- Cloud: Using secure cloud solutions can help to enclave and containerize the CUI data, including the tools within those environments to manage and deploy to the end-users; so, a firm can provide the segmentation from the rest of the company’s operations necessary to lower the attack surface and provide for customized controls that correlate to the practices necessary to achieve certification for CMMC.
- Leveraging existing accredited cloud solutions, which have already laid the groundwork for 800-171 compliance, such as General Services Administration (GSA) Federal Risk & Management Program (FedRAMP) authorized Infrastructure-as-a-Service (IaaS) and Software-as-a-Service (SaaS), can jumpstart that compliance.
- Endpoints: Company-owned tools, including mobile-enabled, desktops, laptops and cloud-based apps must ensure there are clear policies governing their access and use. Device & App Management solutions are paramount to ensuring that they are and provide the flexibility to cover the large use cases associated with them.
- End-users: A company’s greatest assets are unfortunately often its greatest weakness; the system’s end-users themselves. Not only are the aforementioned tools important, so too is continuous training, education, and auditing within the entire end-user’s environment.
- Identity: Lastly, providing for automation of Identity Management and access to and through the devices or apps is paramount to not only a good end-user experience (UX) but also to integrate with DoD 2-Factor Authentication (2fA)/Multi-factor Authentication (MFA) mandates, including Common Access Card (CAC) use through Personal Identity Verification (PIV)-D (Derived Credentials).
An additional area to consider, prior to any formal engagement, is potentially leveraging existing or previous assessments or compliance in other arenas to have likely provided a baseline or comparable framework. For example, ISO 27001 or PCI or even engaging a Registered Provider Organization (RPO) firm who specializes in CMMC assessments may be worthwhile, as opposed to going at it alone.
But if a GovCon does so, there are other great resources to review to help ensure that these and other elements of a GovCon’s environment is ready for an official audit. These resources include the CMMC’s own assessment guides (Levels 1 & 3 are currently available as of publication).
Workspace ONE Solution
The VMware EUC product portfolio is made up of Workspace ONE, a digital platform that delivers Unified Endpoint Management (UEM) for most end-user device types, and provides device, application, content/end-user experience management, an app store/catalog, and identity & access management (IdM/IAM), as well as an integrated service to provide access controls, application management, single sign-on (SSO), data loss prevention (DLP), securing browsing, conditional access, and multi-platform endpoint management.
The existing portfolio of VMware EUC solutions have been certified under GSA’s FedRAMP program which complies with Federal Information Security Modernization Act (FISMA) and NIST’s corresponding SP 800-53, a predecessor and more involved set of controls, which SP 800-171 is based on. And although as of this writing, reciprocity for leveraging this existing accreditation path in lieu of a 3PAO separately has not yet been expressly ruled on by the CMMC-AB, it is anticipated in numerous discussions and forums that a pass-through of FedRAMP Moderate IL2 will equate to the CMMC Level 3.
Thus, as an existing or future government contractor with DoD data representative of Level 3, the VMware Authorized FedRAMP environment and deployment architecture can be used by the DIB customer to deploy the same security controls within that architecture to enable the appropriate Practices represented in the control groups defined under NIST SP 800-53 and map them to SP 800-171 / CMMC framework for certification baselining.
Workspace ONE is built on VMware's Workspace ONE UEM technology that provides for the standard aspects of Mobile Device Management (MDM), Mobile App Mgt (MAM), including App Storefront (MAS) and integrates with virtual application delivery via VMware Horizon on a common identity framework, including:
- PIV-D is delivered by VMware Workspace ONE Access for identity management (IdM), as well as simple application access for end-users, a Self-service Appstore, an enterprise-grade single sign-on (SSO), conditional access enforcement policies and lastly, productivity tools.
- The platform enables IT to deliver a digital workspace that includes the devices and apps of the business's choice through Workspace ONE Intelligent Hub (Intel Hub) Services, without sacrificing the security and control that IT professionals need while implementing key security controls, such as encrypting data both at-rest and in-transit with Tunnel and secure apps such as Workspace ONE Boxer E-Mail, while providing data isolation and containerization and user group segmentation. The Content Management aspects also provides agencies under the VMware Workspace ONE Content app the ability to enable end-users to access managed content within configured, controlled parameters and policies.
