[Technical Blueprint] Windows 10 Co-Management with SCCM & Workspace ONE

For many SCCM admins, the path to modern management for Windows 10 remains unclear or appears overly complex. To demystify this path, today’s post lays out an approach known as co-management. Co-management allows Workspace ONE to co-exist alongside current PCLM tools, such as SCCM. Keep reading to learn about the co-management capabilities that exist today in Workspace ONE, and to access links to helpful resources and tools.
For information about next-gen co-management capabilities, check out the blog Accelerate and Simplify Your Transition to Modern Management for Windows 10.
Ways to Approach Co-Management
While there are many approaches to co-management, most can be broken into one of three categories: complement, transition, or transform. The image below describes each approach and their distinguishing characteristics.
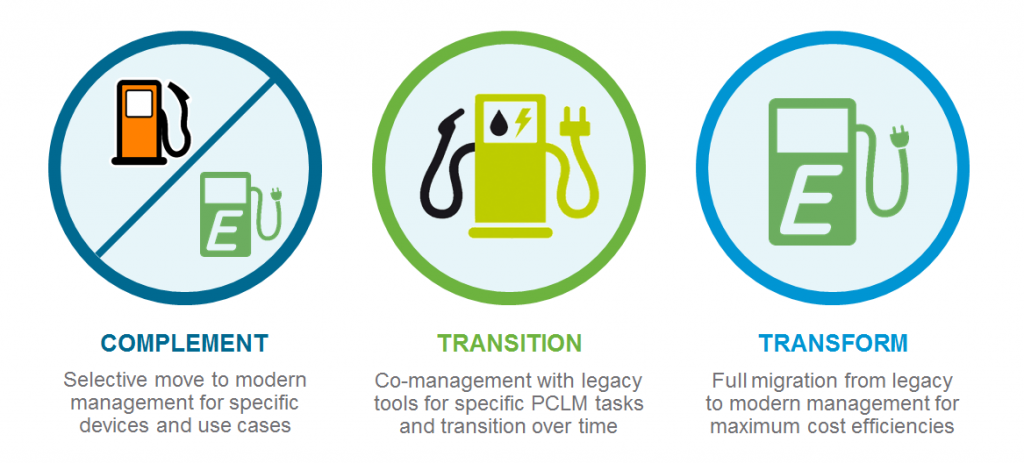
All three approaches apply to current as well as popular prior versions of SCCM (pre-1710) and Windows 10 (pre-1709).
Co-Management for SCCM Admins
For SCCM administrators interested in Workspace ONE’s modern management capabilities, getting started can be overwhelming. To simplify the process, we’ve provided resources tailored to SCCM admins.
- SCCM Admin Resources
-
SCCM to Workspace ONE Translations
The following table “translates” common SCCM terms and concepts into Workspace ONE terminology.
SCCM Terms Workspace ONE Translations WMI/MOF CSPs/Profiles Apps & Packages Software Distribution & Product Provisioning Distribution Points (DPs) + BranchCache CDN + Peer-to-Peer (P2P) MDT/OSD OOBE/AutoPilot/Dell Cloud Provisioning Software Center/App Catalog/Company Portal Workspace ONE Catalog MBAM for Encryption BitLocker Lifecycle Management Collections Smart Groups & Assignment Groups Software Updates/ADRs/WSUS Windows Update Profile Task Sequences Product Provisioning Site Code & Assigned Site Group ID & Enrollment Group Enrollment Point/Enrollment Proxy Point Device Services (Mobile and Mac Devices Only) Management Point Device Services (Windows Devices) Primary Site/Secondary Site Parent/Child Organization Group Hands-On Labs
The best place to learn about Workspace ONE and AirWatch Unified Endpoint Management, is in an immersive hands-on lab. Since the labs are free, and don’t require additional infrastructure, they provide a low-stakes way to see what the product can do and how it works.
VMware TestDrive
Another great resource at your disposal is TestDrive. TestDrive is a fully featured, integrated and globally available demo environment provided by VMware for partners, customers and employees. Sign up for your TestDrive account and check out some awesome demos created using TestDrive.
Getting Started with Co-Management
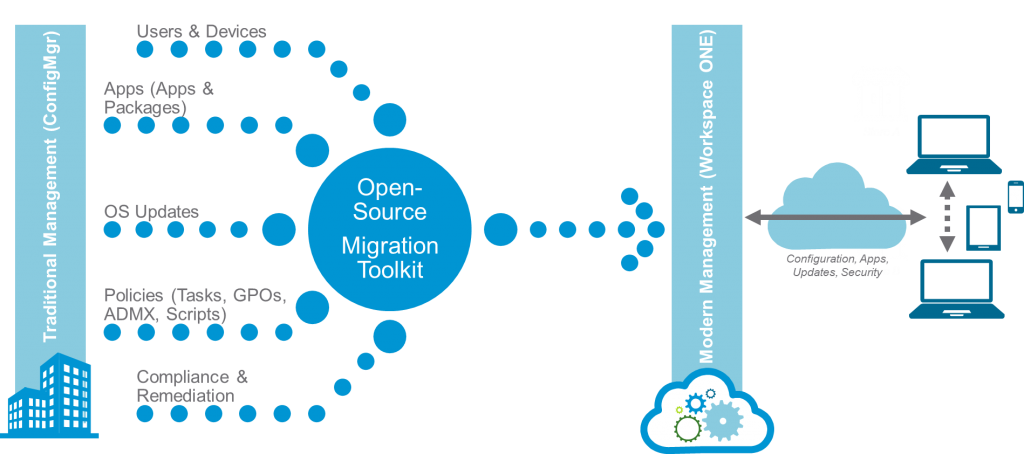
Create the foundation for co-management by migrating devices with user mappings from SCCM to Workspace ONE. Then, use VMware’s open-source toolkit to migrate workloads.
The following diagram overviews the steps involved in establishing co-management.