Cybersecurity Journey to Zero Trust - 1
How has Cybersecurity failed us and why do we need yet another framework to follow?
Cybersecurity from its infancy was inherited from a network standpoint, thus it was always designed under a lock-and-key, moat around the castle mentality. The focus of which was perimeter defenses put in place to ensure that external ‘malicious actors’ were kept at bay by them. Or worst case, all those defenses put together would at the very least provide security by obscurity or make the target appear less attractive to an opponent, e.g., the herd mentality = the ‘illusion’ that an organization didn’t have to be the fastest prey on the Serengeti, just faster than their peer(s)!
But that began changing by the 2010 timeframe, when time and time again those actors became more sophisticated, more driven to extract ‘valuable treasure-troves’ of data/information rather than simply hijinks or acts of mischief, and were now state-backed or ‘nation-state’ sponsored. With the continued reliance on foreign software/hardware or simply the developmental/acquisition supply chain, it became increasingly noticeable that perimeter defenses would not work against driven adversaries, who often were leveraging compromised systems from those provisional asset pools, thus seemingly having a backdoor around those defenses and worse, appear to be valid systems/users and traffic!
Watch our video series Cybersecurity Journey to Zero Trust: Episode 1 and follow along as we cover the basics of Zero Trust.
What Zero Trust Is:
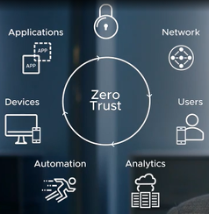
- Zero Trust provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.
- Zero Trust Architecture (ZTA) is an enterprise’s cybersecurity plan that uses zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero-trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a ZTA plan.
- Ref. NIST SP 800-207: ZTA 2020: NIST SP 800-207 - ZTA Guide – PDF Download

And … what Zero Trust IS NOT:
Myth 1 - That Zero Trust can be achieved for any infrastructure or application
- Zero trust presents a shift from a location-centric model to a more data-centric approach for fine-grained security controls between users, systems, data and assets that change over time; for these reasons, moving to a ZTA is non-trivial.
- This provides the visibility needed to support the development, implementation, enforcement, and evolution of security policies. More fundamentally, zero trust may require a change in an organization’s philosophy and culture around cybersecurity.
- “The path to zero trust is a journey that will take years to implement.”
- Ref. CISA Zero Trust Maturity Model: CISA ZT Maturity Model Draft - PDF Download
Myth 2 - That Zero Trust is just Least Privilege updated
- Although Zero Trust certainly requires granular (container, service, app) enforcement of least privilege, it is completely insufficient to realize the resilience to supply chain and ransomware attacks that conformant Zero Trust promises.
- Zero Trust also requires:
- Least functionality
- Continuous enforcement – real-time and inline
- Continuous verification of conventional security assertions (authentication, integrity, …)
- Ref. Implementing Zero Trust, NCCoE: NIST NCCoE ZTA Project - Standards-based Implementation Cybersecurity Guide - PDF Download
Myth 3 - That Zero Trust can be realized by implementing it at end-user platform, the workload platform or the gateway, alone
- “Zero Trust is an assumed breach security model that is meant to guide cybersecurity architects, integrators, and implementers in integrating disparate but related cybersecurity capabilities into a cohesive engine for cybersecurity decision-making. However, to be fully effective, Zero Trust principles need to permeate most aspects of the network and its operations ecosystem to minimize risk and enable robust and timely responses.”
- “Architect from the inside out – First, focus on protecting critical DAAS. Second, secure all paths to access them.”
- “Determine who/what needs access to the Data, Assets, Applications, and Services to create access control policies – Create security policies and apply them consistently across all environments (LAN, WAN, endpoint, perimeter, mobile, etc.).”
- Embracing a Zero Trust Security Model, NSA Ref. (page 3) Defense.gov - Embracing ZT Security Model PDF Download
Myth 4 - That the requirements of the Executive Order-14028 mandate immediate implementation of Zero Trust
- The current requirements are to demonstrate progress along the complex and disruptive journey toward ZT
- Page 2 -Transitioning to a zero-trust architecture will not be a quick or easy task for an enterprise as complex and technologically diverse as the Federal Government. But as President Biden stated in EO 14028, “Incremental improvements will not give us the security we need; instead, the Federal Government needs to make bold changes and significant investments in order to defend the vital institutions that underpin the American way of life.”
- Examples of actually required near term actions by agencies in moving toward Zero Trust:
- Identify all authorized users and their intended access.
- Segment networks around applications (not collections of applications, not security posture zones)
- Reach maturity level 1 (IL1) logging requirements (M 21-31)
- Operate dedicated application security testing programs
- Inventory all assets, including all cloud and IoT assets, establishing pervasive monitoring
- Avoid the use of privileged software agents wherever possible (presumed compromise) page 10
Note: All of these are prerequisites to formulating Zero Trust Policies, and implementing Zero Trust
- Ref. Moving the U.S. Government Towards Zero Trust Cybersecurity Principles - Zero Trust Cyber.gov - PDF Download
*** Don’t Miss out on our follow-on Journey sessions, including Episode 2! ***
Additional Resources
And for further Zero-Trust assets on Tech Zone, see:
Zero Trust Regulation & Framework Executive Summary
Incorporating VMware Zero-Trust for the Presidential Executive Order
VMware's TechZone Zero Trust Cybersecurity Portal