- A robust Workspace ONE Intelligence service aggregates and correlates data from multiple sources to give complete visibility into the entire environment and produces the insights and data that will allow you to make the right decisions for your Workspace ONE deployment, leveraging its built-in automation engine that can create rules to take automatic action on security issues.
- VMware EUC provides for a secure VDI deployment in the Workspace ONE Horizon Service, leveraging a multi-tenant, cloud-scale architecture to enable administrators to deploy virtual desktops and applications across public and private clouds.
Additional support tools for VMware EUC include:
- Workspace ONE Assist enables IT and help desk staff to remotely support employees with device tasks and issues, directly from the Workspace ONE console. When integrating with Workspace ONE Unified Endpoint Management (UEM), it provides remote access and troubleshooting capabilities to physical devices through the Workspace ONE UEM administrator console, and with VMware Horizon Cloud Control Plane it provides a real-time remote employee support solution specifically designed for Horizon customers with virtual desktop deployments.
- And lastly, Workspace ONE Mobile Threat Defense (MTD) is an embedded MTD agent within the Hub client providing a single source for on-device, truly integrated and automated endpoint protection for mobile-enabled devices for a true Zero Trust security for the device, the data it's accessing through applications and phishing detection.

WS1 = UEM + Access + Hub Services + Intelligence + Assist + MTD + Horizon
Figure 3: EUC Portfolio Logical View with Product Links
Today’s technology infrastructure is complex; VMware products aim to simplify that infrastructure and develop a more secure environment for customers. VMware’s approach to enabling them to meet regulatory controls includes compliance kits, validation of capabilities, and VMware products’ ability to meet compliancy requirements (for example, GSA FedRAMP & Management Program – FedRAMP), as well as producing a framework focused on assembling products to a holistic compliance solution. This same enablement can be leveraged by DIBs to address the practice control groups for CMMC.
VMware prioritizes data protection and system security within an enterprise through Workspace ONE and its core components. The framework incorporates both EUC and cloud-hosted product capabilities to enable a customer to perform CMMC controls required for compliance product capabilities and leverage those existing NIST SP 800-53 & 171 as their foundational security framework to create a series of standards and baselines. These are broadly illustrated in Table 3:
|
CMMC Practice Control |
MTD |
||||||
|
Access Control (AC) |
✅ |
✅ |
✅ |
✅ |
✅ |
|
✅ |
|
Asset Mgt. (AM) * |
✅ |
|
✅ |
|
|
✅ |
✅ |
|
Awareness & Training (AT) |
✅ |
|
|
✅ |
|
✅ |
✅ |
|
Audit & Accountability (AU) |
✅ |
|
✅ |
✅ |
|
|
✅ |
|
Config Mgt. (CM) |
✅ |
|
|
✅ |
|
✅ |
✅ |
|
Identification & Auth (IA) |
✅ |
✅ |
✅ |
|
|
|
|
|
Incident Response (IR) |
✅ |
|
✅ |
✅ |
|
✅ |
✅ |
|
Maintenance (MA) |
✅ |
|
✅ |
✅ |
|
✅ |
✅ |
|
Media Protection (MP) |
✅ |
✅ |
|
|
|
|
✅ |
|
Personnel Security (PS) |
✅ |
✅ |
✅ |
|
|
|
✅ |
|
Physical Security (PE) |
✅ |
✅ |
|
|
|
|
✅ |
|
Recovery (RE) * |
✅ |
✅ |
✅ |
✅ |
✅ |
✅ |
|
|
Risk Management (RM) |
✅ |
|
✅ |
|
|
|
✅ |
|
Security Assessment (CA) |
✅ |
✅ |
✅ |
✅ |
|
|
✅ |
|
Situational Awareness (SA) * |
✅ |
✅ |
✅ |
|
|
|
✅ |
|
Sys Comm Protection (SC) |
✅ |
✅ |
|
|
|
|
✅ |
|
Sys & Info Integrity (SI) |
✅ |
✅ |
✅ |
|
✅ |
|
✅ |
Table 3: CMMC Security Domain Mapping to VMware EUC
Table 4 contains a service description of each of VMware’s EUC compliance utilities per Practice Control and some additional associated material links in addition the ‘Product Release Notes’ in linked in Table 3 for reference to VMware’s Workspace ONE solution enablement for the CMMC practice controls.
Table 4: CMMC Security Domain Mapping to VMware EUC Service References
VMware’s CMMC
Although there is no single vendor solution that can achieve compliance with the still evolving CMMC model, and all 110+ security practice requirements, there is however practical ways to incorporate VMware’s EUC suite of solutions, as represented above, along with a GovCons strategy of the use of existing services and tools that can guarantee long-term success.
By effectively taking into consideration the deployment and integration of VMware’s Workspace ONE service, especially when coupled to our FedRAMP environment controls and security architecture practices, a customer can take great strides, prior to any formal assessment to ensure that the data is being hosted, managed, and controlled properly regarding SP 800-171 and the CMMC mandate and provide CMMC implementation solutions by:
- Identifying CUI/FCI data within existing environments and within new engagements
- Scoping for the necessary solution elements of your SP 800-171 compliance efforts, and protecting the CUI / FCI data in the discovery phase or identified in the DFARS contract language
- Helping pre and post assessment discovery gaps by having solutions in place to mitigate the practice areas
- Step-by-step guide for Supplier Performance Risk System (SPRS) submittal
- Ensuring a service solution that enables an audit-ready System Security Plan (SSP) draft and Plan of Action & Milestones (POA&M) that can help close gaps after post audit from within the POA&M
- Strategically address implementation and manage compliance for endpoints, the data they access and where that data is being housed e.g., multi-cloud
Lastly, VMware is committed to supporting government IT programs and the extended ecosystem / supply chain worldwide as is the case for CMMC and we continue to expand our compliance programs to meet the requirements of the most demanding missions. For more information on VMware compliance, see the following:
- GSA FedRAMP Marketplace - VMware
- VMware Federal Certifications
- VMware Product Certifications & Public Testing
- VMware Boxer - Only NIAP Accredited App for Email
- VMware's NCSC 14 Cloud Security Principles Guide
- Workspace ONE Cloud Services Achieve ISO 27001, ISO 27017, and ISO 27018 Certifications
Subscribe and look for our enhanced tutorial and design considerations guideline on Digital Workspace Tech Zone that will be made available later this summer/fall as the final CMMC regulation details are ratified by the DoD and implemented into the program.
Additional Resources
For supporting documentation, explore the following resources:
- VMware Workspace ONE: Suite Documentation
- Workspace ONE Resource Portal
- Tech Zone: WSO-UEM-Configuration
- Tech Zone: Mastering Horizon VDI
- Tech Zone: Getting Started with WSO Intel Reports & Dashboards
- Tech Zone: Unified Access Gateway Architecture
- Tech Zone: Dynamic Environment Manager Architecture
- Tech Zone: WSO Tunnel Tutorial
- Tech Zone: UEM Platform Integration Guide
- Tech Zone: EUC Service Integration
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2022/06/23 |
|
| 2021/11/11 |
|
| 2021/06/02 |
|
About the Author
Andrew Osborn is serving in a role at VMware as a dedicated ‘Staff Technical Marketing Architect’ for all things End-User Computing (EUC) compliance / regulatory. He has over 20 years’ experience in the IT Industry, including the last 8 years within Public Sector, with roles spanning Cybersecurity, Networking, Enterprise Ops, Mobility & Telco solutions, encompassing numerous technologies and architectures. Andrew received an MIS degree from University of Oklahoma with certs from ISC2 CISSP & GIAC GSLC and is based out of San Antonio, TX. He'll be contributing to VMware’s Tech Zone to provide more tailored messaging for Federal, State, Local & Education (SLED) solutions from VMware EUC.
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware End-User-Computing Technical Marketing at euc_tech_content_feedback@vmware.com.
